Preface: Drupal is a free and open source content-management framework written in PHP and distributed under the GNU General Public License.
Security Focus:
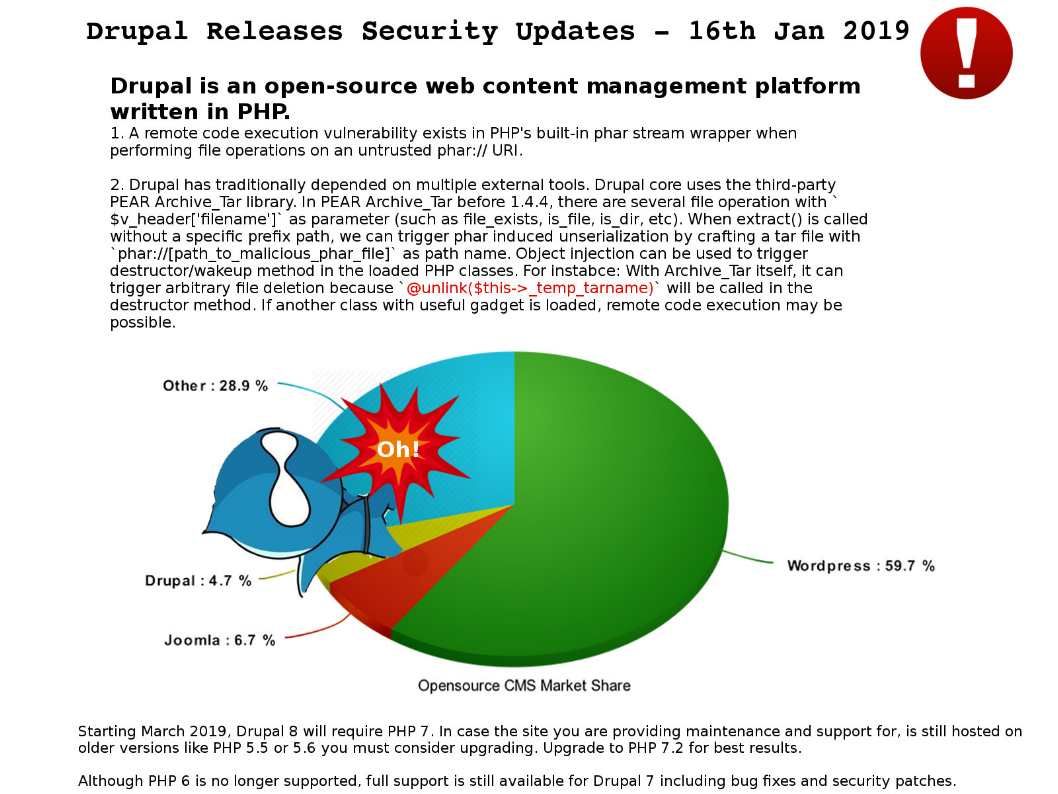
Drupal has traditionally depended on multiple external tools. Drupal core uses the third-party PEAR Archive_Tar library. In PEAR Archive_Tar before 1.4.4, there are several file operation with $v_header['filename'] as parameter (such as file_exists, is_file, is_dir, etc). When extract() is called without a specific prefix path, we can trigger phar induced unserialization by crafting a tar file with phar://[path_to_malicious_phar_file] as path name. Object injection can be used to trigger destructor/wakeup method in the loaded PHP classes. For instabce: With Archive_Tar itself, it can trigger arbitrary file deletion because @unlink($this->_temp_tarname) will be called in the destructor method. If another class with useful gadget is loaded, remote code execution may be possible.
Official announcement:
Drupal core Arbitrary PHP code execution (Critical) – https://www.drupal.org/sa-core-2019-002
Drupal core Third Party Libraries vulnerability (Critical) – https://www.drupal.org/sa-core-2019-001