Preface: PyCrypto is no longer under active development (project is dead – 2015). For details, see the link – https://github.com/pycrypto/pycrypto/issues/173
“cryptography” is a package which provides cryptographic recipes and primitives to Python developers. The goal is for it to be your “cryptographic standard library”. It supports Python 3.6+ and PyPy3 7.2+.
Background: “cryptography” is a package which provides cryptographic recipes and primitives to Python developers.
Unlike some OOP languages, Python is dynamically typed, which means that you don’t need to declare what kind of data (e.g. integer, array, etc) a variable can take before using it.
In computer science, a data buffer (or just buffer) is a region of a memory used to temporarily store data while it is being moved from one place to another.
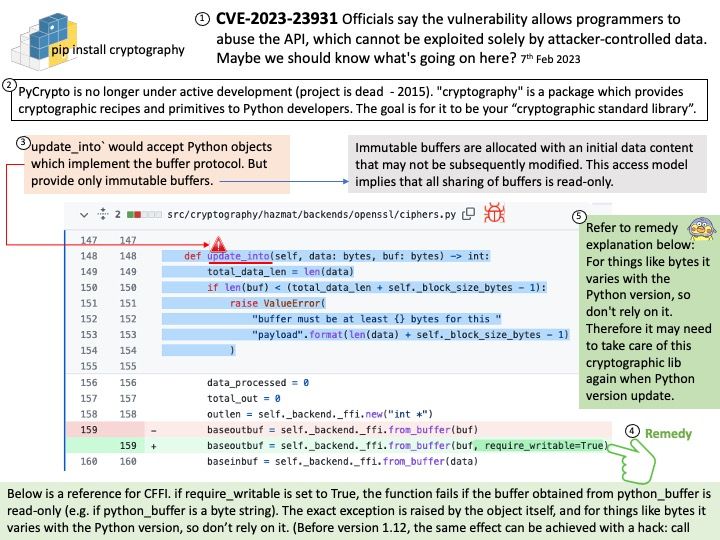
Immutable buffers are allocated with an initial data content that may not be subsequently modified. This access model implies that all sharing of buffers is read-only.
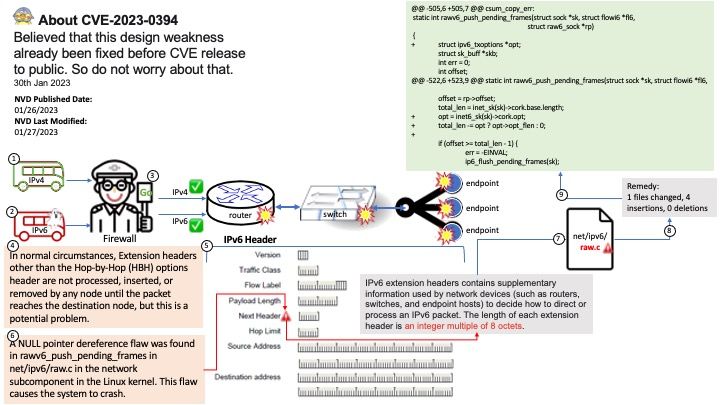
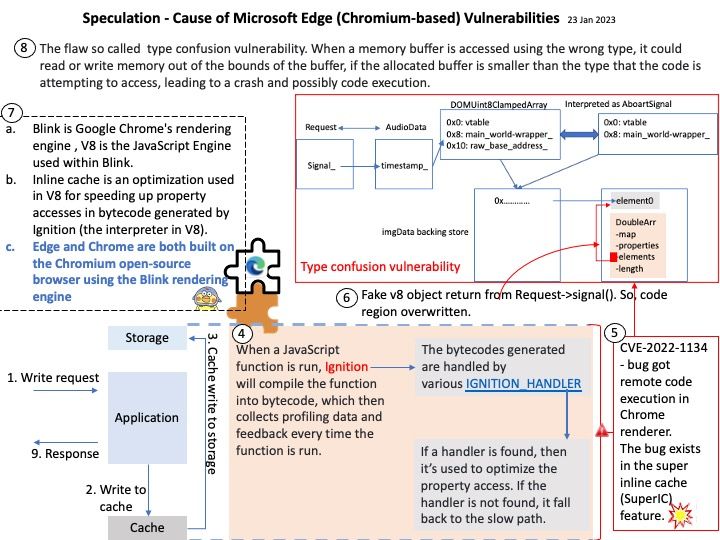
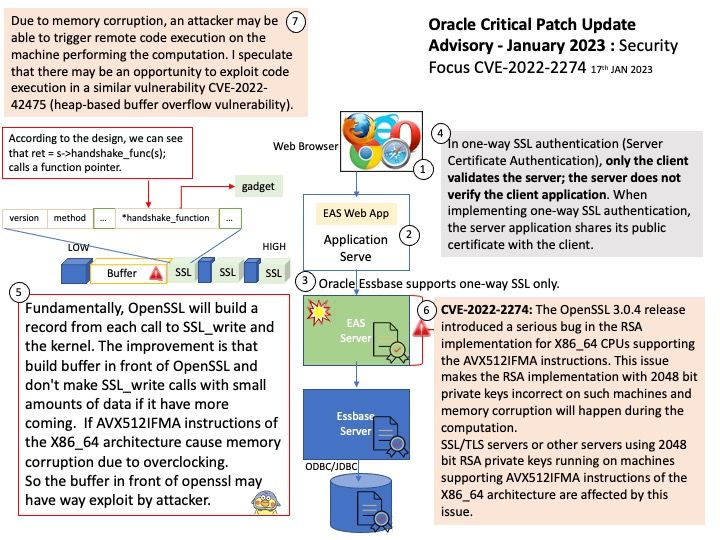
