Preface
We heard that the new age transformation is coming. As a result it transform the traditional military weapons to electronic codes. The computer technologies such as DDOS (Distributed denial of services), malware and virus similar a killer. It can disrupt the financial activities, daily network communication and health care services. An idea bring to our attention on world war II history was that classic military power result destroyed everything (mankind and properties). But re-built the society and operation after war. It is a harsh and difficult mission! From technical point of view, the victorious might stand on ethics view point to assists defeated side to rebuild the business and economic system. As a matter of fact, the distruction level of war created by military weapon especially missile it is hard to evaluation. And this is the reason let’s cyber warfare appears in coming future! But it started already!
Analytic result on technical articles about cyber warfare
In regards to my study on technical article issued by CSS Eth Zurich (The Center for Security Studies (CSS) at ETH Zurich).The analytic result highlights serveral key factors of Cyber warfare . Cyber warfare was cheaper than traditional military force. It provides a “cleaner” (with less or no bloodshed) suitation. No doubt that less risky for an attacker than other forms of armed conflict. The analytic result defines 5 different types of cyber conflict during their study. They are Cyber War, Cyber Terrorism, Cyber Espionage, internet crime and cyber vandalism.
The specific feature of cyber weapon (in between country to country)
I was sometimes confused with the headline news on prediction on cyber technology war. The questions on my mind is that how electronic weapon or cyber weapon replacing traditional military facilities? Think it over, the appropriate technique might adopted target into the following criteria (see below):
