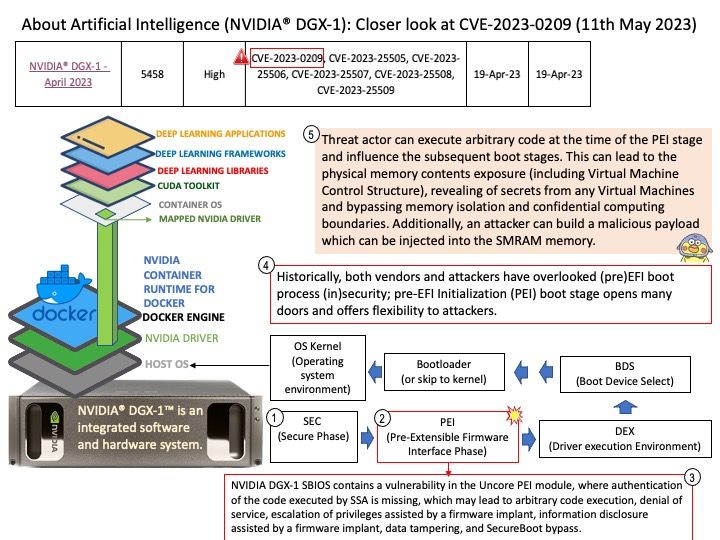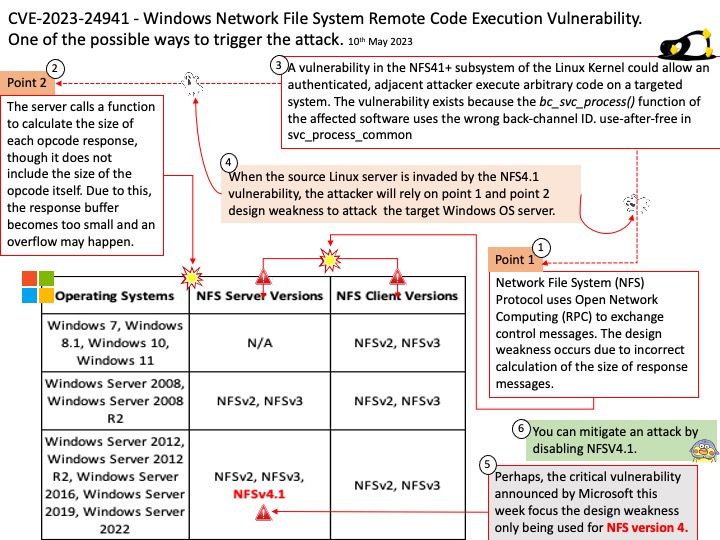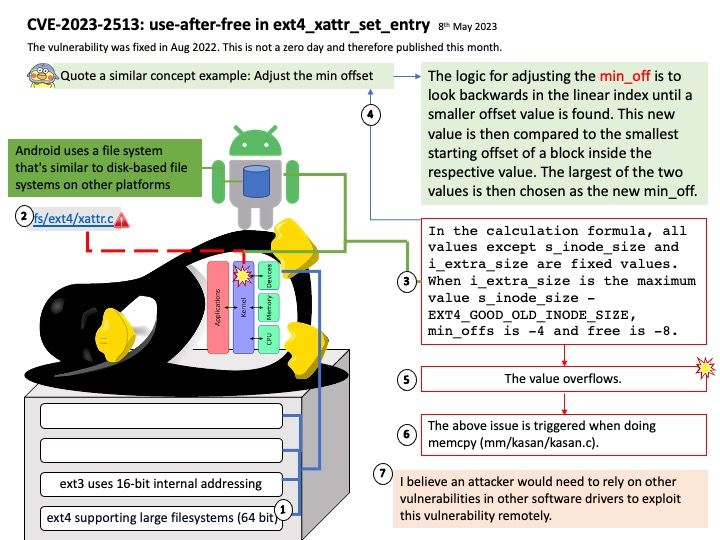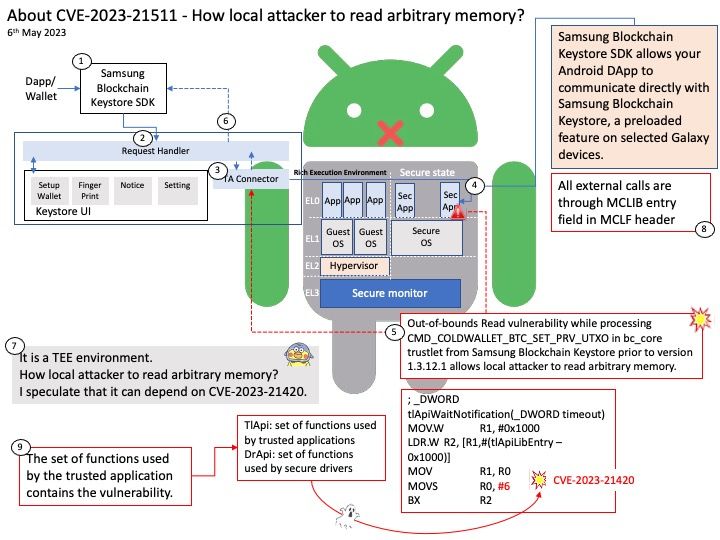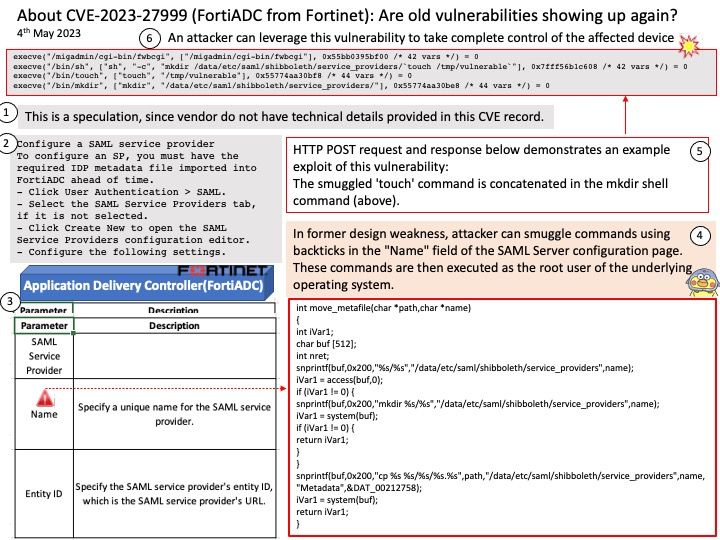