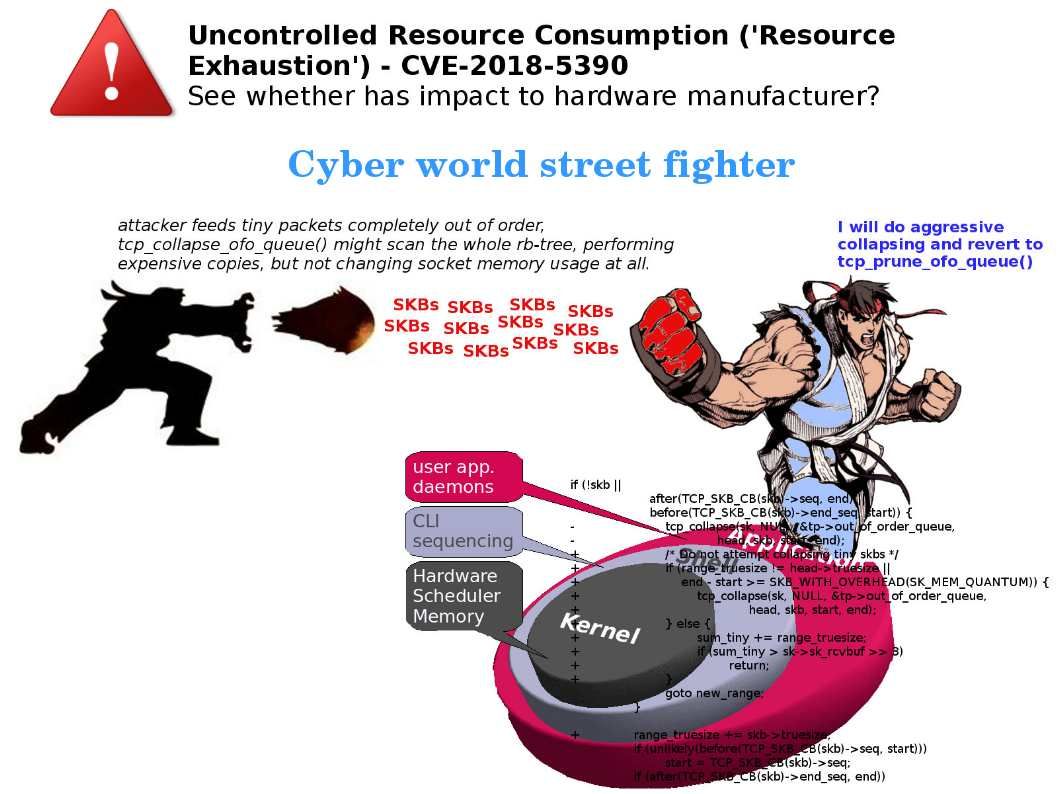
The hardware vendors deploy Linux OS on demand growth. Even though your firewall appliances, malware detector, load balancer, network L2 and L3 switch and IoT devices are the Linux. The attacker found a tricks recently. If source device feeds tiny packets completely out of order. The parameter (tcp_collapse_ofo_queue()) might scan the whole rb-tree. As a result , attacker can induce a denial of service condition by sending specially modified packets within ongoing TCP sessions. I think the specfiy vulnerability we can not contempt. The worst case is that attacker is possible to conduct denial of services on non-patch hardware appliances and IoT devices.
In the meantime, we are waiting for hardware vendor responses?
US CERT official announcement shown as below:
Linux Kernel TCP implementation vulnerable to Denial of Service
https://www.kb.cert.org/vuls/id/962459