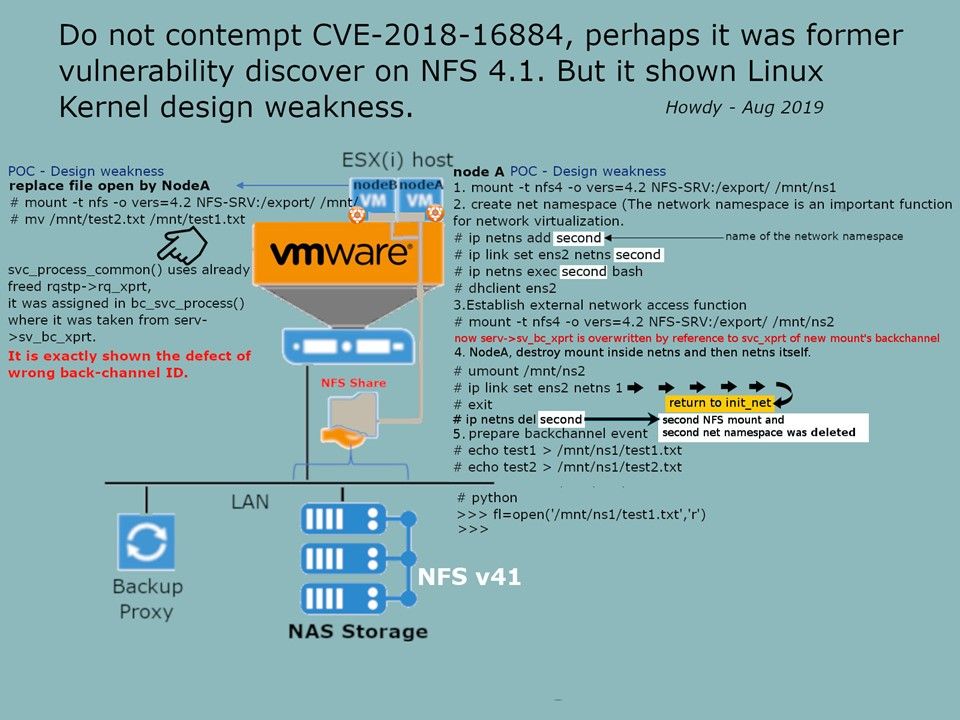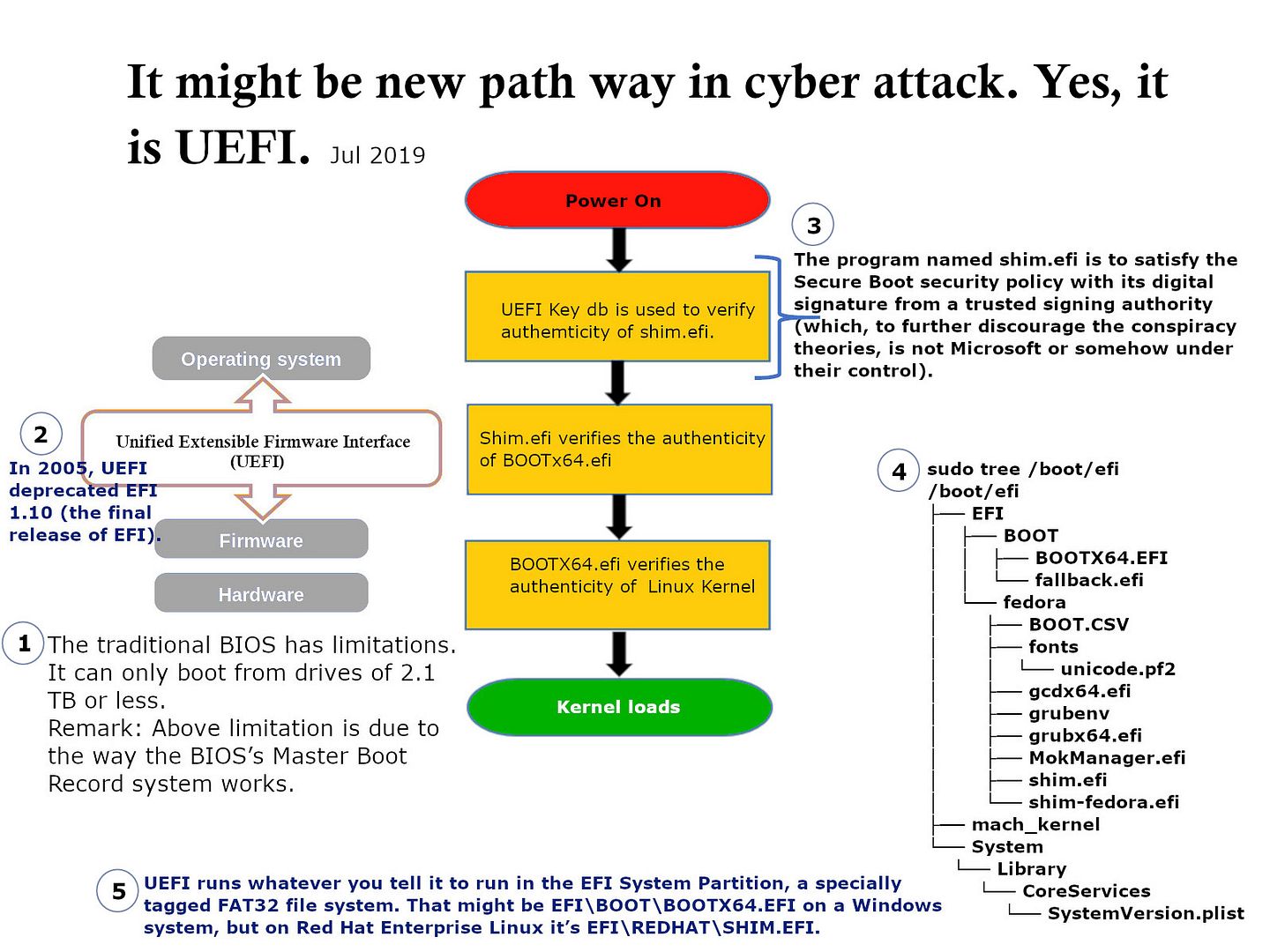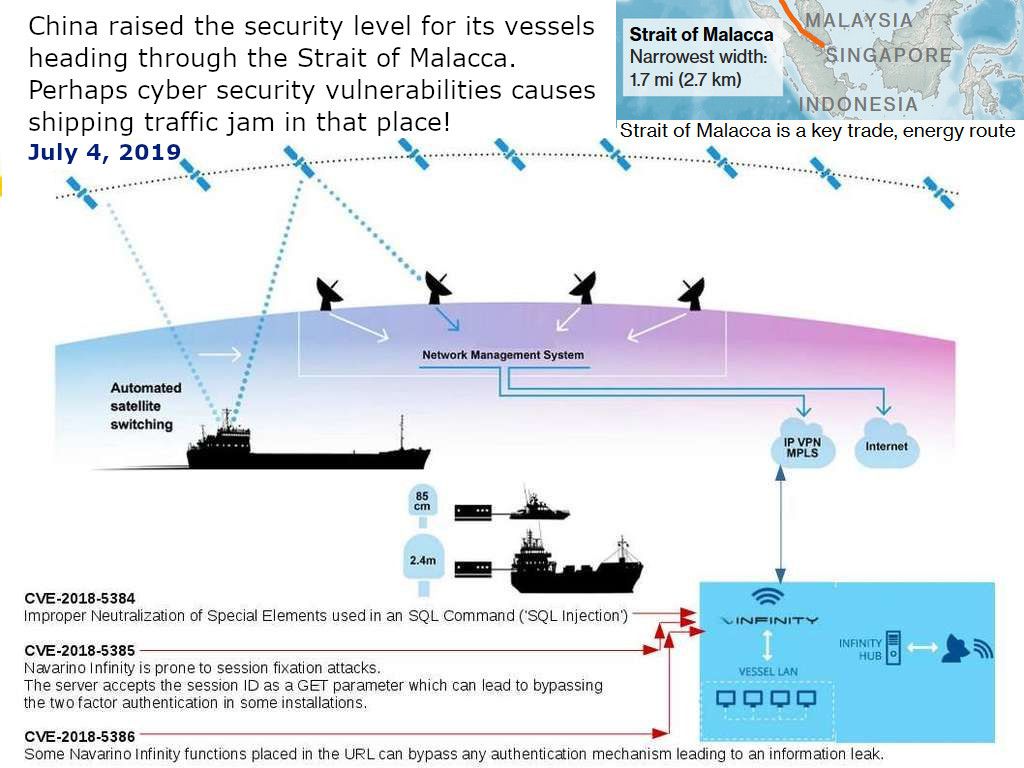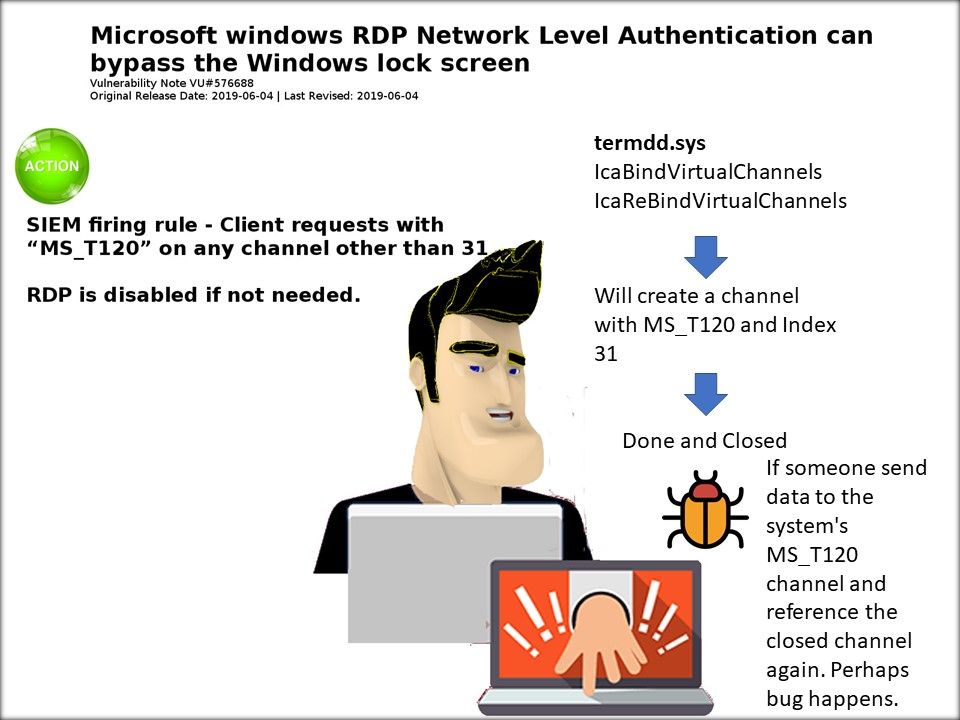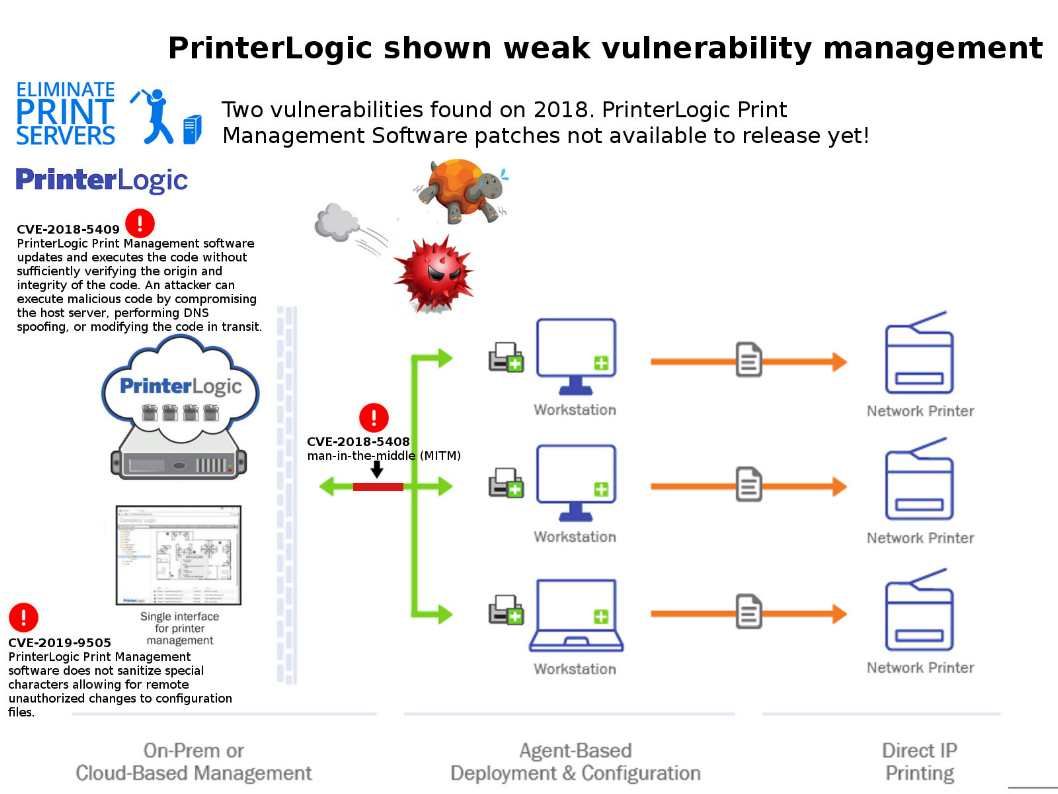