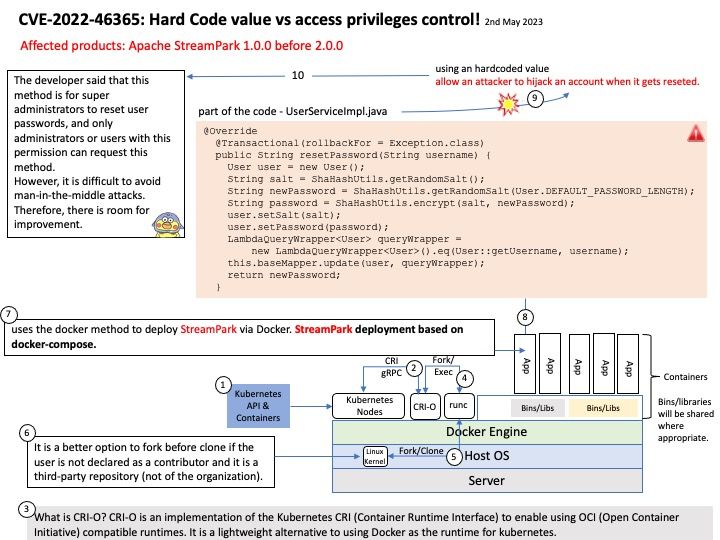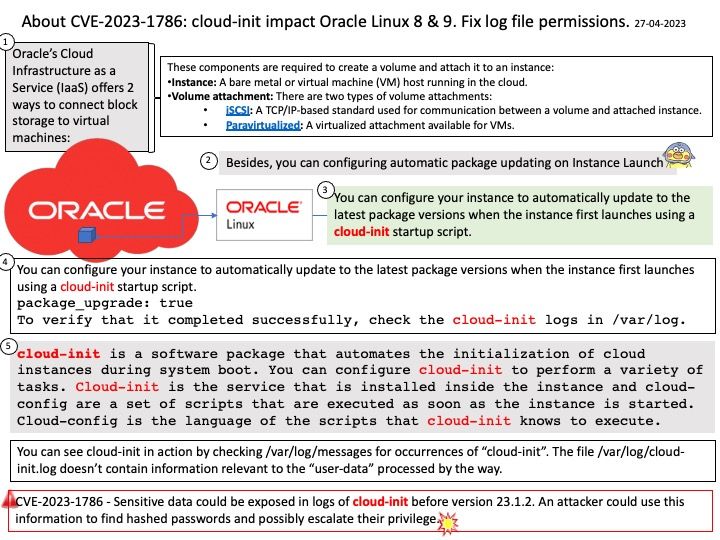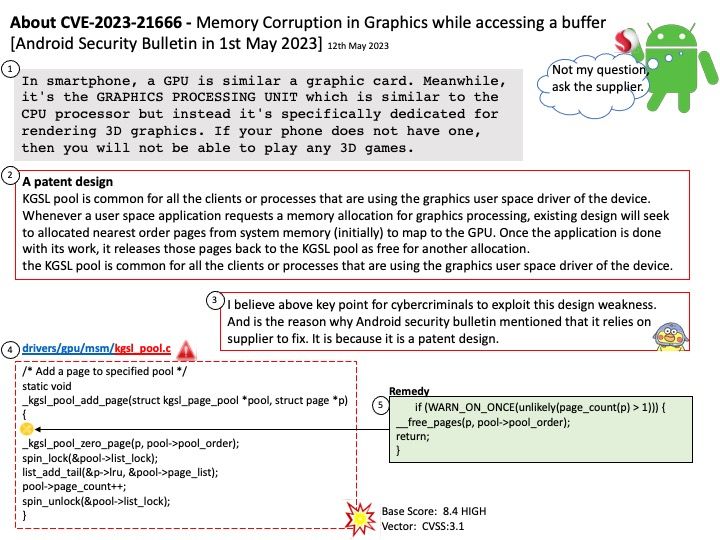
Preface: In smartphone, a GPU is similar a graphic card. Meanwhile, it’s the GRAPHICS PROCESSING UNIT which is similar to the CPU processor but instead it’s specifically dedicated for rendering 3D graphics. If your phone does not have one, then you will not be able to play any 3D games.
