Vulnerability Note VU#576688
Original Release Date: 2019-06-04 | Last Revised: 2019-06-04
Preface: The more the power you have, the greater the risk is being infected.
Synopsis: Microsoft Windows RDP Network Level Authentication can allow an attacker to bypass the lock screen on remote sessions.
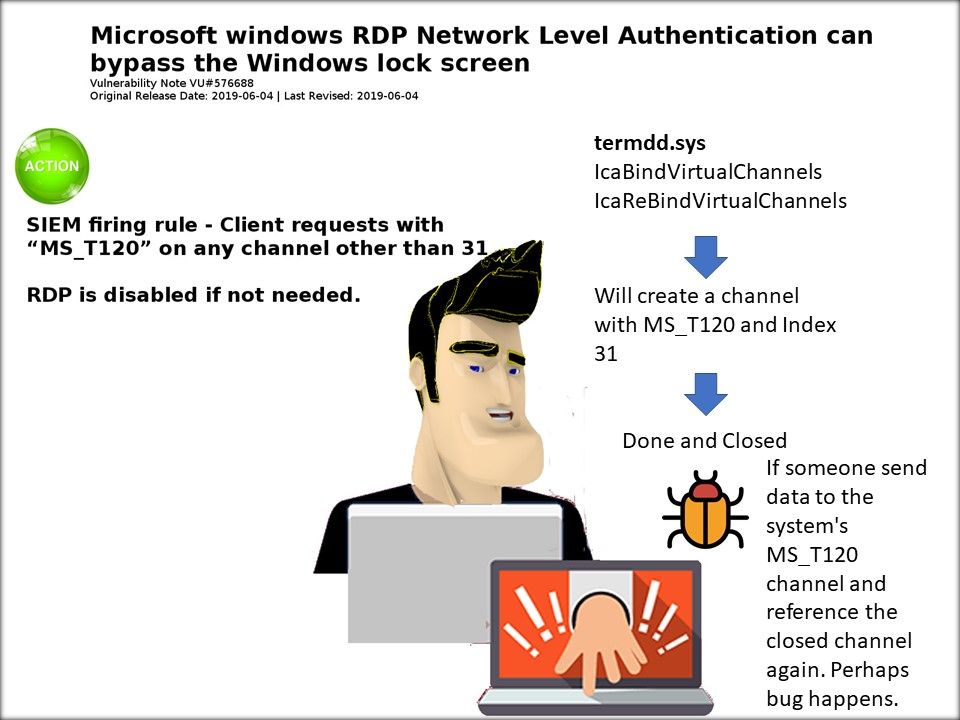
My observation: Observing that Microsoft re-engineering the RDP with create a channel with MS_T120 and Index 31.
But vulnerability occurs when someone send data to the system’s MS_T120 channel and reference the closed channel again.
Interim remediation step:
- RDP is disabled if not needed.
- SIEM firing rule – client requests with “MST-T120′ on any channel other than 31
Reference: https://kb.cert.org/vuls/id/576688/