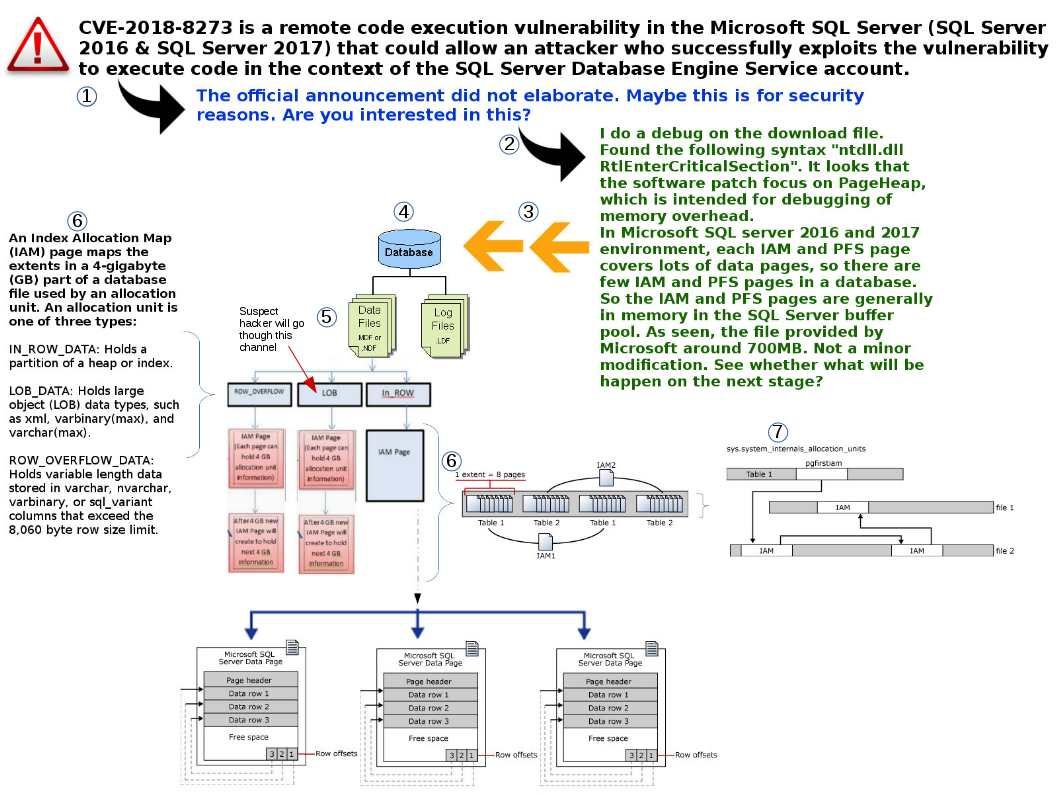
Above vulnerability looks complicated. It is only effect SQL server 2016 and 2017.
I do a debug on the download file.
Found the following syntax “ntdll.dll RtlEnterCriticalSection”. It looks that the software patch focus on PageHeap, which is intended for debugging of memory overhead.
In Microsoft SQL server 2016 and 2017 environment, each IAM and PFS page covers lots of data pages, so there are few IAM and PFS pages in a database. So the IAM and PFS pages are generally in memory in the SQL Server buffer pool. As seen, the file provided by Microsoft around 700MB. Not a minor modification. See whether what will be happen on the next stage?
Should you have interest, please reference below diagram.
Official announcement shown below:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8273