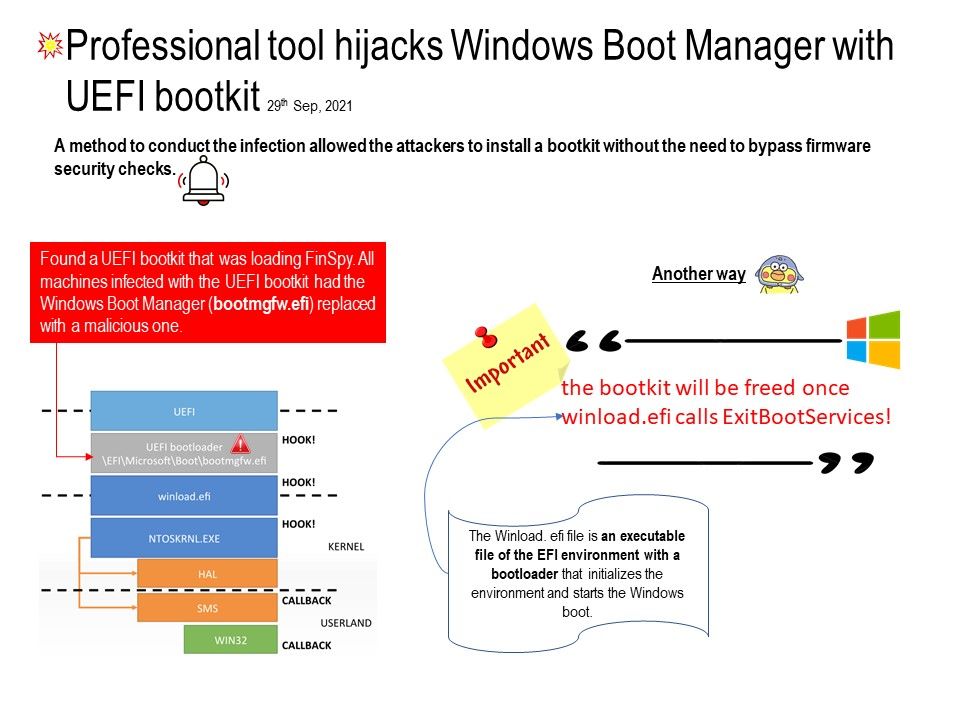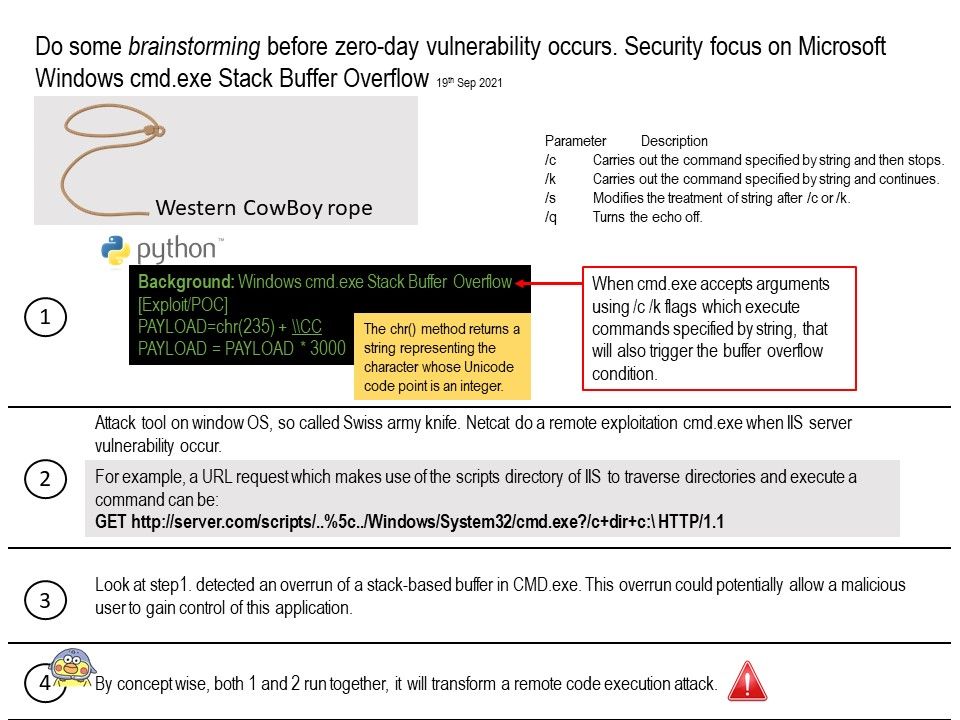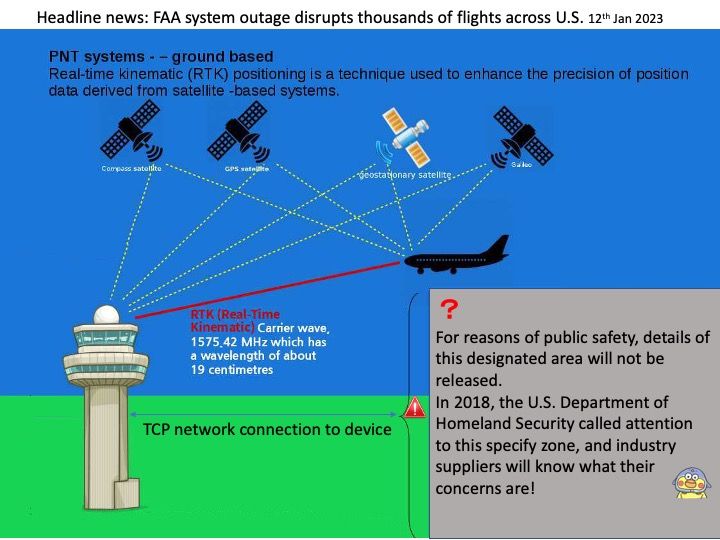
Preface: Thousands of flights across the U.S. were delayed Wednesday after a Federal Aviation Administration pilot alert system failed overnight, prompting a nationwide halt to departures. said CNBC news.
Headline news – https://www.cnbc.com/2023/01/11/faa-orders-airlines-to-pause-departures-until-9-am-et-after-system-outage.html