The capabilities of cyber attack techniques ( A transformation of traditional military force)
| Type |
Attack technology |
Functional feature – objective |
Target – Environment |
Remark: |
| Cyber Vandalism, Cyber War |
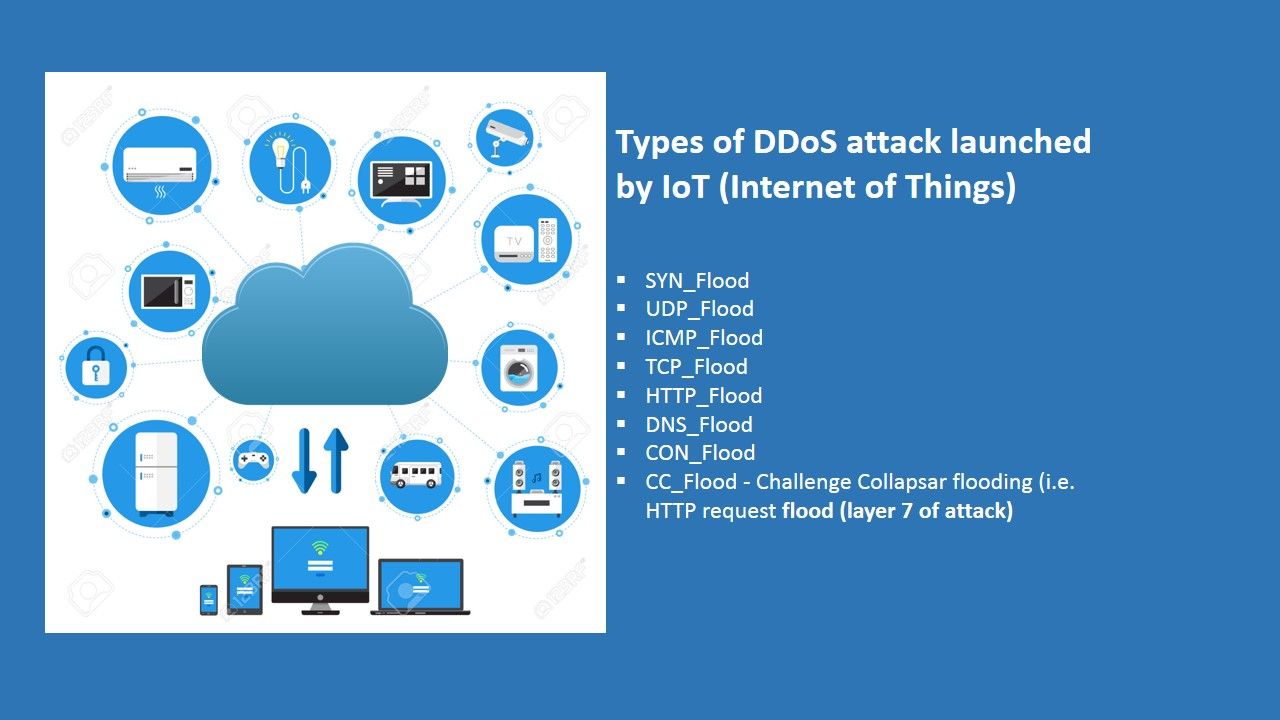
IOT & BOTNET (DDOS technique) |
Services suspension – electronic communication services (IP-Telephony) |
Bank, Fund House , Stock Exchange |
|
| Cyber Espionage |
Malware |
Information gathering |
Bank, Fund House, Stock Exchange & government sector |
|
| Cyber War, Cyber Vandalism |
Ransomware |
Services suspension important facility fucntion |
nuclear facility , Airlines,TV broadcast station, Radio broadcast station & military facility |
Ransomware feature contained facility to supspend the computer services. Besides it capable listen to the instruction of C&C server. On the other hand, the attacker can resume the services once they win the battle. |
| Traditional military force |
Bomb |
Services Suspension on important facility function and destroy permanently |
nuclear facility, military facility, power station, airport & communiation facility (Digital phone system) |
|
| Internet Crime, Cyber war |
Email phishing and Scam email message |
Carry out psychological warfare, implant malware activities in order to fulfill their objective |
nuclear facility, military facility, power station, |
|
Let us dig out one of the attack technique to see how the cyber technology feature fulfill the goal of the cyber warfare features .
Do you think Ransomware is founded by military department?
The first ransomware appear in the world on 1989. A biologist Joseph L. Popp sent 20,000 infected diskettes labeled
“AIDS Information – Introductory Diskettes” to attendees of the World Health Organization’s international AIDS conference.