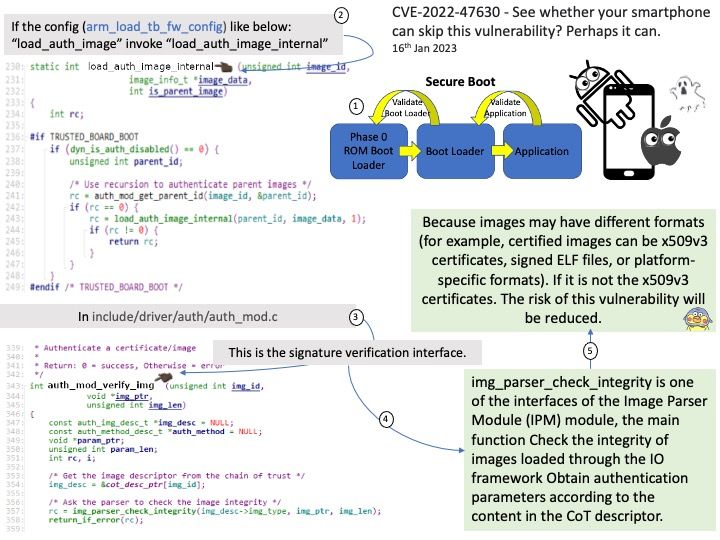
Vulnerability details: cryptography is a package designed to expose cryptographic primitives and recipes to Python developers. In affected versions Cipher.update_into would accept Python objects which implement the buffer protocol, but provide only immutable buffers. This would allow immutable objects (such as bytes) to be mutated, thus violating fundamental rules of Python and resulting in corrupted output. This now correctly raises an exception. This issue has been present since update_into was originally introduced in cryptography 1.8.
My observation: According to CFFI technical manual, if require_writable is set to True, the function fails if the buffer obtained from python_buffer is read-only (e.g. if python_buffer is a byte string). The exact exception is raised by the object itself, and for things like bytes it varies with the Python version, so don’t rely on it. (Before version 1.12, the same effect can be achieved with a hack: call. Therefore it may need to take care of this cryptographic lib again when Python version update.
Official announcement: For details, see the link – https://nvd.nist.gov/vuln/detail/CVE-2023-23931