Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
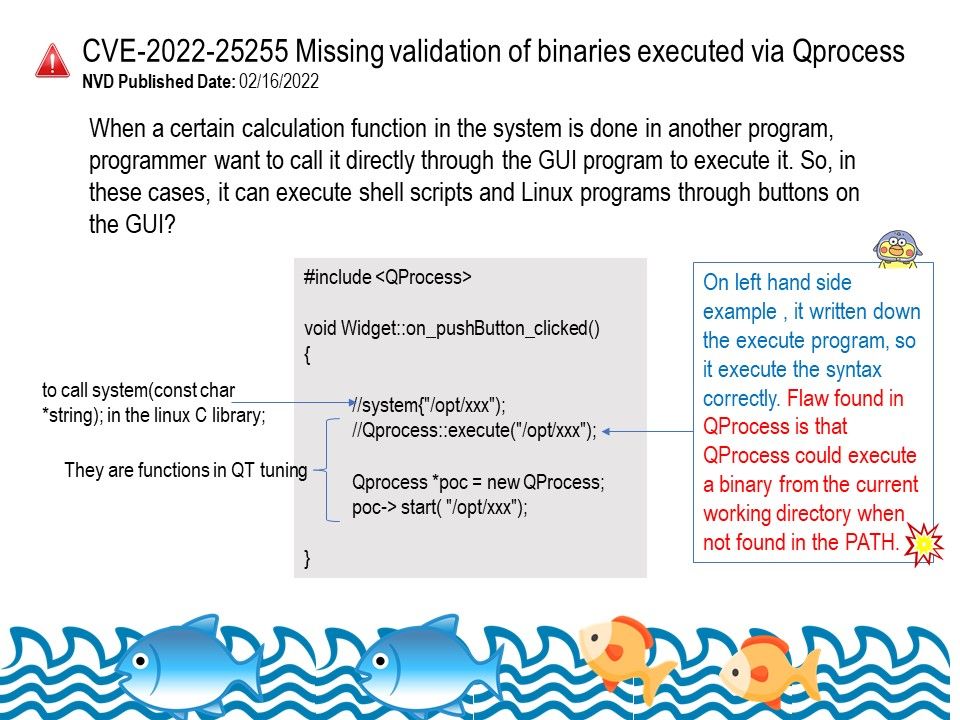
Background: QProcess – Used to start external programs and to communicate with them. The QProcess class is used to start external programs and to communicate with them. To start a process, pass the name and command line arguments of the program you want to run as arguments to start().
What is QProcess in Qt? QProcess manages the output of the running process, keeping standard output and standard error data in separate internal buffers. You can select the QProcess’s current read channel by calling setReadChannel(). This is the default channel mode of QProcess.
Vulnerability details: In Qt 5.9.x through 5.15.x before 5.15.9 and 6.x before 6.2.4 on Linux and UNIX, QProcess could execute a binary from the current working directory when not found in the PATH.
Impact – Opening files might lead to the execution of malicious binaries if they are placed in the right directories.
Remedy: When passed a simple program name with no slashes, QProcess on Unix systems will now only search the current directory if “.” is one of the entries in the PATH environment variable. This bug fix restores the behavior QProcess had before Qt 5.9.
Ref: If launching an executable in the directory set by setWorkingDirectory() or inherited from the parent is intended, pass a program name starting with “./”. For more information and best practices about finding an executable, see QProcess’ documentation.