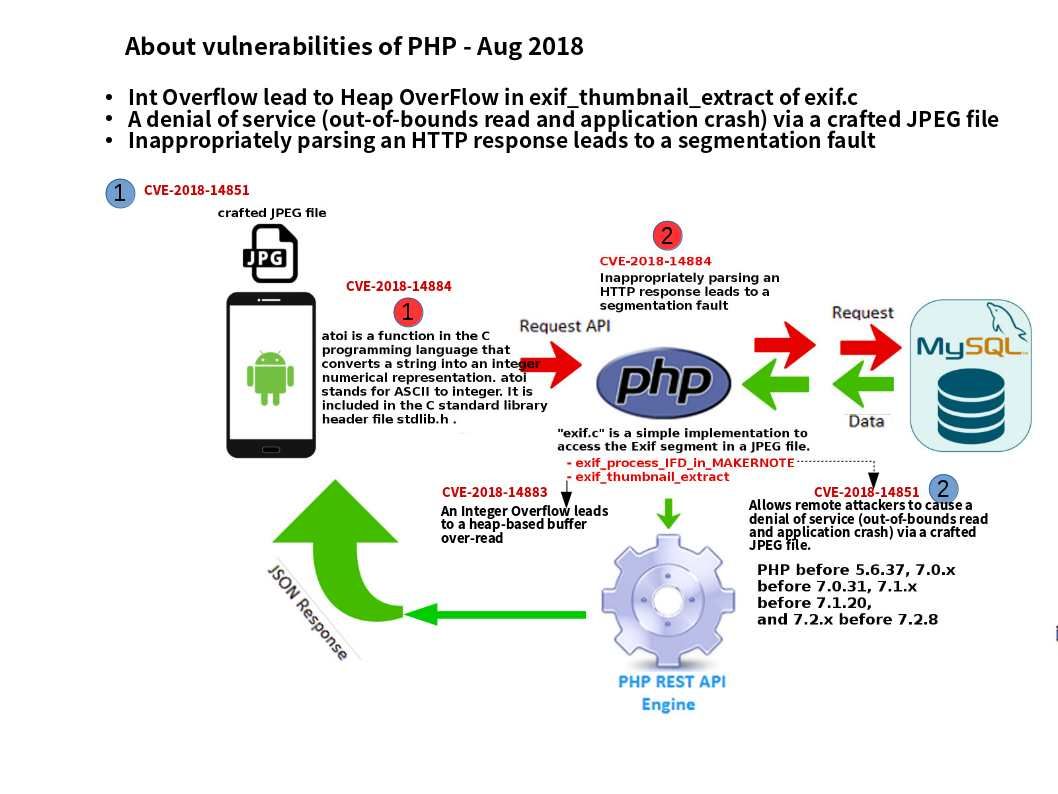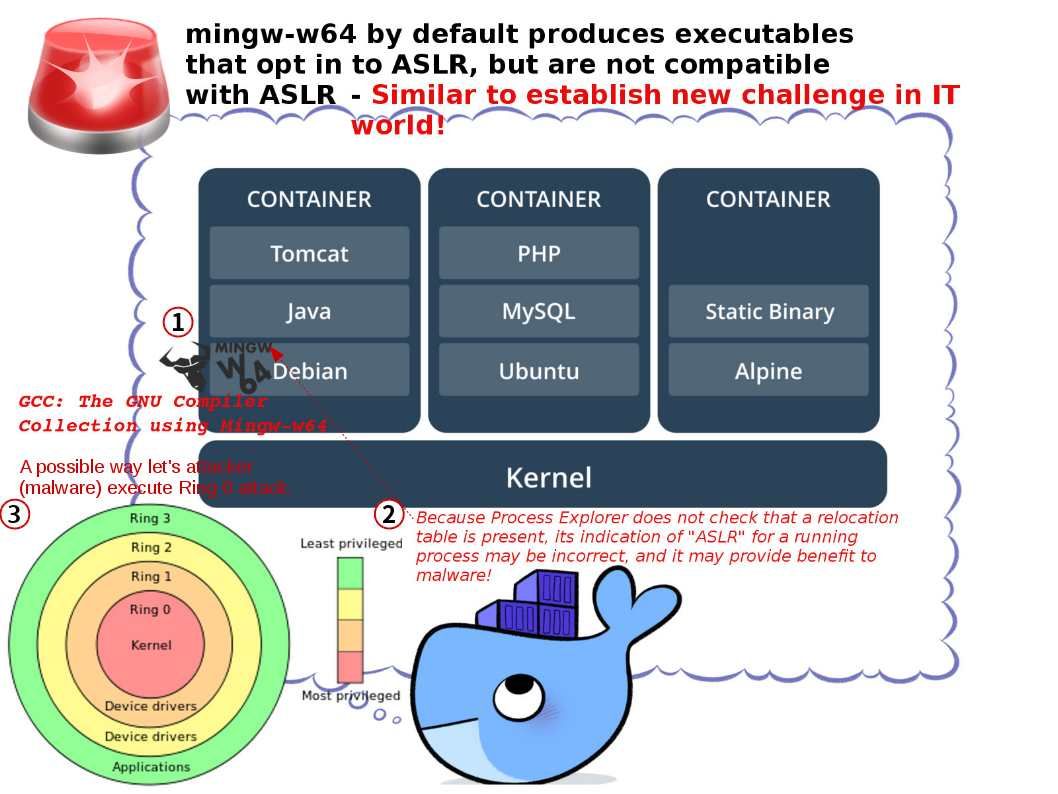