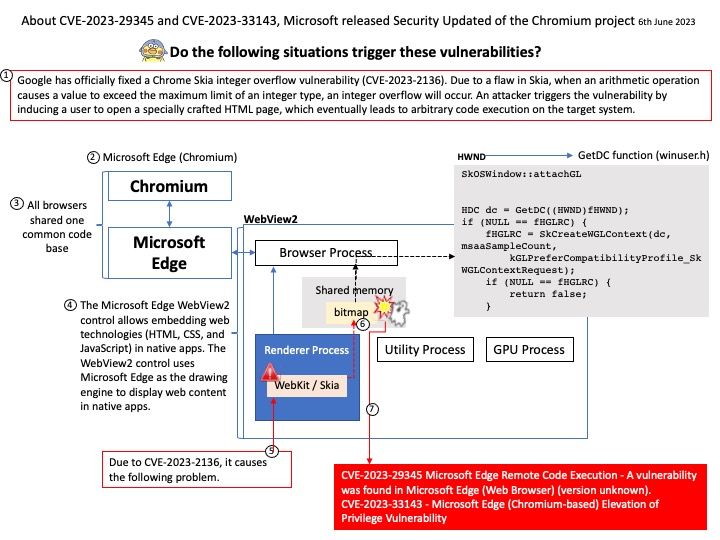
Preface: Samsung said that Open Source is not only the development method also a culture and various things. Samsung always keep in mind to give back to Open Source through their activities. They are partake in the culture of sharing and collaboration with the list of projects they have released and contributed to.
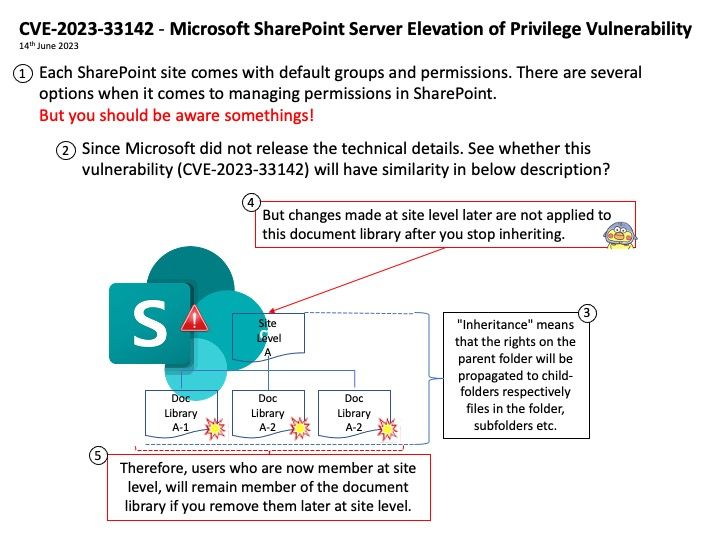
Background: The IoT.js platform uses JerryScript to run JavaScript code and libuv for asynchronous I/O, and enables developers to create IoT services that communicate with each other and the outside world.
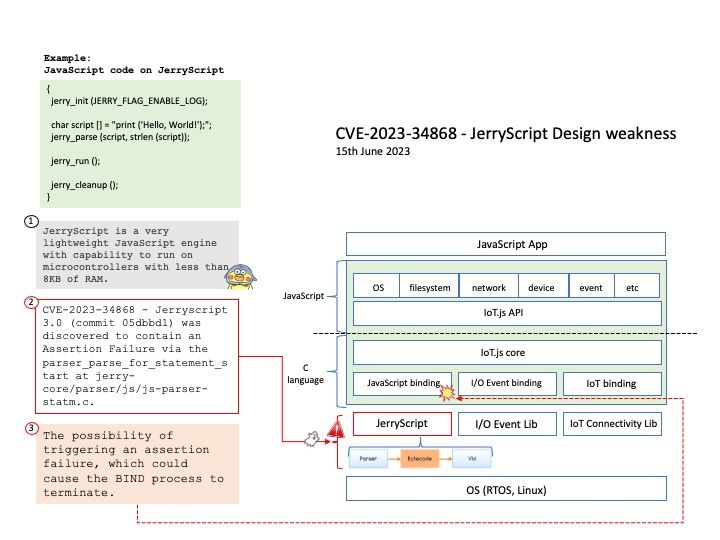
JerryScript is a very lightweight JavaScript engine with capability to run on microcontrollers with less than 8KB of RAM.
