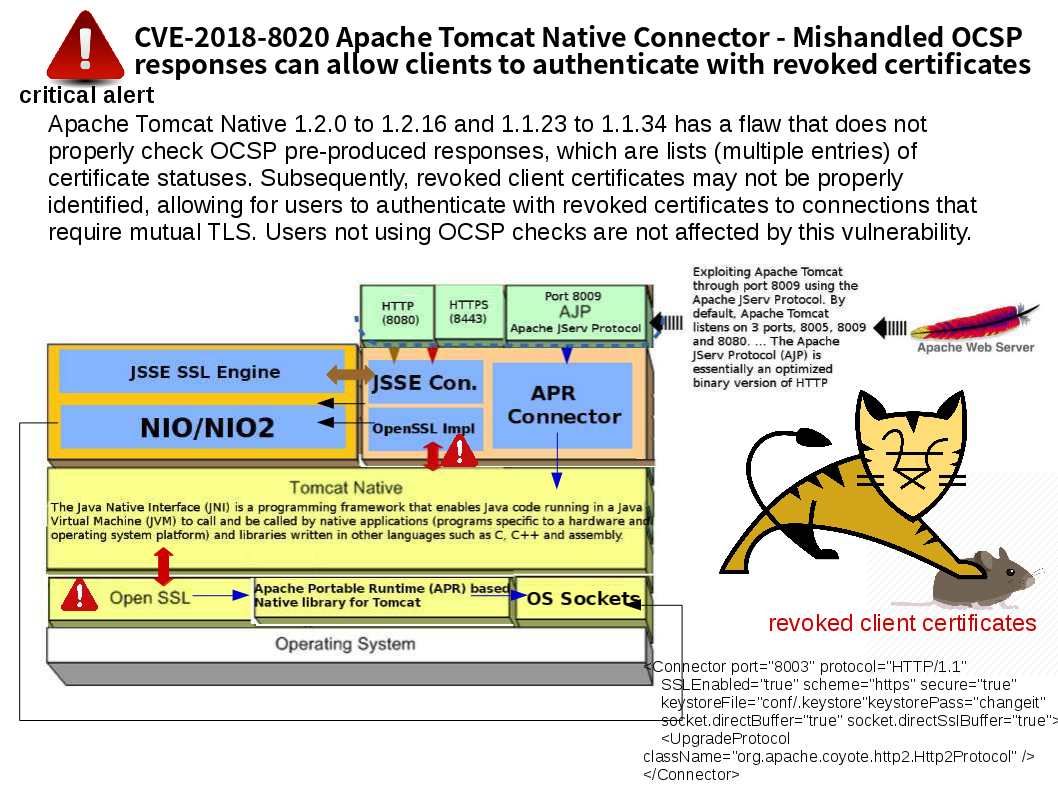
Apache and Tomcat is a perfect match. Their relationship similar pianist and piano. We can’t lack of music in our life. On the other hand, IT world can’t without Apache and Tomcat. But Tomcat is sick today. Found the Apache Tomcat Native (1.2.0 to 1.2.16 and 1.1.23 to 1.1.34) has a flaw that does not properly check OCSP pre-produced responses, which are lists (multiple entries) of certificate statuses. As a result, revoked client certificates may not be properly identified. It allow suspects to authenticate with revoked certificates to connections that require mutual TLS. Native connector use OpenSSL for SSL/TLS function. Refer to attached diagram. If such vulnerability occurs, in the sense that the suspects can control the whole system. It is hard to imagine that how worst will be the IT shop using multiple vhost setup (see below specifications)!
Tomcat 8 supports
one TLS virtual host per connector
one certificate per virtual host
Tomcat 9 supports
multiple virtual hosts per connector (SNI)
multiple certificates per virtual host
For more details, please reference to official announcement.