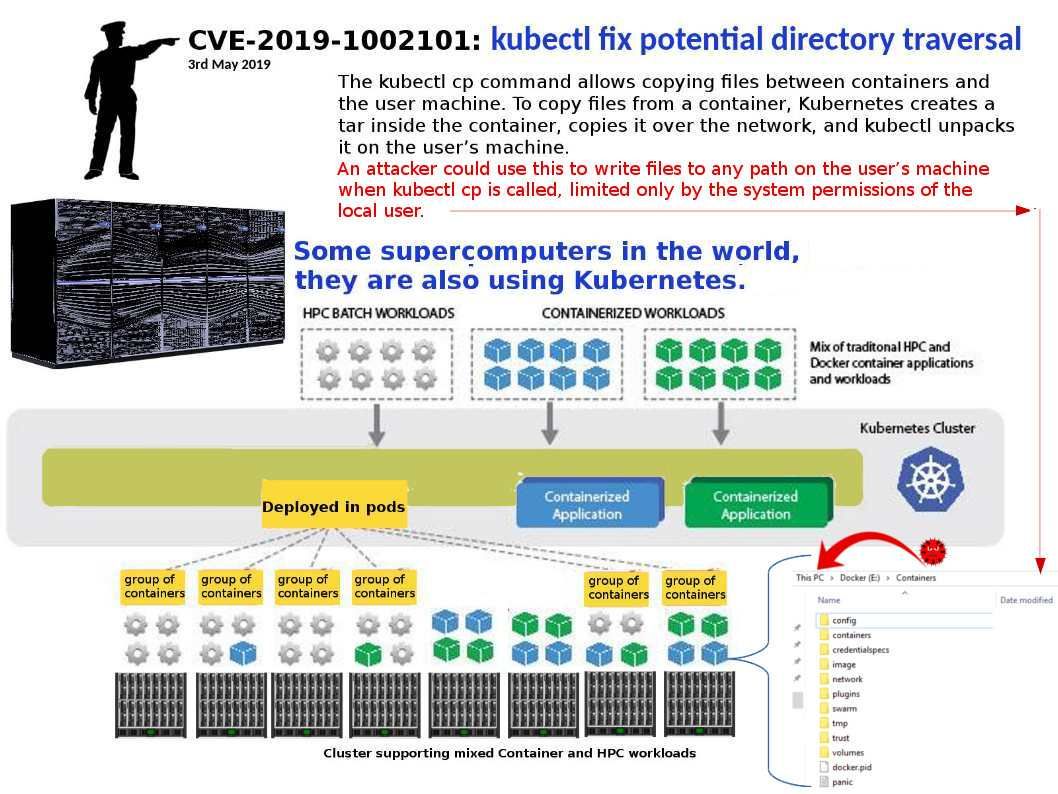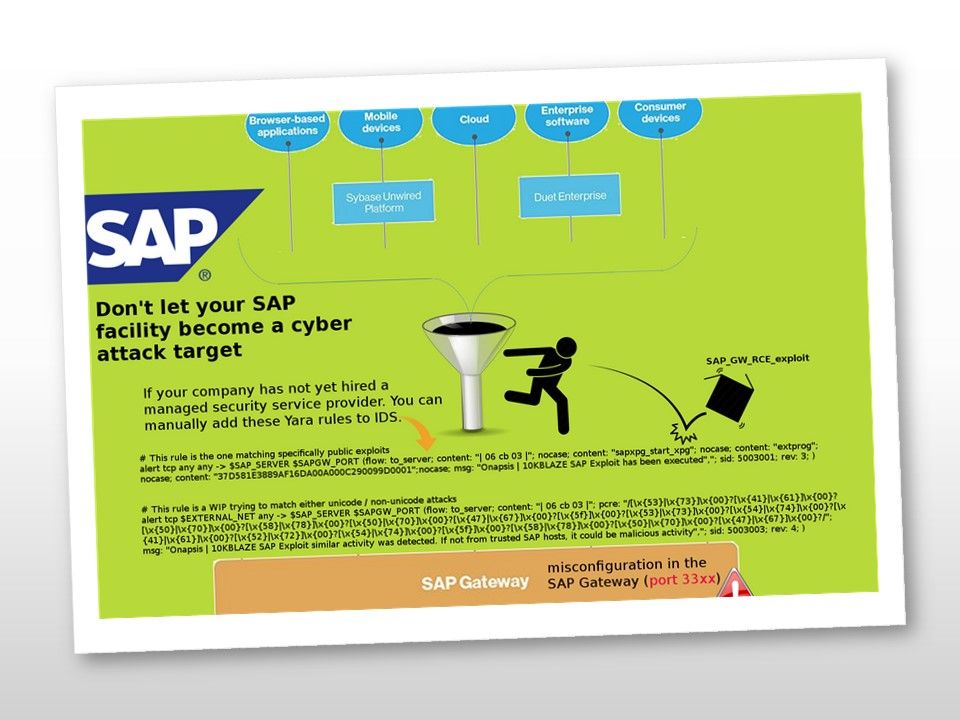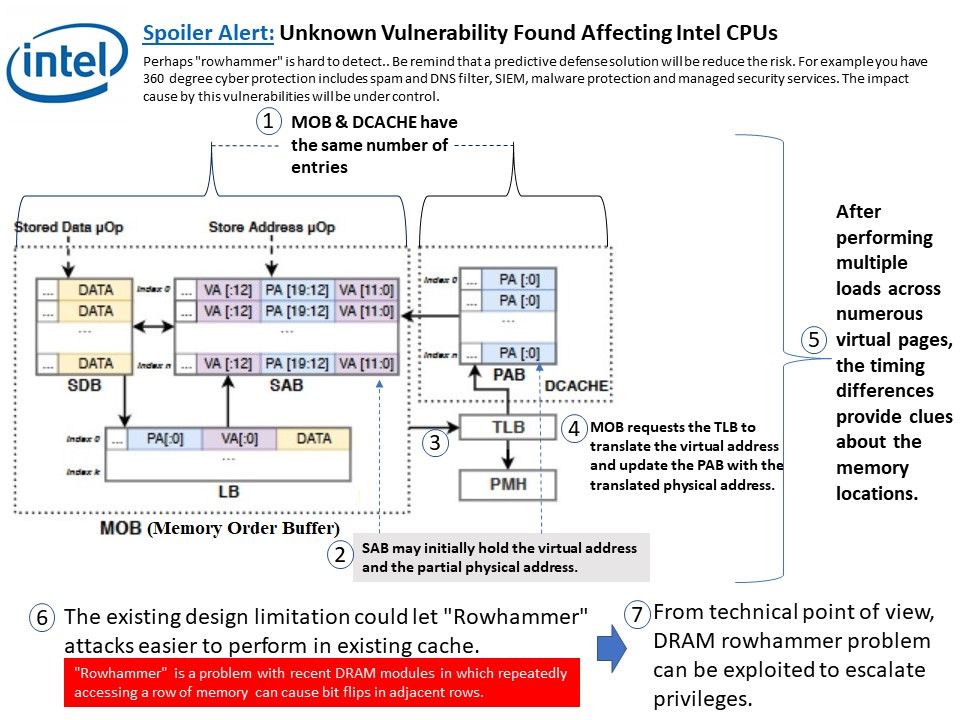
Preface: DNS monitoring can let you predict the user behaviour. According to Cisco’s research, over 