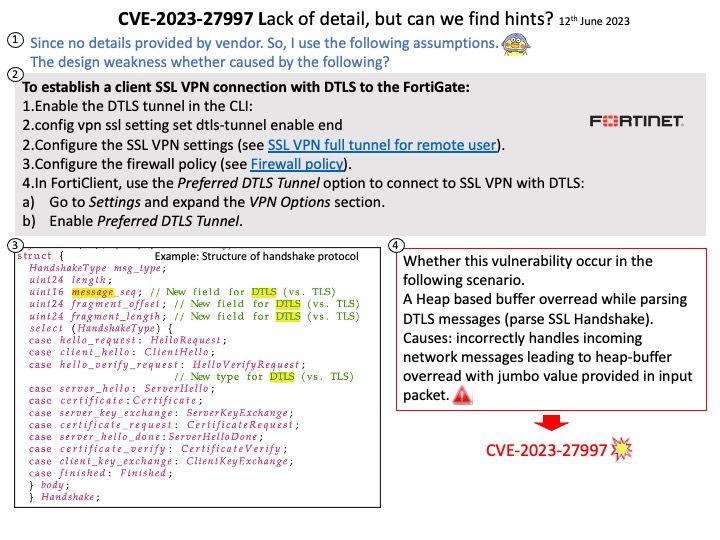
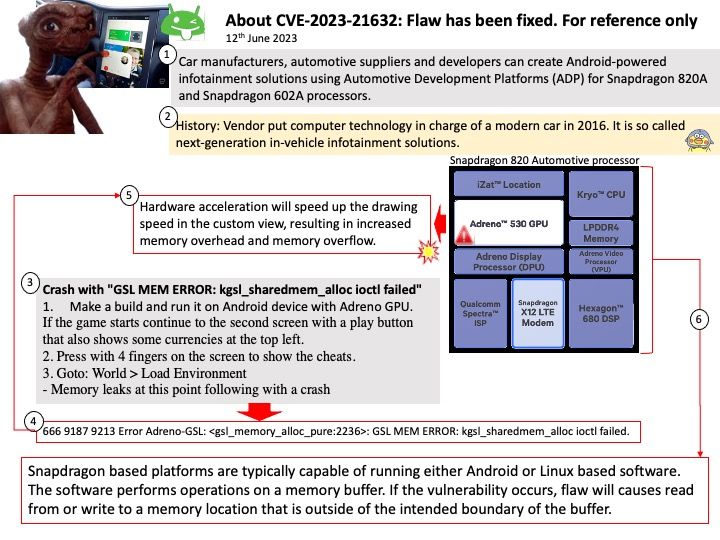
Vulnerability details:
CVE-2023-34868 – Jerryscript 3.0 (commit 05dbbd1) was discovered to contain an Assertion Failure via the parser_parse_for_statement_start at jerry-core[/]parser[/]js[/]js-parser-statm[.]c.
My Predcit Consequence: The possibility of triggering an assertion failure, which could cause the BIND process to terminate.
Reference: https://nvd.nist.gov/vuln/detail/CVE-2023-34868
In addition there is another one.
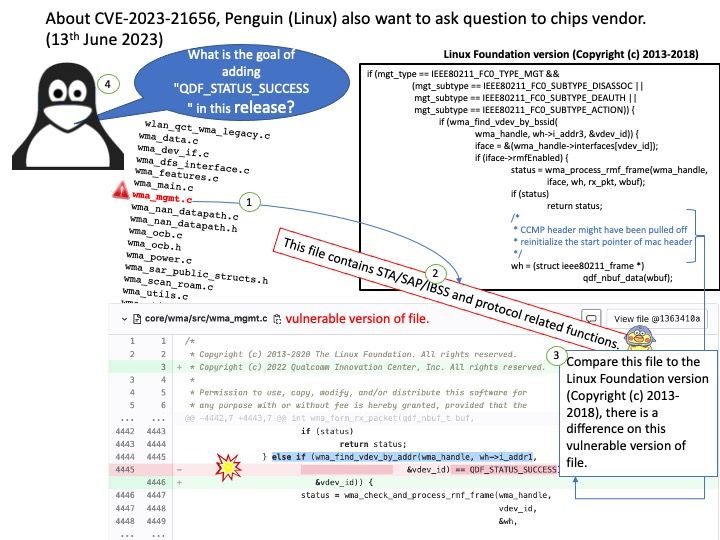
CVE-2023-34867 – Jerryscript 3.0 (commit 05dbbd1) was discovered to contain an Assertion Failure via the ecma_property_hashmap_create at jerry-core[/]ecma[/]base[/]ecma-property-hashmap[.]c.
Reference: https://nvd.nist.gov/vuln/detail/CVE-2023-34867