Preface: UEFI has slowly come to replace BIOS. Whereby Intel schedule to completely replace BIOS with UEFI on all chipsets by 2020.
Quote: Firmware is software, and is therefore vulnerable to the same threats that typically target software.
Technical details: From technical point of view, EFI Runtime services are usually located below 4GB. As a result it has a way into Linux on high memory EFI booting systems.
What is the different when malware alive into these areas?
- Malware injected into the address space is transient, and will be cleaned up on the next boot.
- Malware injected into the firmware flash regions is persistent, and will run on every subsequent boot
Using the follow command can display x509 v3 digital certificate and confirm thatgrubx64.efi can read (/boot/efi/EFI/fedora/)grub.cfg. Oh! It is easy to access this file when you have root privileges. But do not contempt this issue.
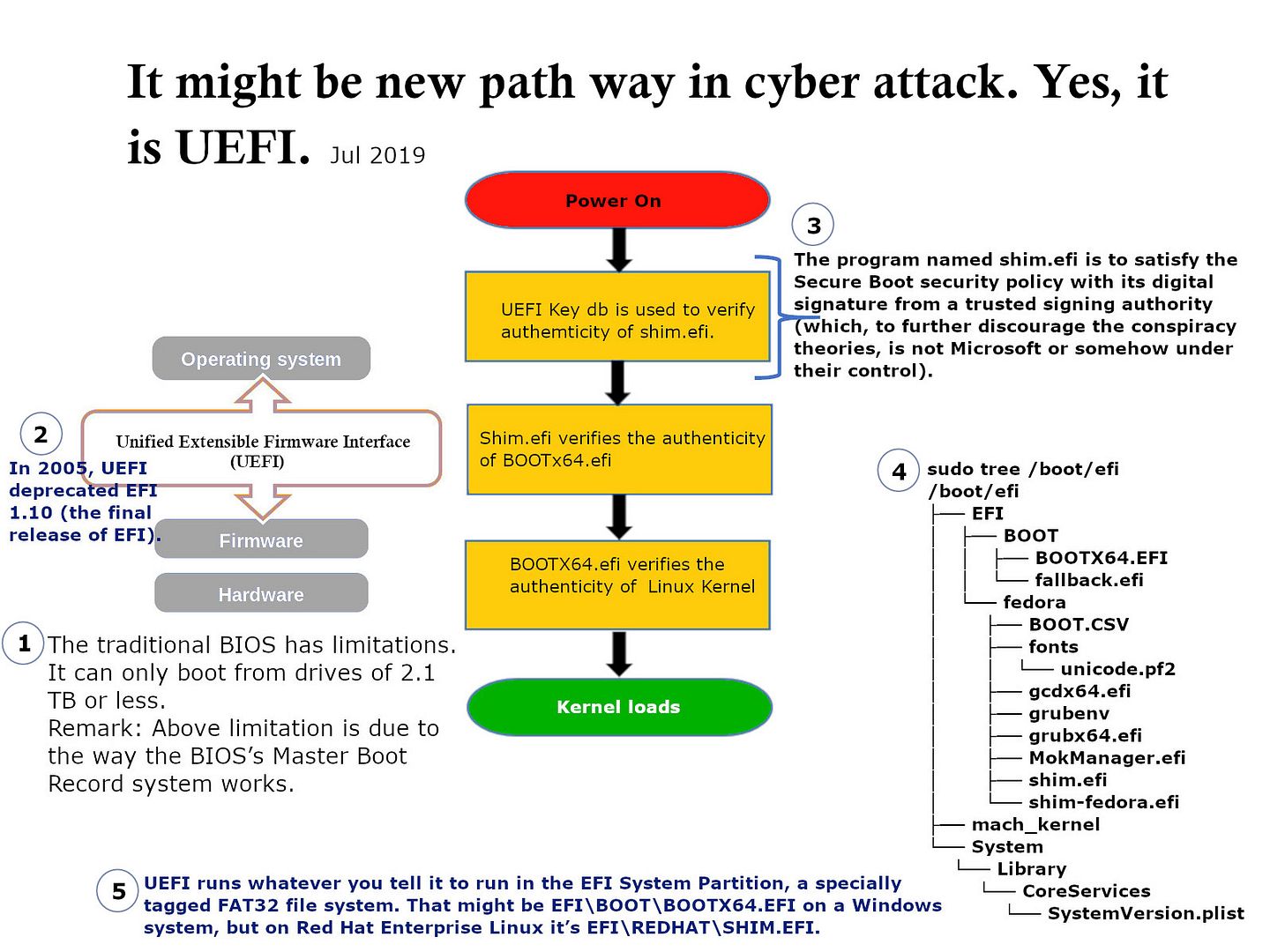
- sudo tree /boot/efi
- sudo hexdump -C /boot/efi/EFI/fedora/shim.efi | egrep -i -C 2 ‘grub|g.r.u.b’
- sudo strings /boot/efi/EFI/fedora/grubx64.efi | grep grub.cfg
Sound interesting. Should you have interested, please refer below guide book :NIST Special Publication 800-147 BIOS Protection Guidelines https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-147.pdf