But after 90 reboots, the Trojan hid directories and encrypted the names of the files on the customer’s computer.
To regain access, the user would have to send $189 to PC Cyborg Corp. at a post office box in Panama.
In 2006, former President George W. Bush was increasingly worried about Iranian efforts at enriching uranium, and ultimately, its hopes to build an atomic bomb. The goal of Stuxnet is going to destroy Iraq nuclear facilities driven by US government. The rumors were told Stuxnet malware destroyed roughly one-fifth of Iran’s centrifuges in 2009.
An unconfirmed information stated that there is a separate operation called Nitro Zeus, which gave the US access into Iran’s air defense systems so it could not shoot down planes, its command-and-control systems so communications would go dead, and infrastructure like the power grid, transportation, and financial systems.
Speculation:
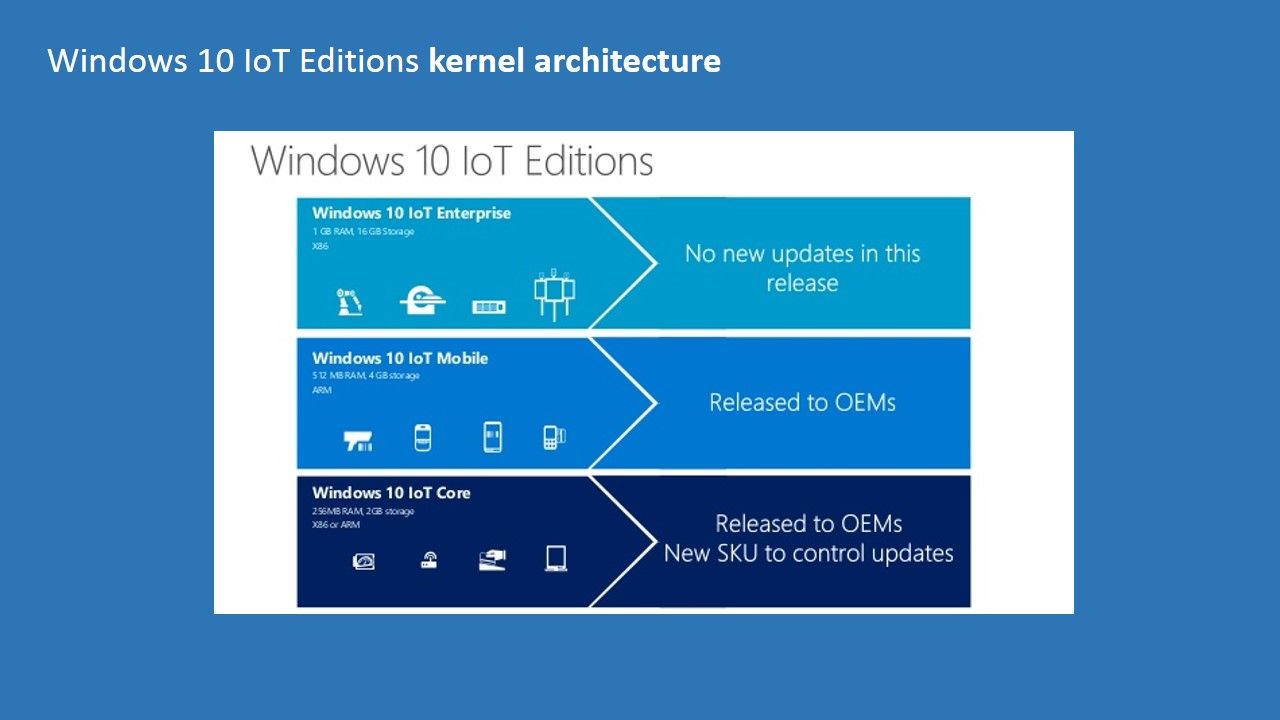
WannaCry infection using EternalBlue, an exploit of Windows’ Server Message Block (SMB) protocol. The U.S. National Security Agency (NSA) had discovered the vulnerability in the past, but used it to create an exploit for its own offensive work, rather than report it to Microsoft. As we know nuclear power facilities control system OS platform relies on Microsoft OS system (see below articles). It may causes people think is there any secret action hide by NSA (National Security Agency). He aroused my interest in questioning who is the key figure to spread WannCry ransome? It looks that there is similarity with Stuxnet worm infection in 2009. Since we all fool by NSA at that time let your computer workstation transform to a cyber army then attack USA enemy. Do you think wanncry is the rehearsal of test or pilot run?
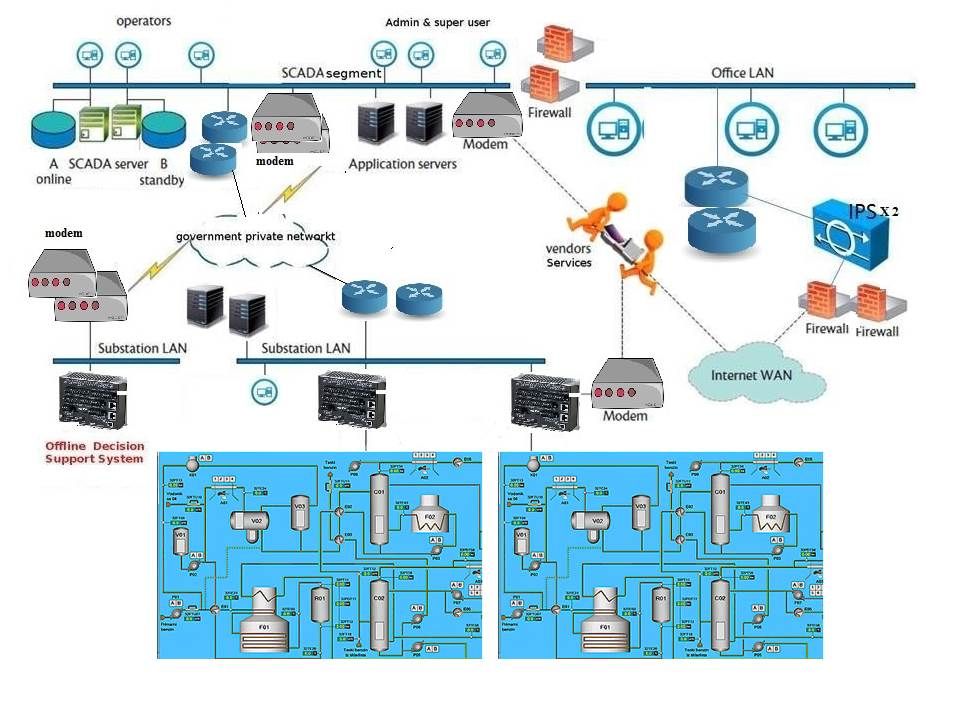
Malware vs. nuclear power: Do you think SCADA system is the culprit of attack on nuclear power system?