Background: The Department of Homeland Security published the following opinion piece four years ago.
The GPS system is now considered a “crosssector dependency” for the Department of Homeland Security’s (DHS) 16 designated critical infrastructure sectors. GNSS is vulnerable to jamming and natural interference. When GNSS is denied, PNT information can be seriously affected in ways that increase risks to the safety of navigation.
My observation: Perhaps the incident was not caused by a cyber attack. But industry experts know that the overall system architecture will be combined with OS vendor-dependent drivers.
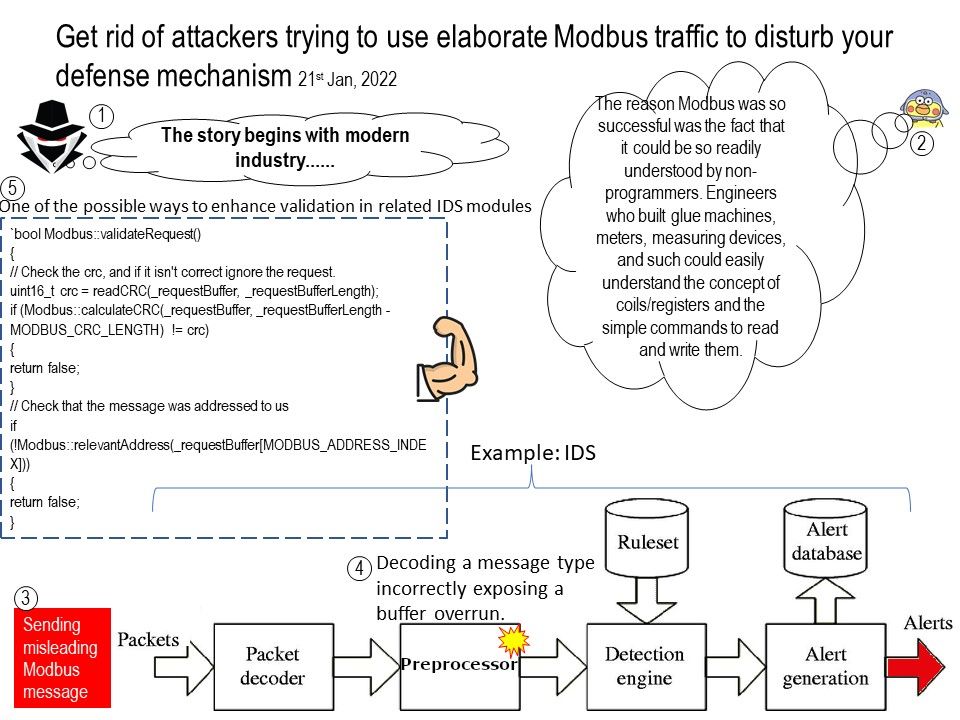
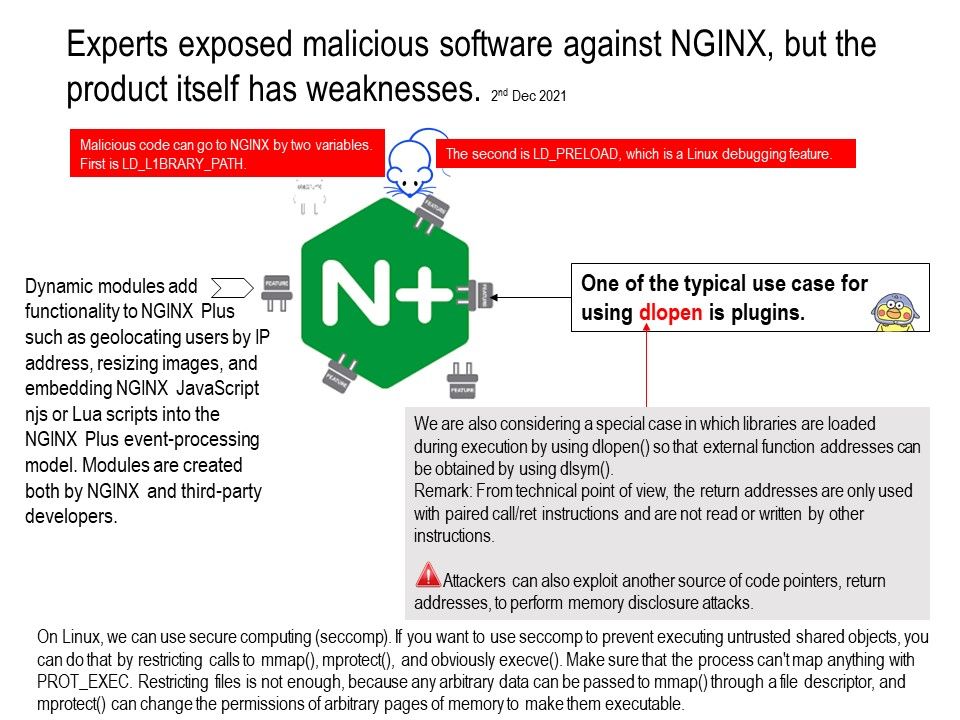
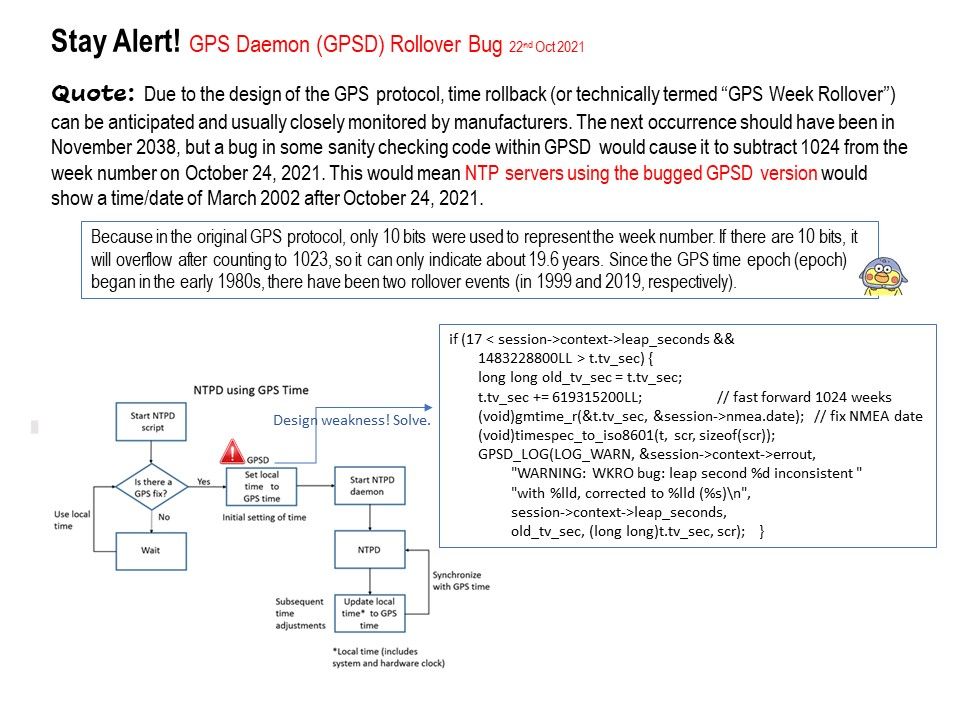
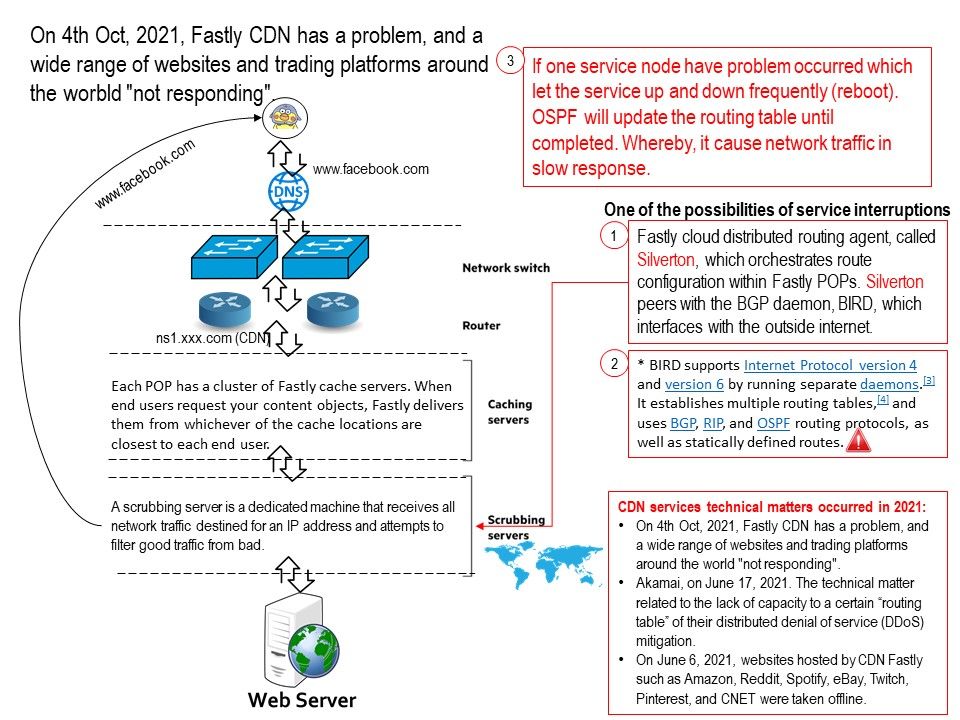
For example: if the driver is written as a specify standard driver using user-mode extensions is not recommended because this model will likely require more memory usage. However, this specify standard is available on all platforms and it is strongly recommended to use the driver written in user mode.
