Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
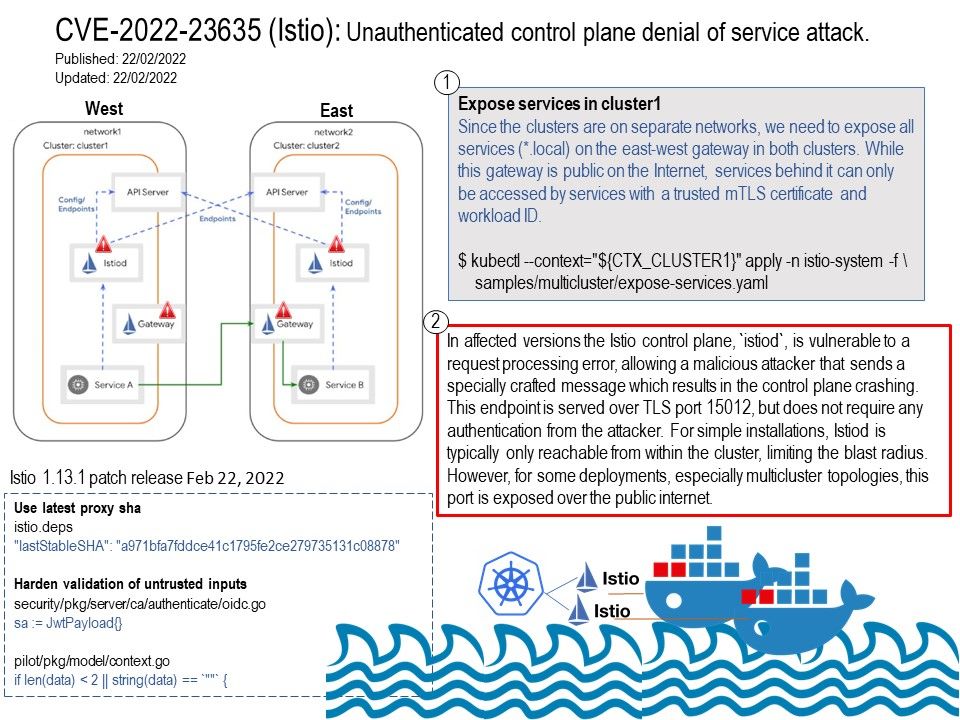
Background: Istio makes traffic management transparent to the application, moving this functionality out of the application and into the platform layer as a cloud native infrastructure. Istio complements Kubernetes, by enhancing its traffic management, observability and security for cloud native applications. Istio is an open source service mesh that layers transparently onto existing distributed applications. A service mesh often has complex operational requirements which include A/B testing, canary releases, access control, and rate limiting. These are in addition to its standard requirements of load balancing, discovering, failure recovery, end-to-end authentication, monitoring, and metrics.
