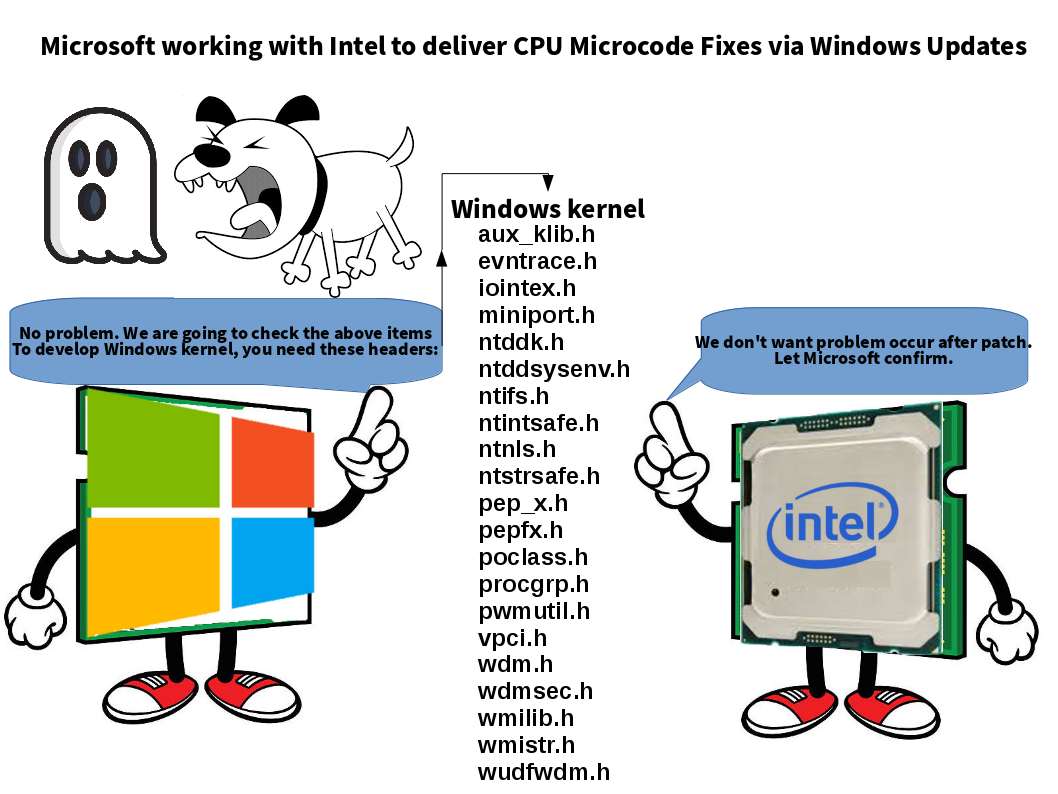
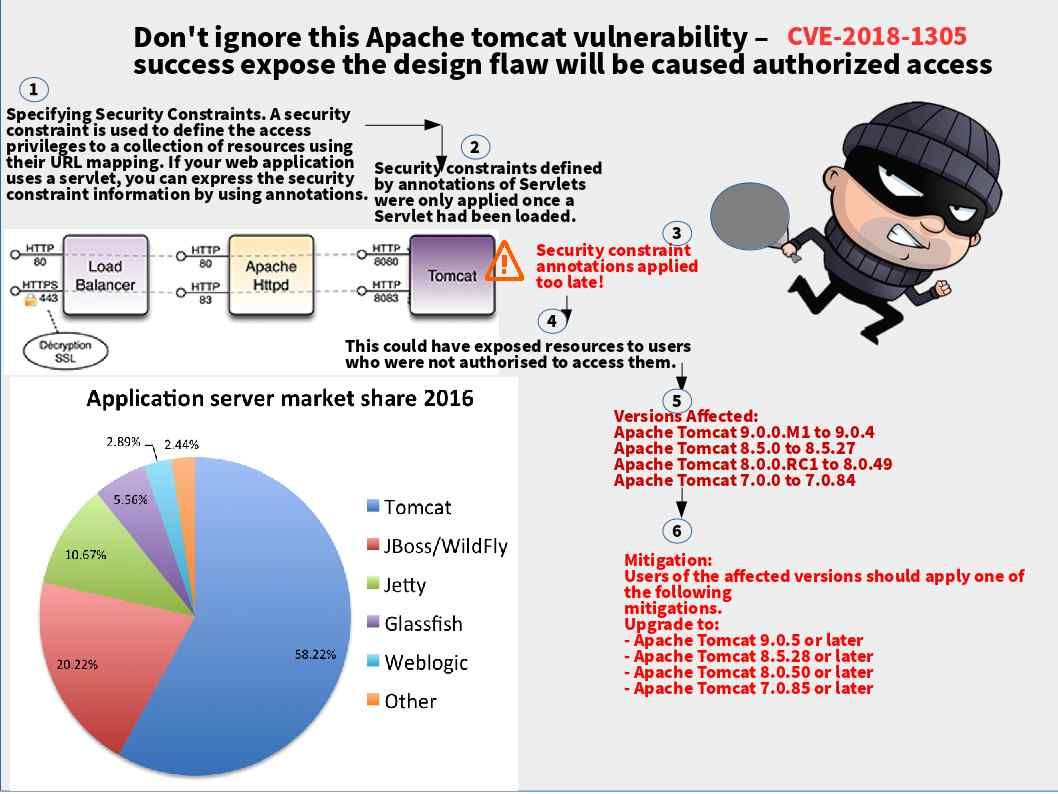
Retrospectively Shibboleth(SAML IDP) found vulnerability on 13th Jan 2018 (CVE-2018-0486). The flaw was that it allows remote attackers to obtain sensitive information or conduct impersonation attacks via a crafted DTD. However there is an additional vulnerability found on Security Assertion Markup Language (SAML). It is the CVE-2018-0489. A multiple SAML libraries may allow authentication bypass via incorrect XML canonicalization and DOM traversal. It looks that it may causes serious headache to many people (webmaster).
During my penetration test engagement in past. I was surprised that no matter airline , financial and retail industries web online application solutions are deployed open source single-sign on resources. An incident occurred in Equifax which awaken the business world that open source application has potential inherent risk. It will jeopardize your firm reputation. Below url is the Security Advisory provided by Shibboleth. You can also find the details on attached picture diagram.