Preface: The Cortex-M stands for the Microcontroller which is used in most of our daily life applications also starting from the automation to DSP applications, sensors, smart displays, IoT applications ,etc.
Background: In April of 2024, Arm Limited published a Cortex-M Security Extensions (CMSE) Security Bulletin that identifies a potential software security issue in code that uses CMSE. The security vulnerability allows an attacker to pass out-of-range values to code executing in Secure state to cause incorrect operation in Secure state. This security vulnerability is present in compilers that are not compliant with version 1.4 of the Arm v8-M Security Extensions Requirements on Development Tools.
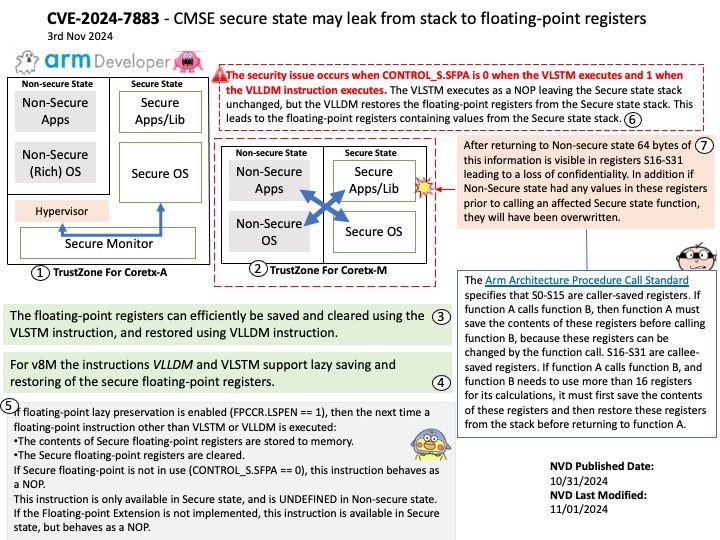
Vulnerability details: When using Arm Cortex-M Security Extensions (CMSE), Secure stack contents can be leaked to Non-secure state via floating-point registers when a Secure to Non-secure function call is made that returns a floating-point value and when this is the first use of floating-point since entering Secure state. This allows an attacker to read a limited quantity of Secure stack contents with an impact on confidentiality. This issue is specific to code generated using LLVM-based compilers.
LLVM and the GNU Compiler Collection (GCC) are both compilers. The difference is that GCC supports a number of programming languages while LLVM isn’t a compiler for any given language. LLVM is a framework to generate object code from any kind of source code.
Official announcement: For more information about the vulnerability, please see the link –
https://nvd.nist.gov/vuln/detail/CVE-2024-7883
https://developer.arm.com/Arm%20Security%20Center/Cortex-M%20Security%20Extensions%20Vulnerability