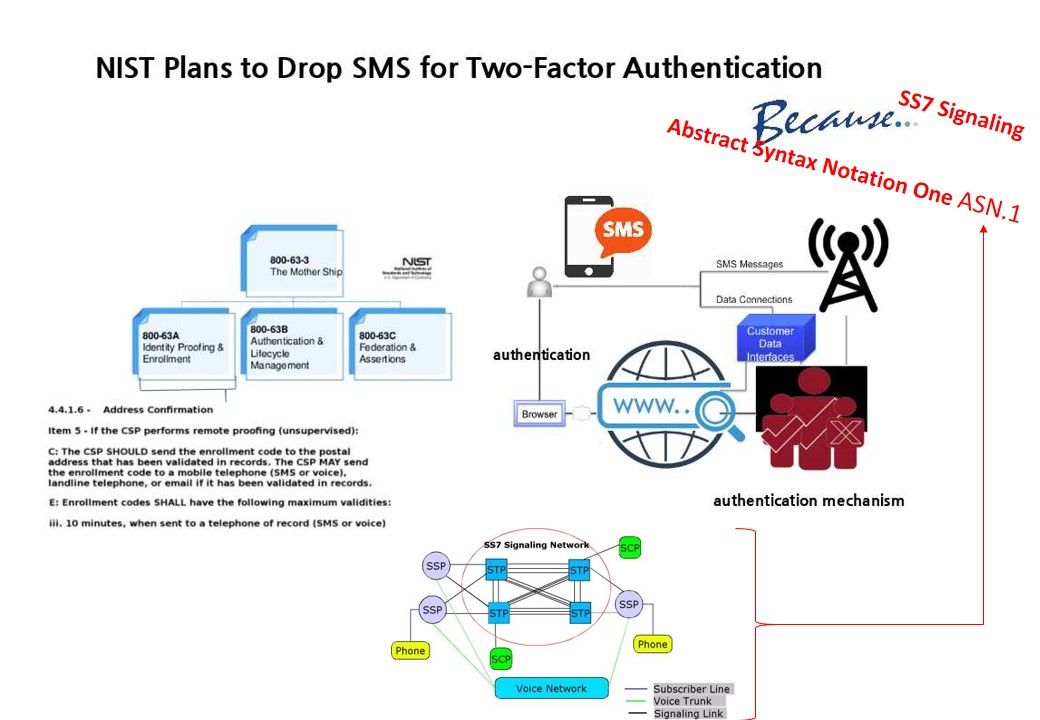