Preface: If a website is hacked, cyber criminals don’t get access to your password. Instead, they just get access to the encrypted “hash” created by your password. Talking about hash algotithms, For example, MD5, SHA1, and so on.
The length of a hash is always a constant, irrespective of the length of the input. For example, if we use the MD5 algorithm and hash two strings like “Password123” and “HelloWorld1234”, the final hash will have a fixed length.
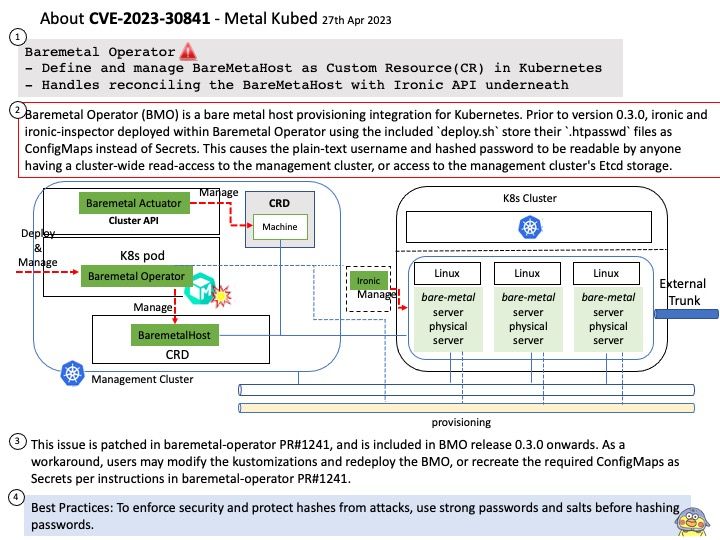
To enforce security and protect hashes from attacks, use strong passwords and salts before hashing passwords.
Background: Metal³ works as a Kubernetes application, it runs on Kubernetes and is managed through Kubernetes interfaces. Metal³ provides Platform9 uses a truly unified operating model by providing bare metal host provisioning integration for Kubernetes.
Bare Metal Operator
- Define and manage BareMetaHost as Custom Resource(CR) in Kubernetes
- Handles reconciling the BareMetaHost with Ironic API underneath
Reference:
The bmc fields contain the connection information for the BMC (Baseboard Management Controller) on the host.
The sub-fields are
• address — The URL for communicating with the BMC controller, based on the provider being used. See below for more details.
• credentialsName — A reference to a secret containing the username and password for the BMC.
• disableCertificateVerification — A boolean to skip certificate validation when true.
Vulnerability details: Baremetal Operator (BMO) is a bare metal host provisioning integration for Kubernetes. Prior to version 0[.]3[.]0, ironic and ironic-inspector deployed within Baremetal Operator using the included deploy[.]sh store their [.]htpasswd files as ConfigMaps instead of Secrets. This causes the plain-text username and hashed password to be readable by anyone having a cluster-wide read-access to the management cluster, or access to the management cluster’s Etcd storage.
Solution:This issue is patched in baremetal-operator PR#1241, and is included in BMO release 0.3.0 onwards. As a workaround, users may modify the kustomizations and redeploy the BMO, or recreate the required ConfigMaps as Secrets per instructions in baremetal-operator PR#1241.
Official details: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-30841