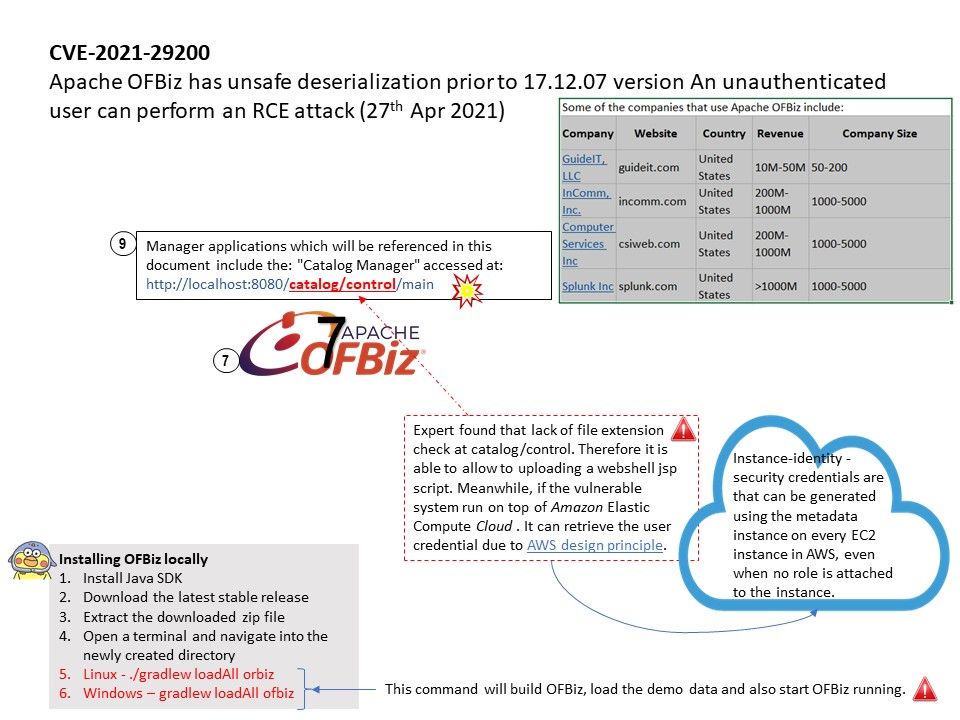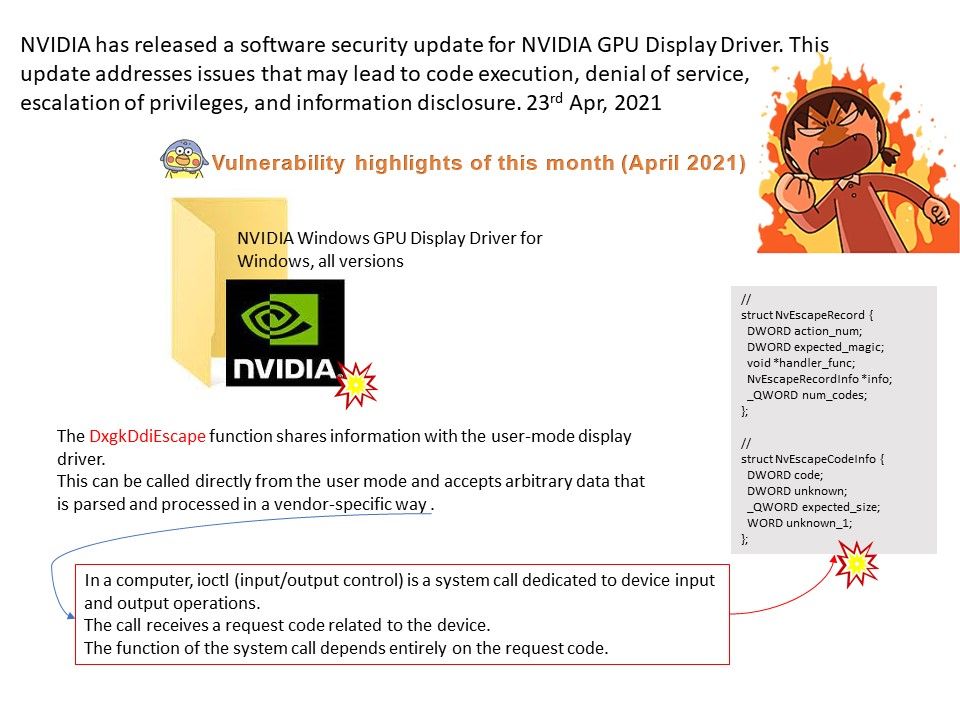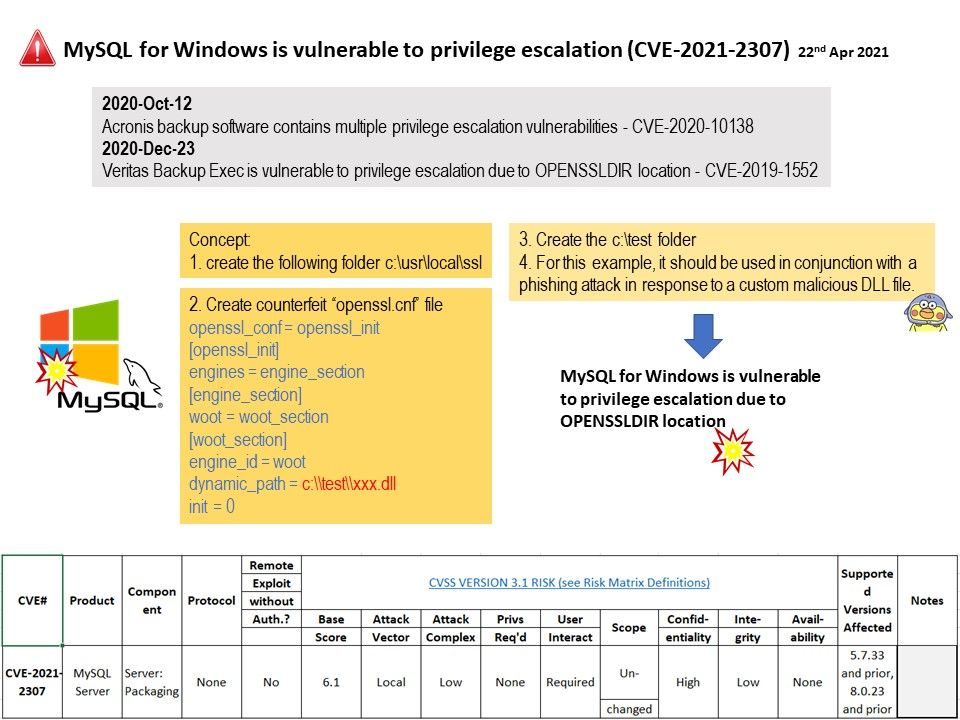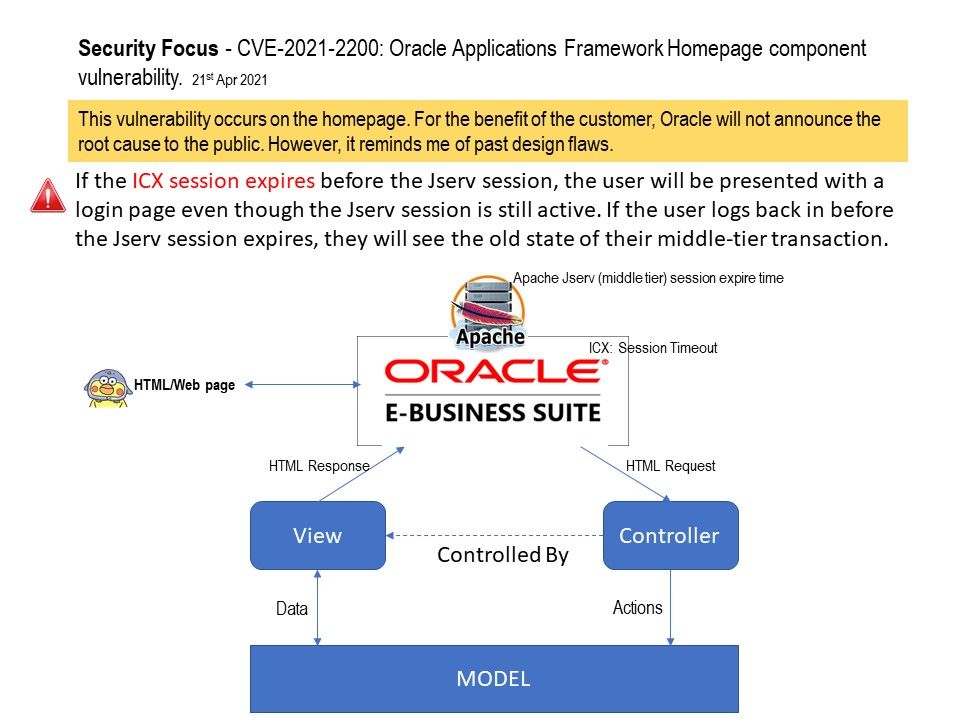
Background: DBUtil_2_3. Sys is a Windows driver. A driver is a small software program that allows your computer to communicate with
hardware or connected devices. This means that a driver has direct access to the internals of the operating system,
hardware etc.
