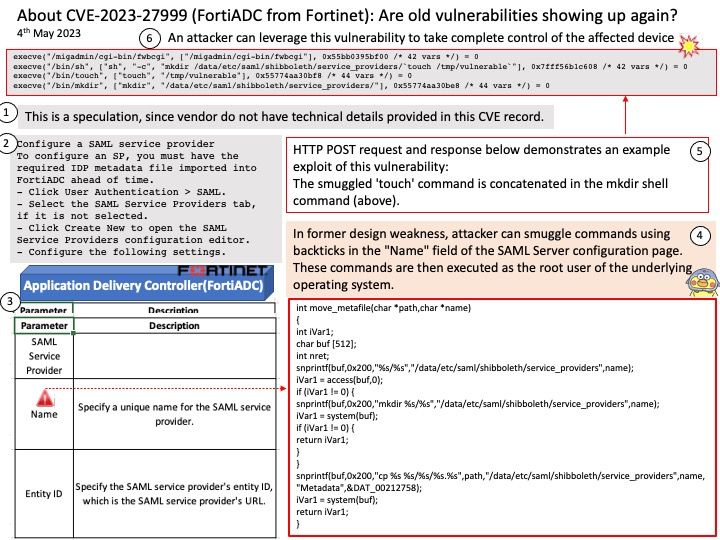
Preface: In former design weakness, attacker can smuggle commands using backticks in the “Name” field of the SAML Server configuration page. These commands are then executed as the root user of the underlying operating system.
This article a speculation, since vendor do not have technical details provided in this CVE record.
Background: FortiADC is an advanced Application Delivery Controller (ADC) that ensures application availability, application security, and application optimization.
For example: Configure a SAML service provider
To configure an SP, you must have the required IDP metadata file imported into FortiADC ahead of time.
- Click User Authentication > SAML.
- Select the SAML Service Providers tab, if it is not selected.
- Click Create New to open the SAML Service Providers configuration editor.
- Configure the settings.
Vulnerability details: An improper neutralization of special elements used in an OS command vulnerability [CWE-78] in FortiADC 7.2.0, 7.1.0 through 7.1.1 may allow an authenticated attacker to execute unauthorized commands via specifically crafted arguments to existing commands.
Official Announcement: See the link below for details – https://cve.report/CVE-2023-27999