Preface: Virtualization in the virtualization platform. It is definitely a microsystem architecture.
Technical background: Windows Sandbox requires a Type 1 hypervisor. Therefore, to run Sandbox on a virtual machine, nested virtualization must be enabled. Nested virtualization allows running Hyper-V on a virtual machine. In addition, it allows Windows Sandbox to run on a virtual machine.
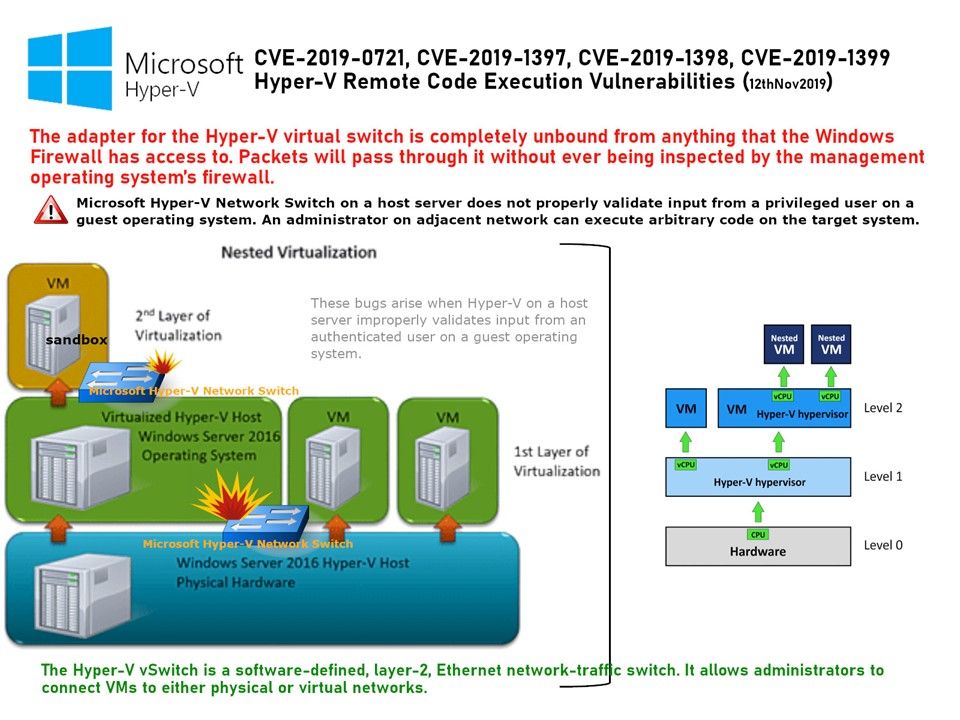
The Hyper-V vSwitch is a software-defined, layer-2, Ethernet network-traffic switch. It allows administrators to connect VMs to either physical or virtual networks. The adapter for the Hyper-V virtual switch is completely unbound from anything that the Windows Firewall has access to. Packets will pass through it without ever being inspected by the management operating system’s firewall.
Vulnerability details: An attacker could run malicious code on a guest operating system, which could cause the Windows Hyper-V host to execute arbitrary code. For the successful of the attack, hacker will run malicious code on a guest operating system. The attacker can do a escape of the VM sandbox once successful. Meanwhile the victim guest VM could cause the Windows Hyper-V host to execute arbitrary code.
Reference: Official announcement –https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1398