Vulnerability details: Dell dbutil_2_3.sys driver contains an insufficient access control vulnerability which may lead to escalation of privileges,
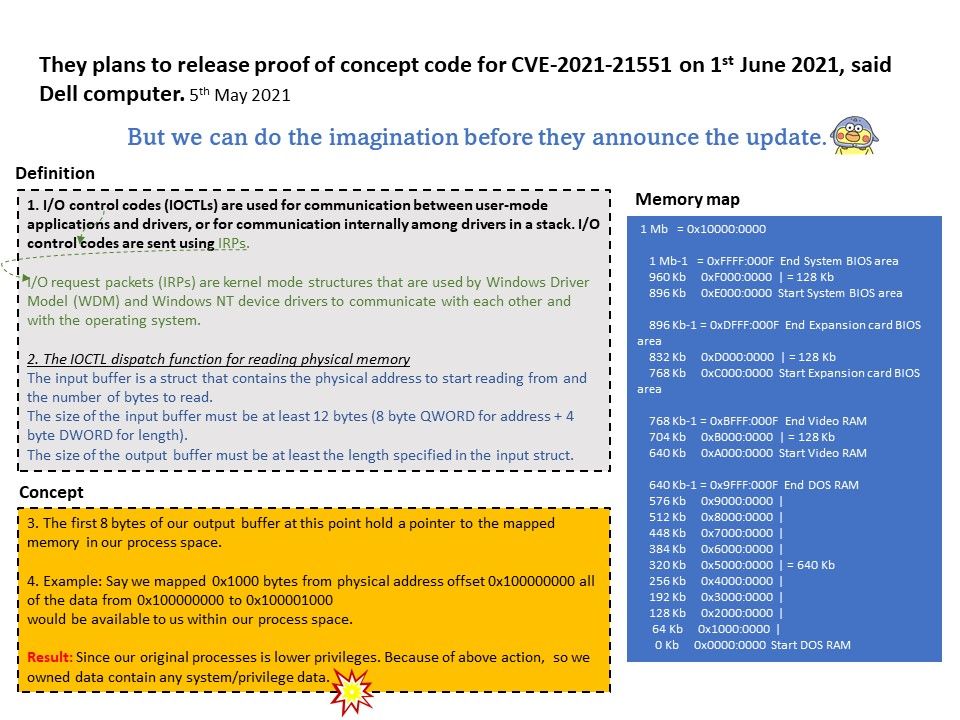
denial of service, or information disclosure. Local authenticated user access is required. Vendor plans to release proof of concept code for CVE-2021-21551 on 1st June 2021, said Dell computer.
But we can do the imagination before they announce the update. For details, please refer to diagram.
Official announcement – https://www.dell.com/support/kbdoc/zh-hk/000186019/dsa-2021-088-dell-client-platform-security-update-for-dell-driver-insufficient-access-control-vulnerability
.jpg)