Preface: Use-After-Free (UAF) is a vulnerability related to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program.
Background: Btrfs provides a clone operation that atomically creates a copy-on-write snapshot of a file. Such cloned files are sometimes referred to as reflinks, in light of the proposed associated Linux kernel system call.
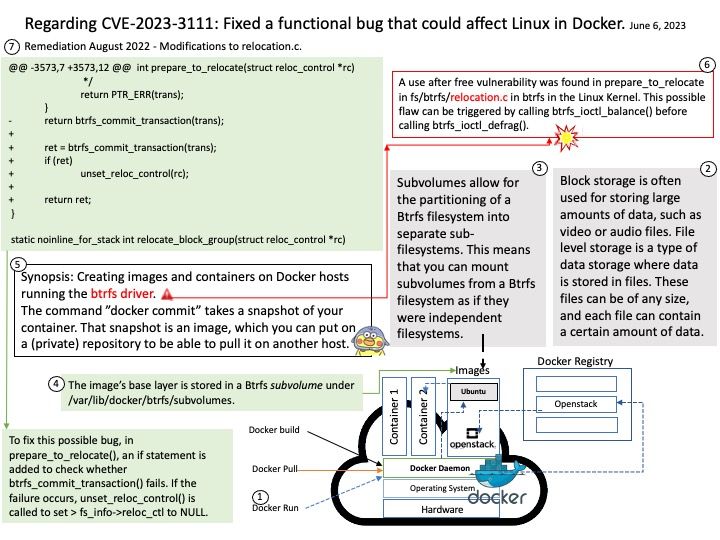
Subvolumes allow for the partitioning of a Btrfs filesystem into separate sub-filesystems. Therefore, you can mount subvolumes from a Btrfs filesystem as if they were independent filesystems.
Vulnerability details: A use after free vulnerability was found in prepare_to_relocate in fs/btrfs/relocation[.]c in btrfs in the Linux Kernel. This possible flaw can be triggered by calling btrfs_ioctl_balance() before calling btrfs_ioctl_defrag().
Solution: To fix this possible bug, in prepare_to_relocate(), an if statement is added to check whether btrfs_commit_transaction() fails. If the failure occurs, unset_reloc_control() is called to set > fs_info->reloc_ctl to NULL.
Official details: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-3111