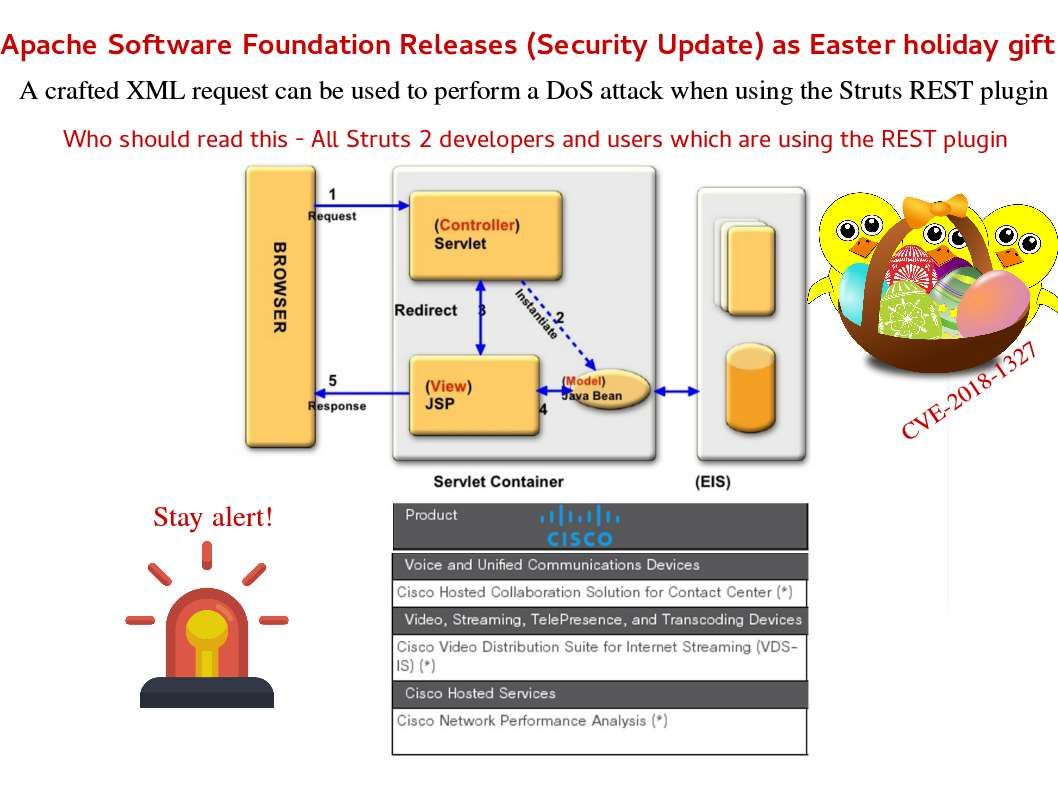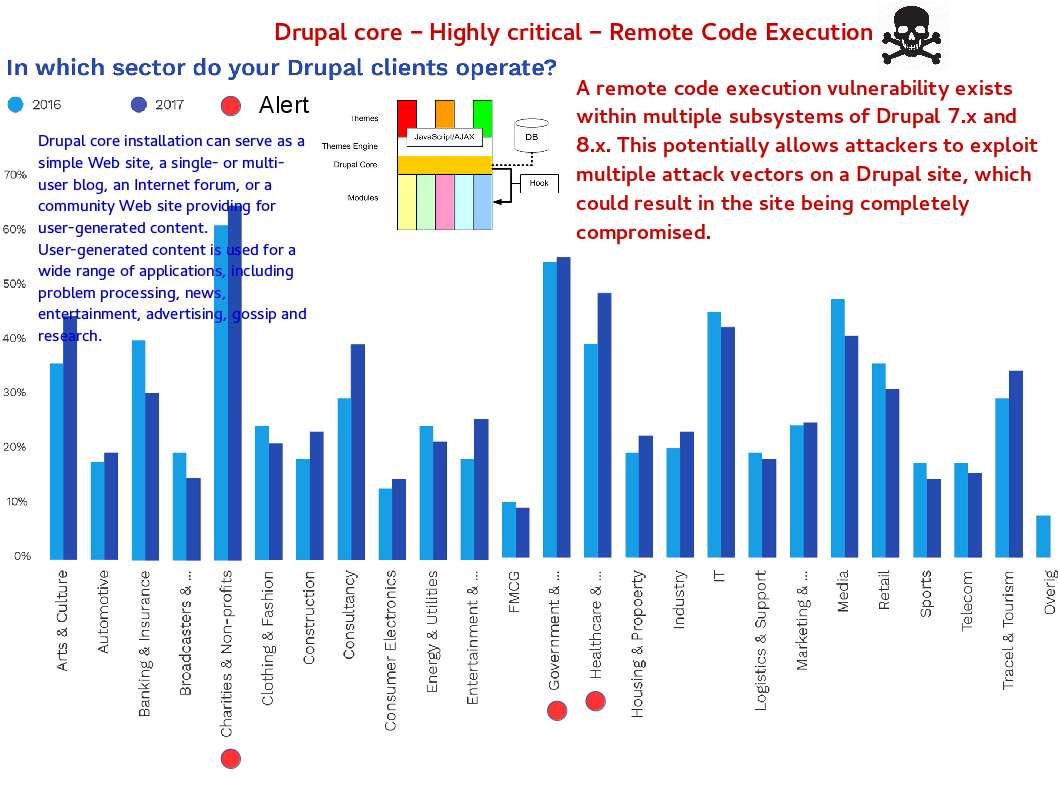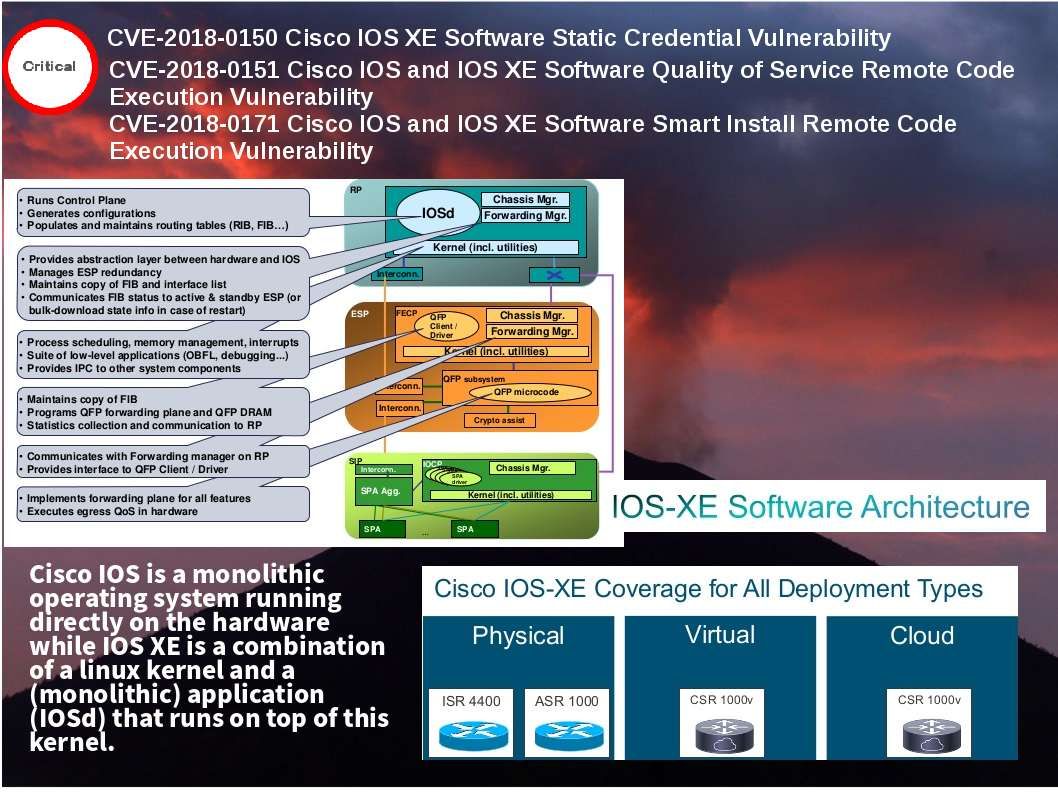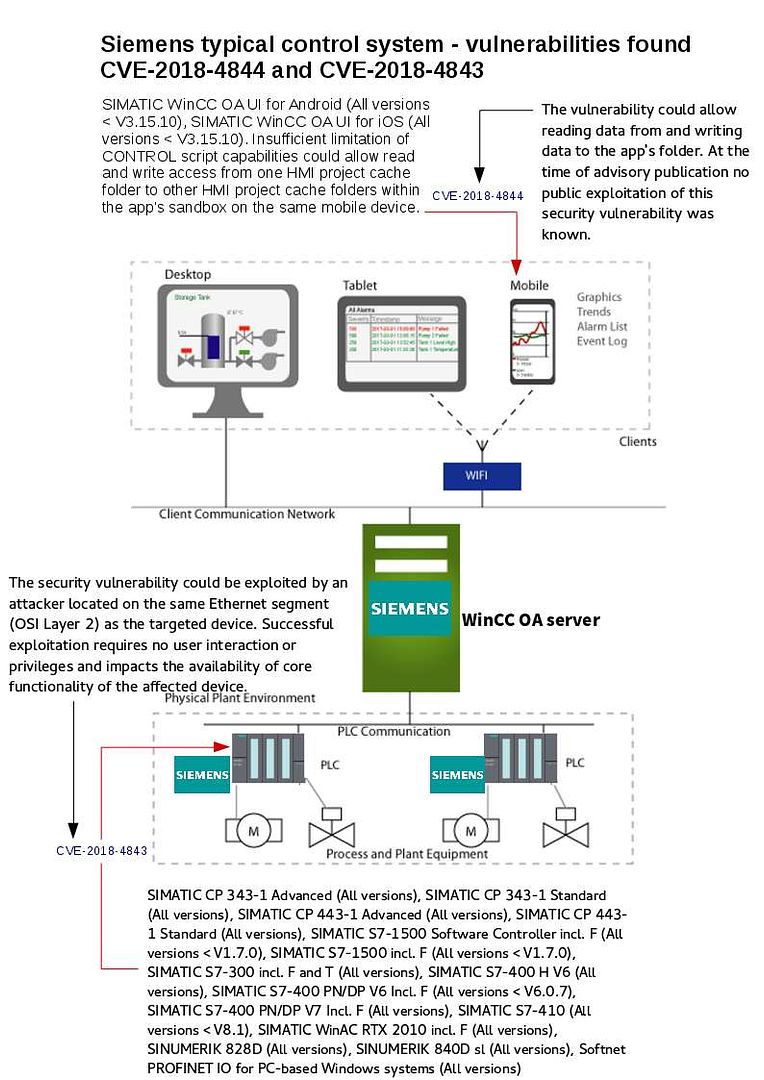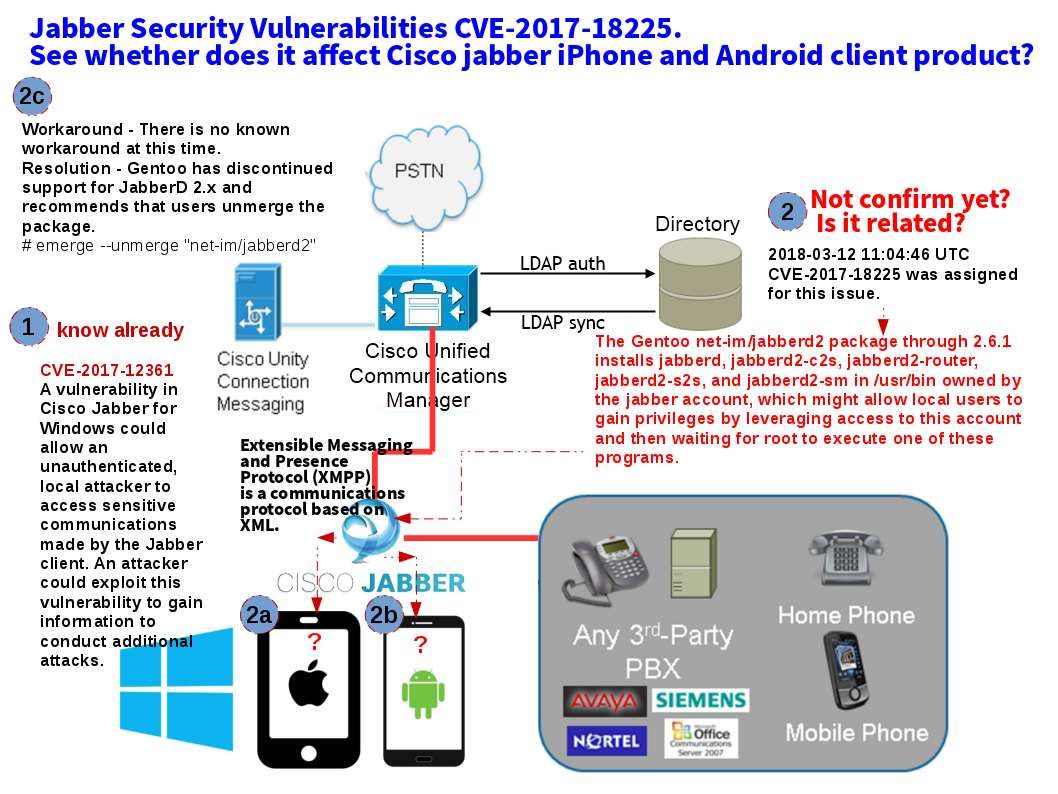
IP telephony integration to IT infrastructure is a main trend in last decade. Following the security best practice, the IP telephony system should be isolated and far away from data network. However there are end user function requirement which causes unified communications manager integrate with Active directory services. A useful function will be activated after active directory integration. For instance a track record will be shown individual communication history. Meanwhile it will enhance the monitor and control process (SOX 403 monitoring and control). Perhaps a pin does not have two points and therefore it is hard to avoid vulnerability happen. For example, Cisco IP telephone working with Microsoft TSAPI last decade. But most recently Android and iPhone growth rapidly. IP telephony vendor will be make use of open source unintentionally. An XMPP client is any software or application that enables you to connect to an XMPP for instant messaging with other people over the Internet. Cisco official announce that there is a vulnerability found on Jabber client from November 2017 (CVE-2017-12361).
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171129-jabber2
The jabber design flaw has been identified this month. The issue is that vulnerability might allow local users to gain privileges by leveraging access to this account and then waiting for root to execute one of these programs. In the meantime, we do not receive announcement release by Cisco (Jabber Security Vulnerabilities CVE-2017-18225). But we keep our eyes open, see whether does it affect Cisco jabber iPhone and Android client product?
CVE-2017-18225 vulnerability details shown as below:
https://security.gentoo.org/glsa/201803-07