Vulnerability details: The Istio control plane, istiod, is vulnerable to a request processing error, allowing a malicious attacker that sends a specially crafted message which results in the control plane crashing. This endpoint is served over TLS port 15012, but does not require any authentication from the attacker……. For more details, please refer to the link – https://istio.io/latest/news/security/istio-security-2022-003/
Remedy: This release fixes the security vulnerabilities described in our February 22nd post, ISTIO-SECURITY-2022-003. This release note describes what’s different between Istio 1.13.0 and 1.13.1. For more details, please refer to the link – https://istio.io/latest/news/releases/1.13.x/announcing-1.13.1/
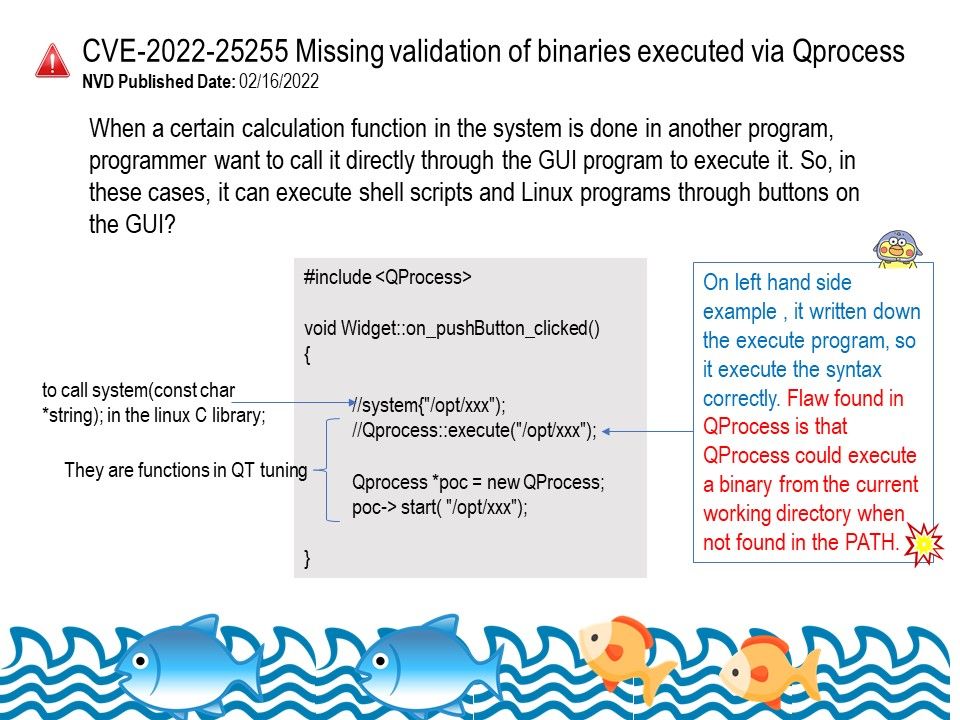
.jpg?width=1920&height=1080&fit=bounds)
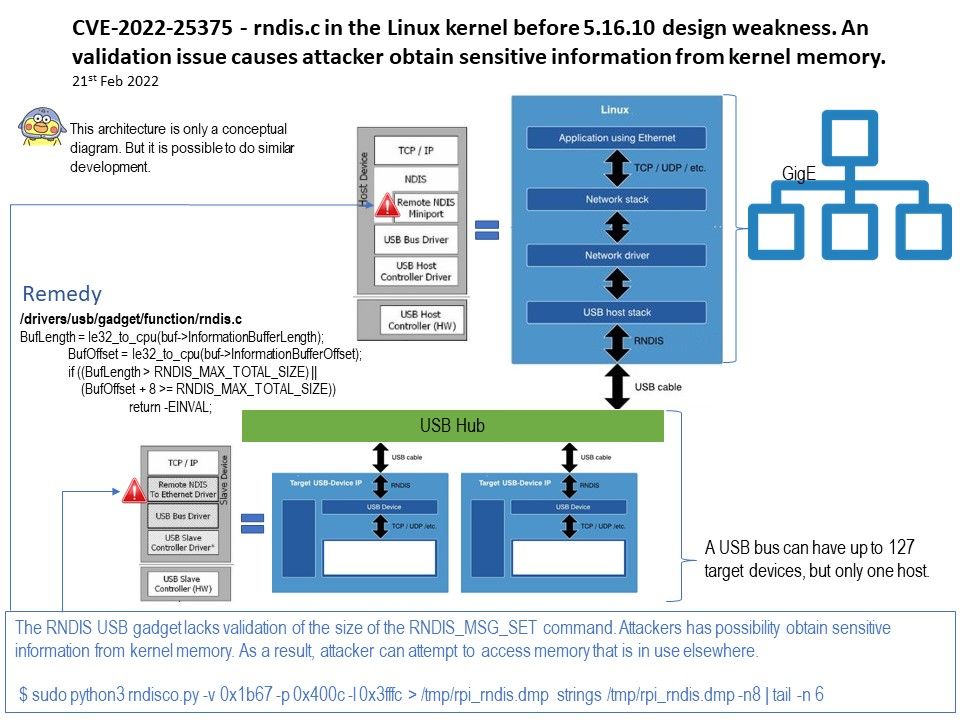
.jpg?width=1920&height=1080&fit=bounds)
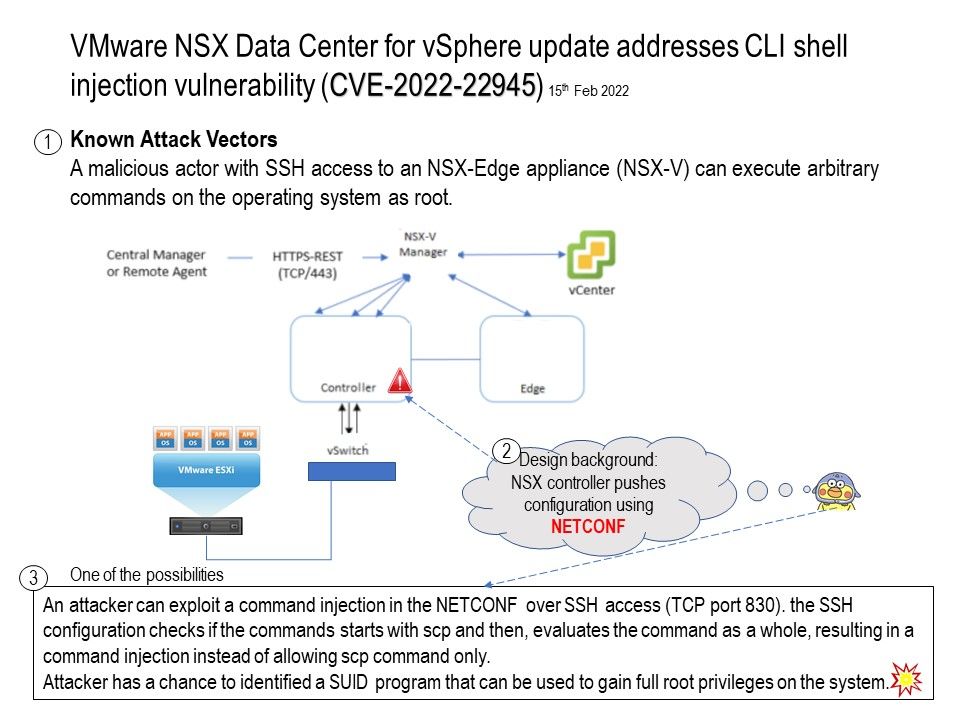
.jpg?width=1920&height=1080&fit=bounds)