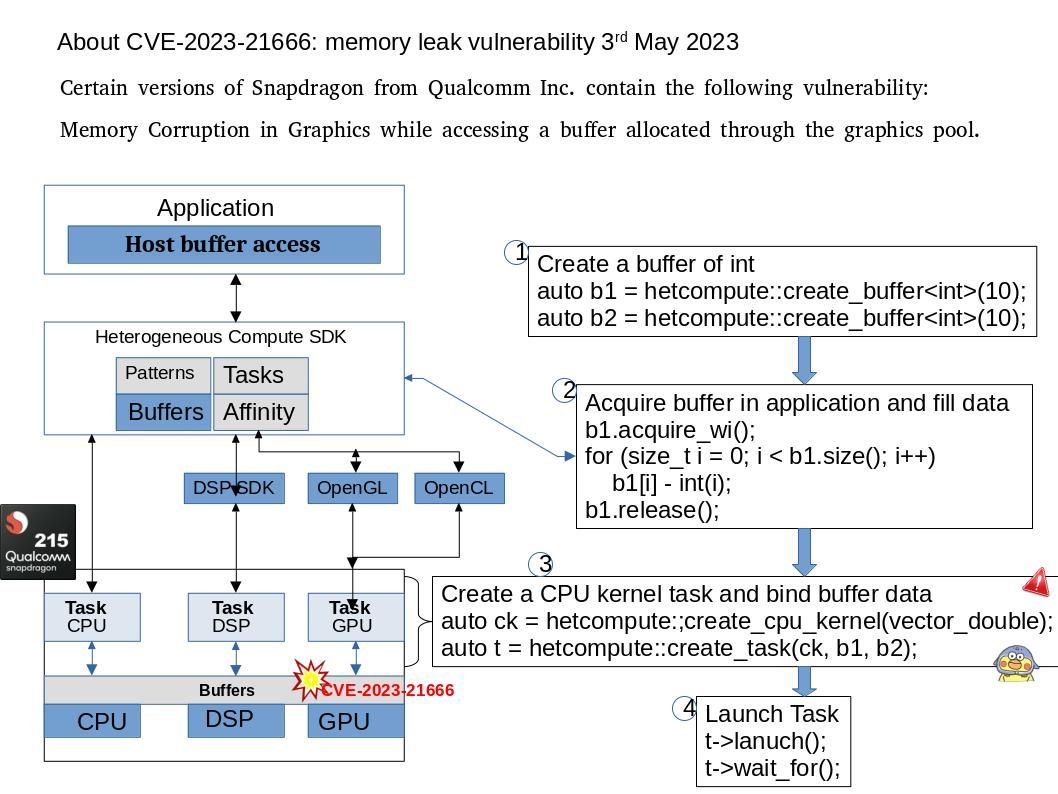
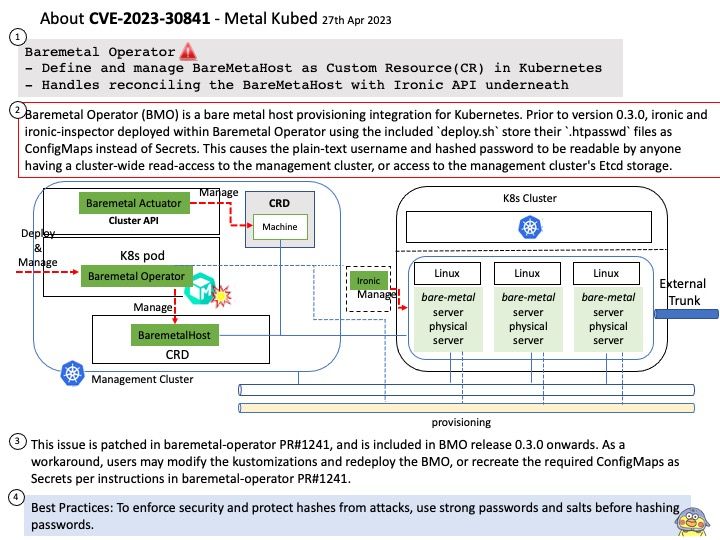
Background: Whenever a user space application requests a memory allocation for graphics processing, existing technology will seek to allocated nearest order pages from system memory (initially) to map to the GPU.
A patent design
KGSL pool is common for all the clients or processes that are using the graphics user space driver of the device. Whenever a user space application requests a memory allocation for graphics processing, existing design will seek to allocated nearest order pages from system memory (initially) to map to the GPU. Once the application is done with its work, it releases those pages back to the KGSL pool as free for another allocation.
the KGSL pool is common for all the clients or processes that are using the graphics user space driver of the device.
Vulnerability details: Memory Corruption in Graphics while accessing a buffer allocated through the graphics pool.
Official announcement – For details, please refer to the link below
Android: https://source.android.com/docs/security/bulletin/2023-05-01
Qualcomm: https://docs.qualcomm.com/product/publicresources/securitybulletin/may-2023-bulletin.html