90% of attacks are done over DNS and only two-thirds of organizations monitor their DNS records.
Technical details:
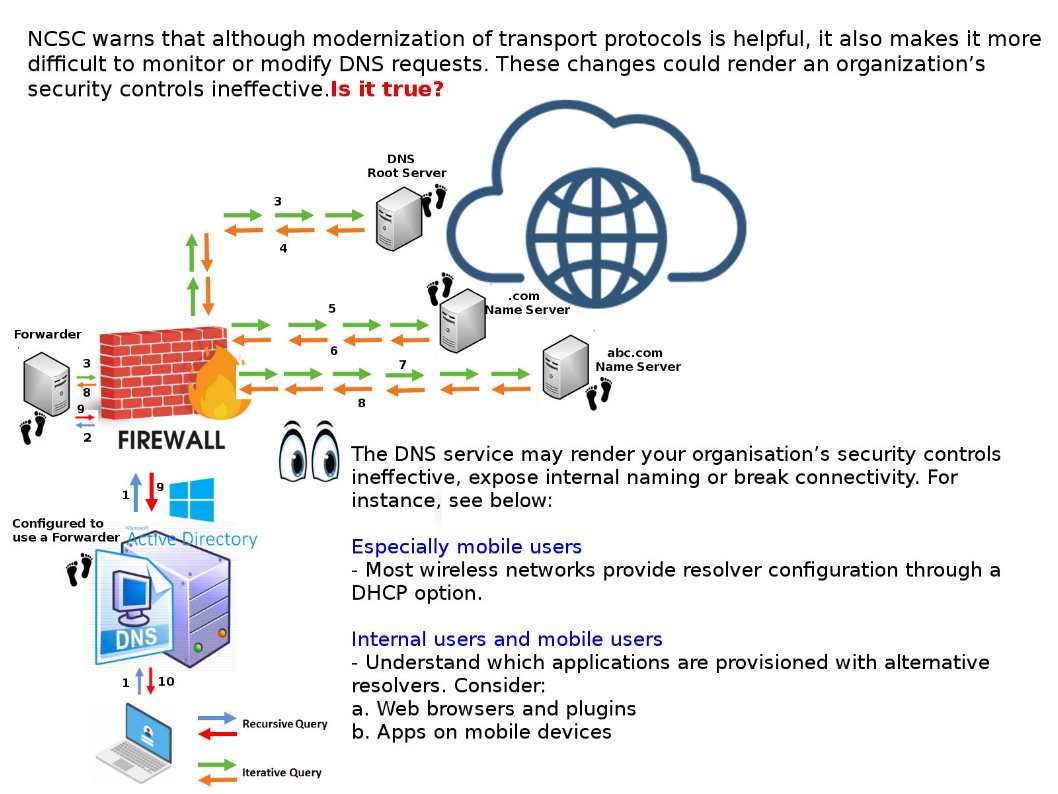
Go to options->Advanced->Network->Settings->Automatic proxy configuration url and enter 8.8.8.8 All you Mozilla traffic uses Google dns now. Google Public DNS fully supports DNSSEC for Domain Name Security Extensions which works against cache poisoning attacks. Meanwhile if mobile device leave company network, DDNS given by wireless hotspot might have way to leave your monitoring. Due to above feature, the Dutch National Cyber Security Centre (NCSC) has released a fact sheet on the increasing difficulty of Domain Name System (DNS) monitoring. For more details, please refer to URL: https://english.ncsc.nl/publications/factsheets/2019/oktober/2/factsheet-dns-monitoring-will-get-harder