Preface: Twenty years ago, content filter firewalls were not popular. A quick way to harden the Microsoft Internet Information server is to delete all cmd commands to avoid network attacks.
Background: If you would like to run cmd in privileged mode. You have to do the following:
- type “CMD” you can hit Ctrl+Shift+Enter to open as administration
- Explorer – Hold Shift and right click on a folder, and choose “Open command window here”
To use multiple commands for , separate them by the command separator && and enclose them in quotation marks.
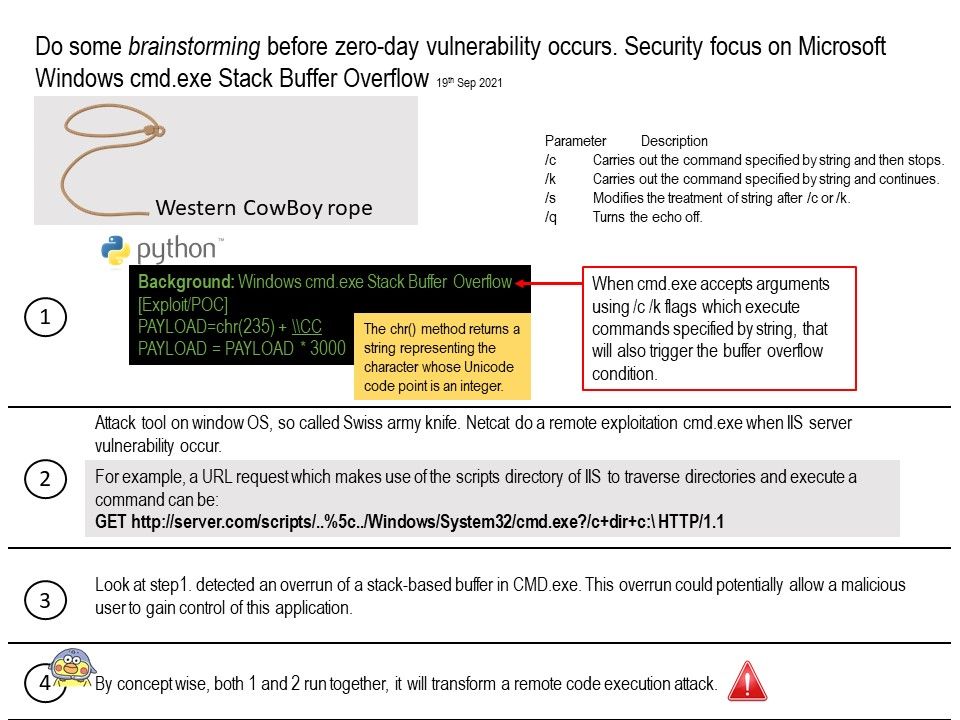
Vulnerability details: Expert found that special crafted payload will trigger a Stack Buffer Overflow in the NT Windows “cmd[.]exe” commandline interpreter. Furthermore, running file type especially [dot]cmd or [bot]bat will be risky. However, when cmd[.]exe accepts arguments using /c /k flags which execute commands specified by string, that will trigger the buffer overflow condition.
Above attack only exploit in local workstation. Do you think it can do it remotely? As far as I remember, if the situation is available. For example, Windows OS server encounter zero day or not patched.The netcat tool can do a remote command execution by CMD. Refer to attached diagram, if the stack buffer overflow run by tool to exploit by concept. Therefore this vulnerability will become more risky.
Observation: If your are using application firewall. It will drop the malicious traffic including netcat command automatically. Since this idea is still in concept stage. So, no need to worries.