So, the function is not only OS specific, it also including 3rd party vendor to do the software development. As a matter of fact, aero industry is a special zone. The current computer technology is also involving such zone. In computer world nowadays, the patch to vulnerability is common. So, who can say that this is a trust zone and it is without vulnerability forever.
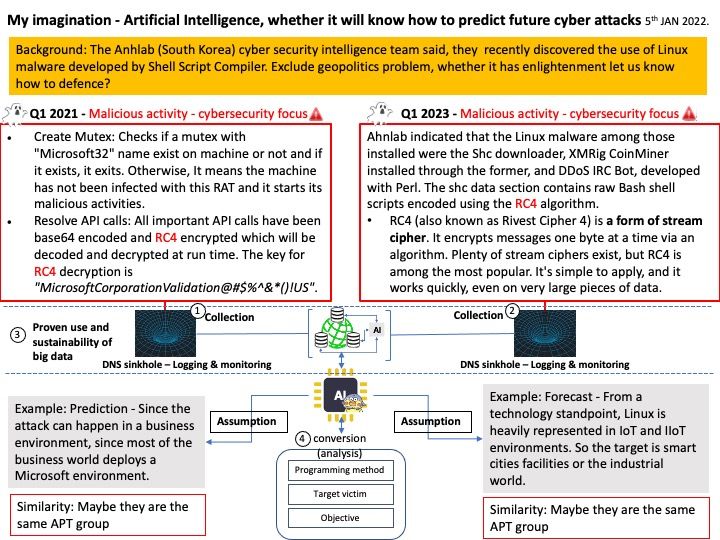
.jpg)