Preface: The NFS 4.1 design flaw was released in August 2019 because it only affected the Linux operating system kernel at the time. It was hard to predict, and now it is going to the Windows platform!
Background: Using the NFS protocol, you can transfer files between computers running Windows and other non-Windows operating systems, such as Linux or UNIX.
NFS in Windows Server includes Server for NFS and Client for NFS. A computer running Windows Server can use Server for NFS to act as a NFS file server for other non-Windows client computers. Client for NFS allows a Windows-based computer running Windows Server to access files stored on a non-Windows NFS server.
Vulnerability detail: Windows Network File System Remote Code Execution Vulnerability
Since vendor do not disclose the technical details. My speculation is shown as below:
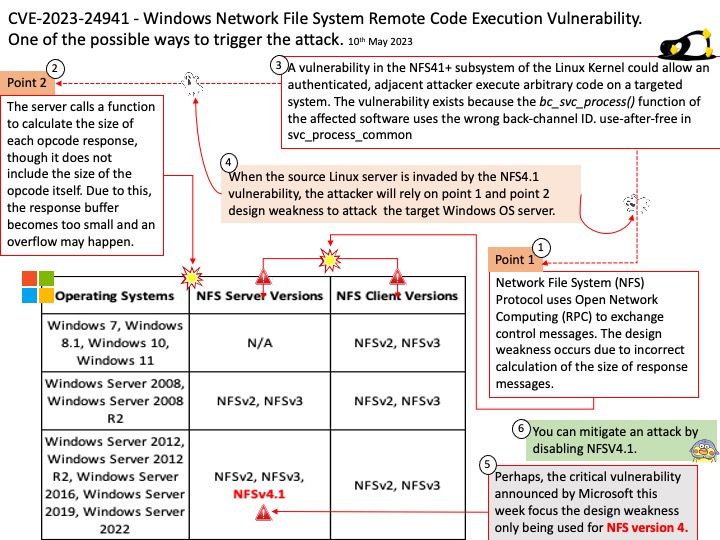
Point 1 – Network File System (NFS) Protocol uses Open Network Computing (RPC) to exchange control messages. The design weakness occurs due to incorrect calculation of the size of response messages.
Point 2 – The server calls a function to calculate the size of each opcode response, though it does not include the size of the opcode itself. Due to this, the response buffer becomes too small and an overflow may happen.
When the source Linux server is invaded by the NFS4.1 vulnerability, the attacker will rely on point 1 and point 2 design weakness to attack the target Windows OS server.
Workaround: This vulnerability is not exploitable in NFSV2.0 or NFSV3.0. Prior to updating your version of Windows that protects against this vulnerability, you can mitigate an attack by disabling NFSV4.1.
Official announcement: For details, please refer to the link – https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-24941