Preface: Le Rouge et le Noir – Not a bad guy is good guy. If, the vulnerability is due to an integer overflow when handling Modbus traffic. Is it an early warning?
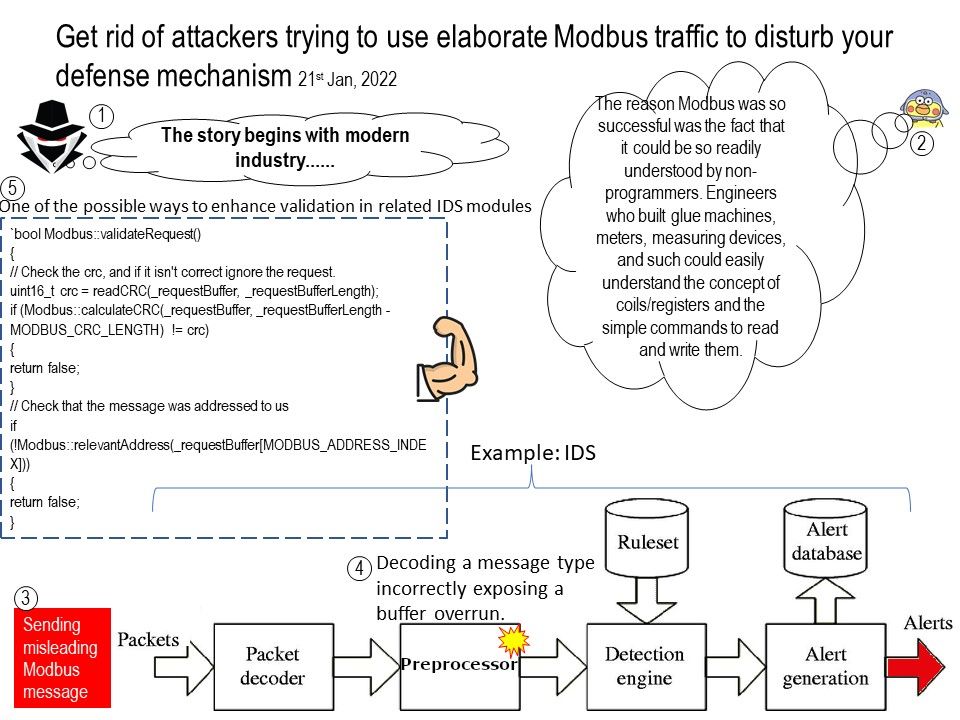
Background: The reason Modbus was so successful was the fact that it could be so readily understood by non-programmers. Engineers who built glue machines, meters, measuring devices, and such could easily understand the concept of coils/registers and the simple commands to read and write them.
About cyber attack: Modbus over serial is immune to any common malware attacks. But what methods will increase the risk of Modbus network attacks? See below:
I. MODBUS over TCP means a MODBUS RTU packet wrapped in a TCP packet.
II. MODBUS TCP means a MODBUS TCP packet wrapped in a TCP packet.
Perhaps a common idea will said Modbus driver might be vulnerable to attack. However, above two types of TCP communications methods are increasing the possibilities of attack. For instance, an attacker could sending crafted Modbus traffic attack a IDS. (This IDS device aim to protect the back-end HMI, PLC and SCADA infrastructure).
Due to implementation of decoding a message type incorrectly exposing a buffer overrun. This is equivalent a denial of service.
One of the possible ways to enhance validation in related IDS modules. (see below):
- Check the crc, and if it isn’t correct ignore the request.
- Check the validty of the data based on the function code.
- Broadcast is not supported
- Add bytes to expected request size (2 x Index, 2 x Count)
Due to PLC, the HMI for repair or mitigation is not so flexible because it affects industrial systems and/or related operating functions.
Sometimes even IIoT manufacturers cannot provide you with a clear upgrade roadmap. Therefore, installing IDS as detection and preventive control is an effective way to implement protection. This discussion does not focus on any IDS devices. If you have any related matters, it is recommended to listen to the supplier’s opinions.
End of writing.