Below diagram is my imagination of the modern nuclear facility environment. The SCADA system pay a key role in nuclear power facility. Ransomeware have capabilities to suspend the services of this facilities. It doesn’t need to destroy anything but the services will be totally shut it down the services. We have seen the real example in UK health care services as a reference. I will stop written here. Should you have any queries, I will try my best to written more in future.
Supplement – The other side of the story on cyber attack (Electronic war between countries) – 13th June 2017
As said on above discussion topic, since it looks not interest to visitors on reflection of comments on feedback. However there is something on my mind need to share.
North Korea President Kim’s intention show to the world of his governance power. He is in frequent to demonstrate his military power cause US government concerns his equalize of military power in the world. To be honest, it is hard to equal the military and economics power as of today. For instance China nearly become the 1st business economic leader. We all know United state is the leader in this moment. However their economic operation chain should have difficulties to do the 2nd round of transformation. Because some of their capital business and business economy contained made in China element. Since North Korea on finance and business economy are weak. President Kim did such things seems not make sense. I did not visit North Korea however a lot of news on TV might speculate their current situation. I strongly believed that their nuclear facility might operation in 60’s fashion. The SCADA system not possibly supply by Siemens. But learn and develop a windows based SCADA system not difficult. From information point of view, North Korea nuclear facilities might relies on window for Control Systems instead of Linux for control system. And therefore Ransomware type attack can specifics shot the target. Meanwhile the business industry from North Korea all work with Microsoft OS in daily life.
