Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: NSX Data Center for vSphere provides networking and security functionality for your vSphere environment, including logical switching, logical routing, Distributed Firewall, load balancer, NAT, and VPN. NSX Data Center for vSphere is installed as a plug-in to VMware vCenter Server®.
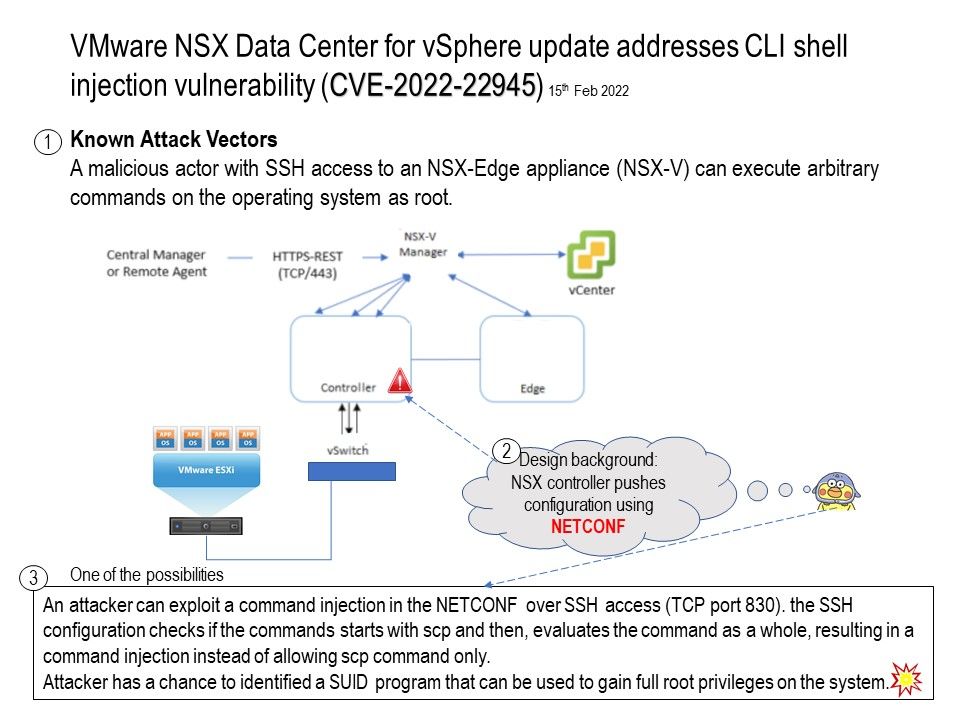
Vulnerability details: The vulnerability allows a local user to escalate privileges on the system.
The vulnerability exists due to improper input validation in the NSX Edge appliance component. A local user with access to NSX-Edge appliance (NSX-V) can pass specially crafted argument to unspecified shell utility and execute arbitrary OS commands as root.
One of the possibilities: An attacker can exploit a command injection in the NETCONF over SSH access (TCP port 830). the SSH configuration checks if the commands starts with scp and then, evaluates the command as a whole, resulting in a command injection instead of allowing scp command only.
Attacker has a chance to identified a SUID program that can be used to gain full root privileges on the system.
Official announcement: Refer to the link for details – https://www.vmware.com/security/advisories/VMSA-2022-0005.html