Preface: To improve bandwidth utilization, an introduce of layer-4 relay(s) that enable the pipelining of TCP connections.
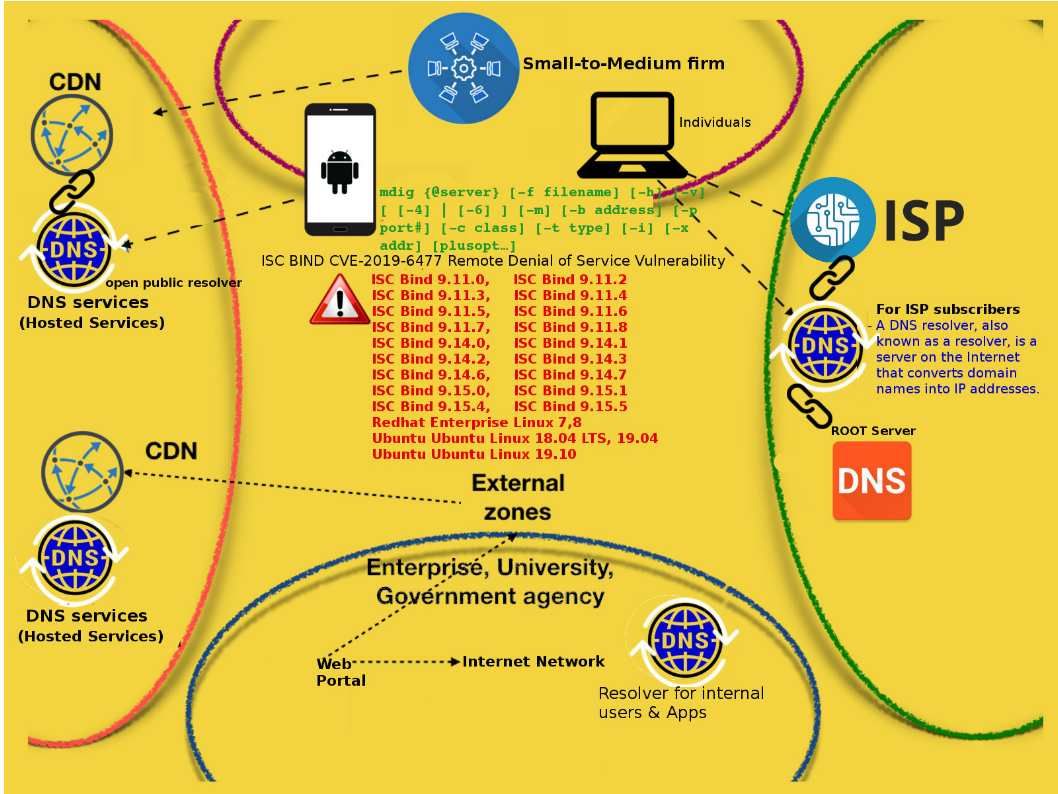
Background: BIND 9 has evolved to be a very flexible, full-featured DNS system. On a server with TCP-pipelining capability,it is possible for one TCP client to send a large number of DNS requests over a single connection.
Vulnerability details: It was discovered that Bind incorrectly handled certain TCP-pipelined queries. A remote attacker could possibly use this issue to cause Bind to consume resources, resulting in a denial of service.
Observation: Before remedy apply, such design weakness may provide a pathway to cyber criminals conduct a denial of service attack. Perhaps it is easy to start the attack then suspened the DNS services. Eventhough you have defense control but cannot avoid. The official announcement and remedy solution can be find in following url. https://kb.isc.org/docs/cve-2019-6477