Below are the hints how to eliminate the risks issued by SCADA system vendor. Any interest?
Process control vendors require:
1. A system with a minimal attack surface, so that biweekly or monthly patches are not required
2. A consistent programming interface that will not change every four to five years, requiring a complete rewrite of their software
3. An environment that can be quickly and safely “locked down” to reduce the risk from hacking
4. A system with limited network access, only through specific ports to reduce the risk of network based attacks
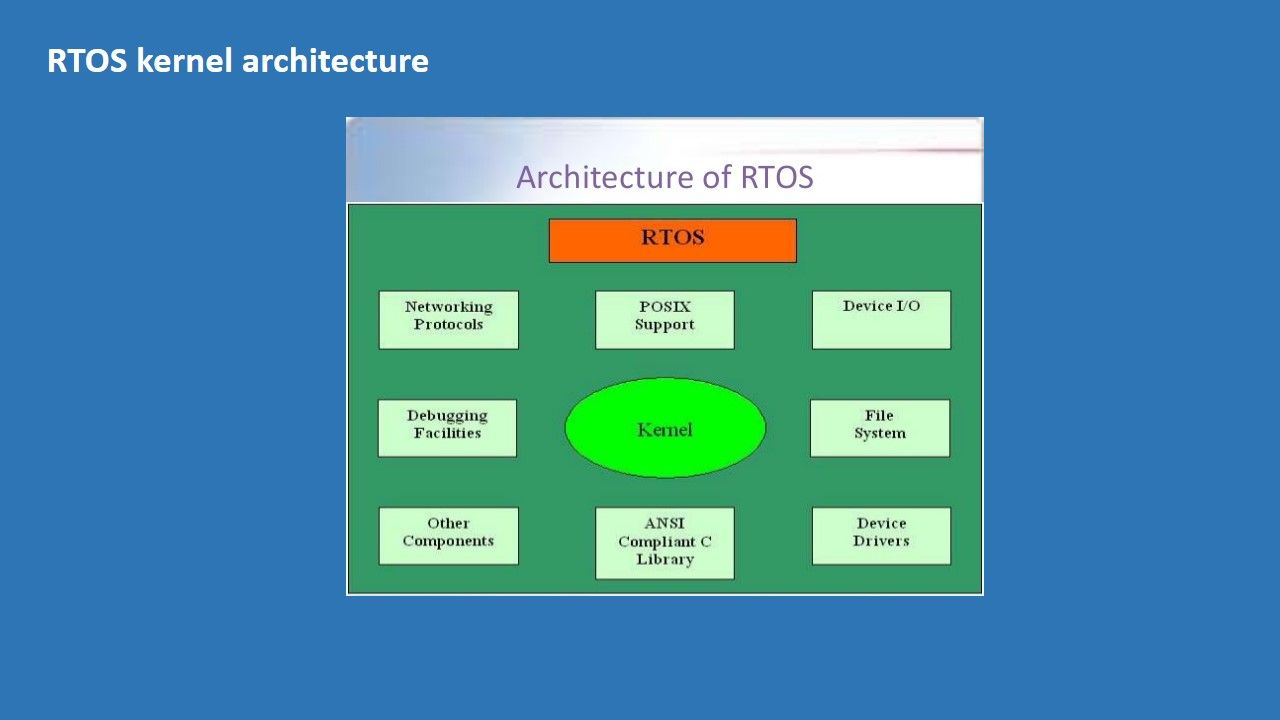
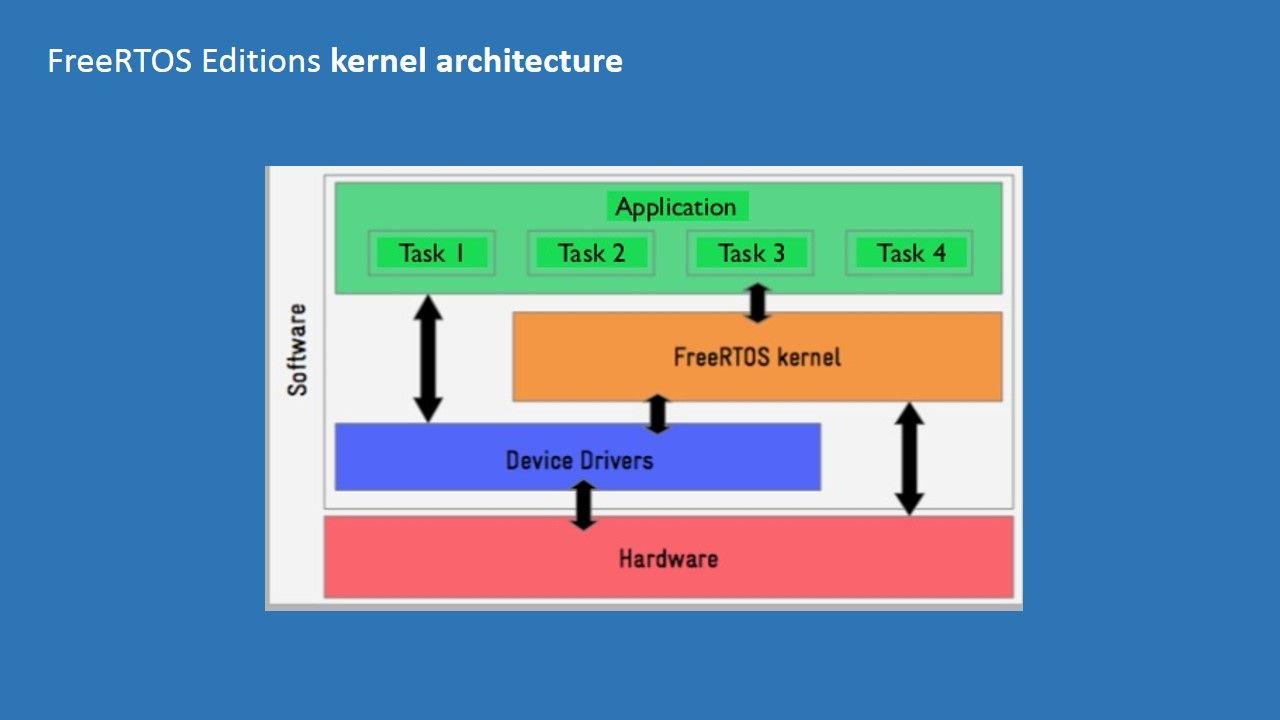
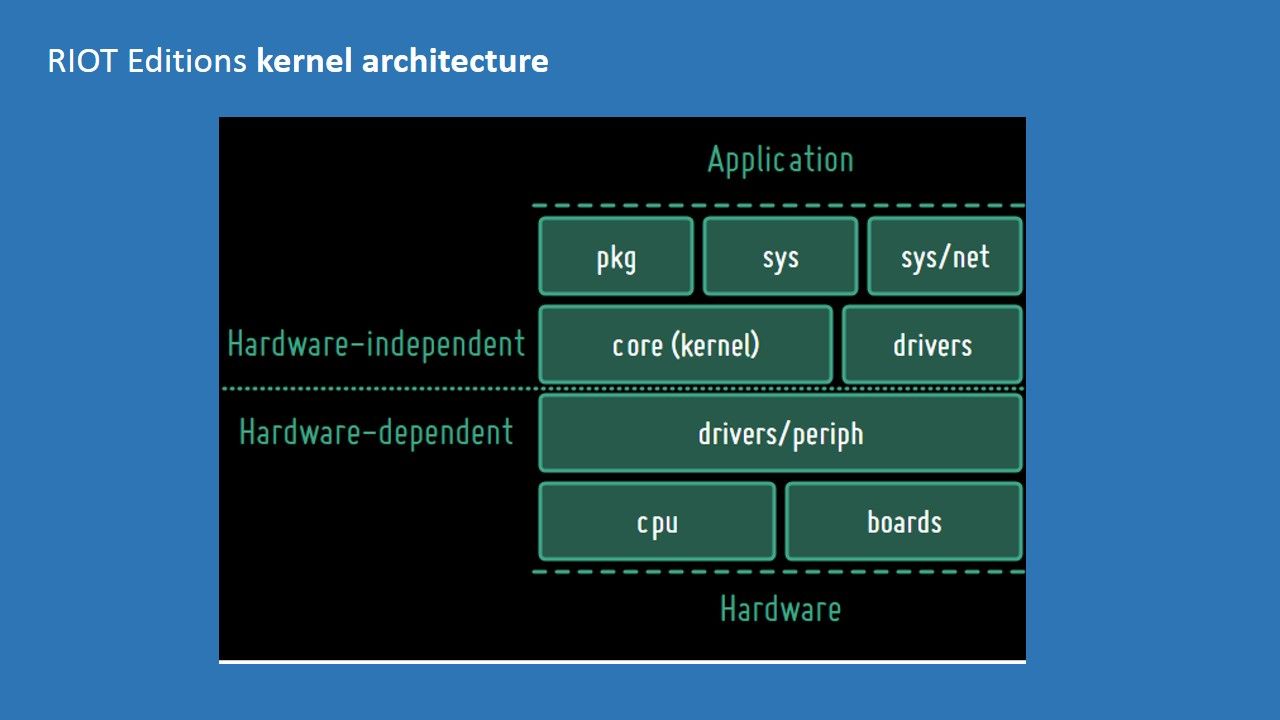
5. Support for priority-based multi-tasking, preferably a real-time operating system (RTOS) that supports hard real-time requirements
6. A robust ecosystem of utilities and tools to make development, installation, debugging, and maintenance as easy as it is on consumer systems.
End of this topic