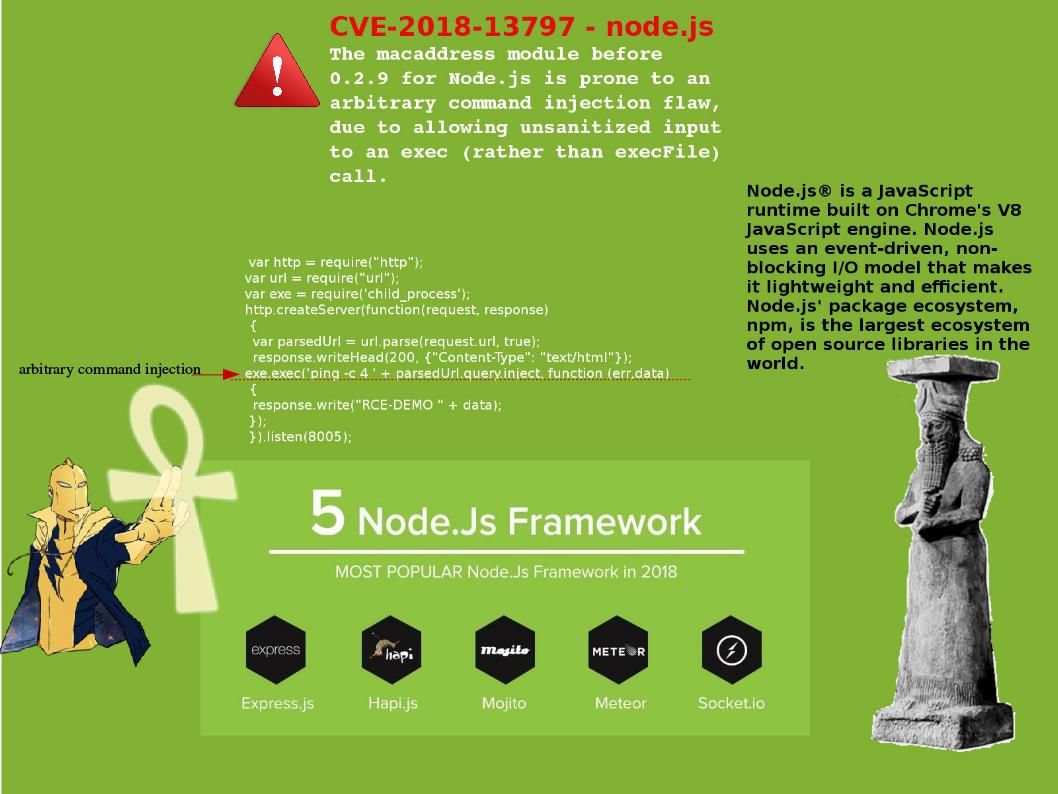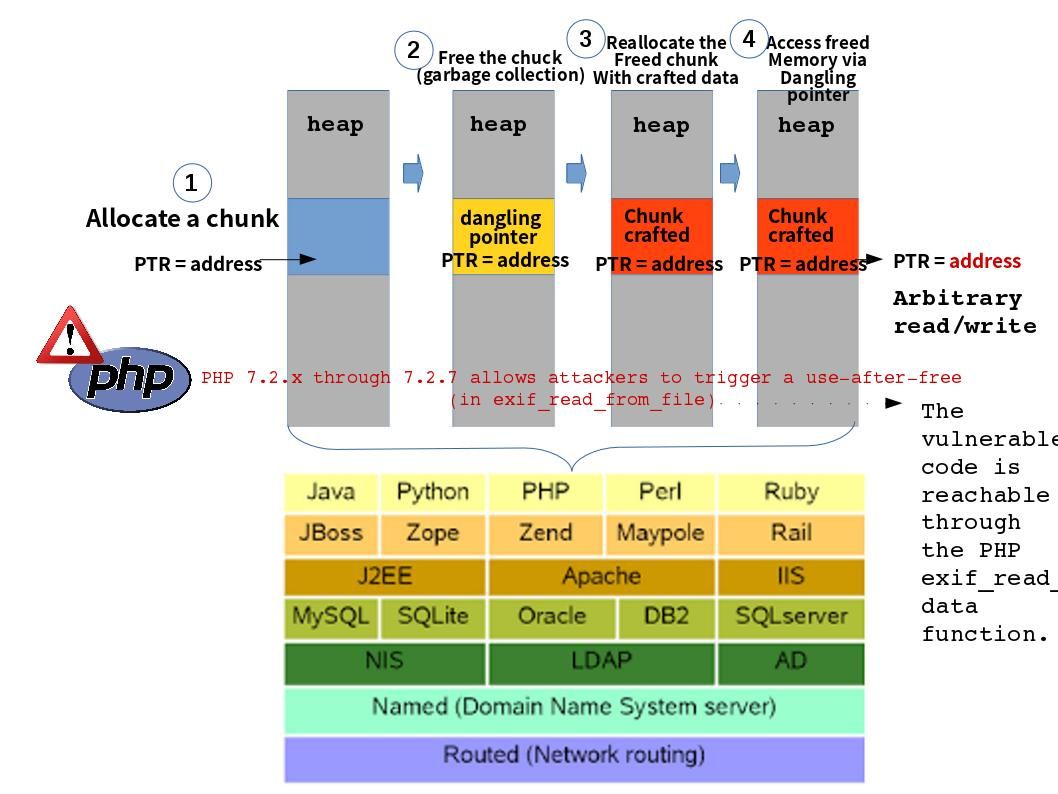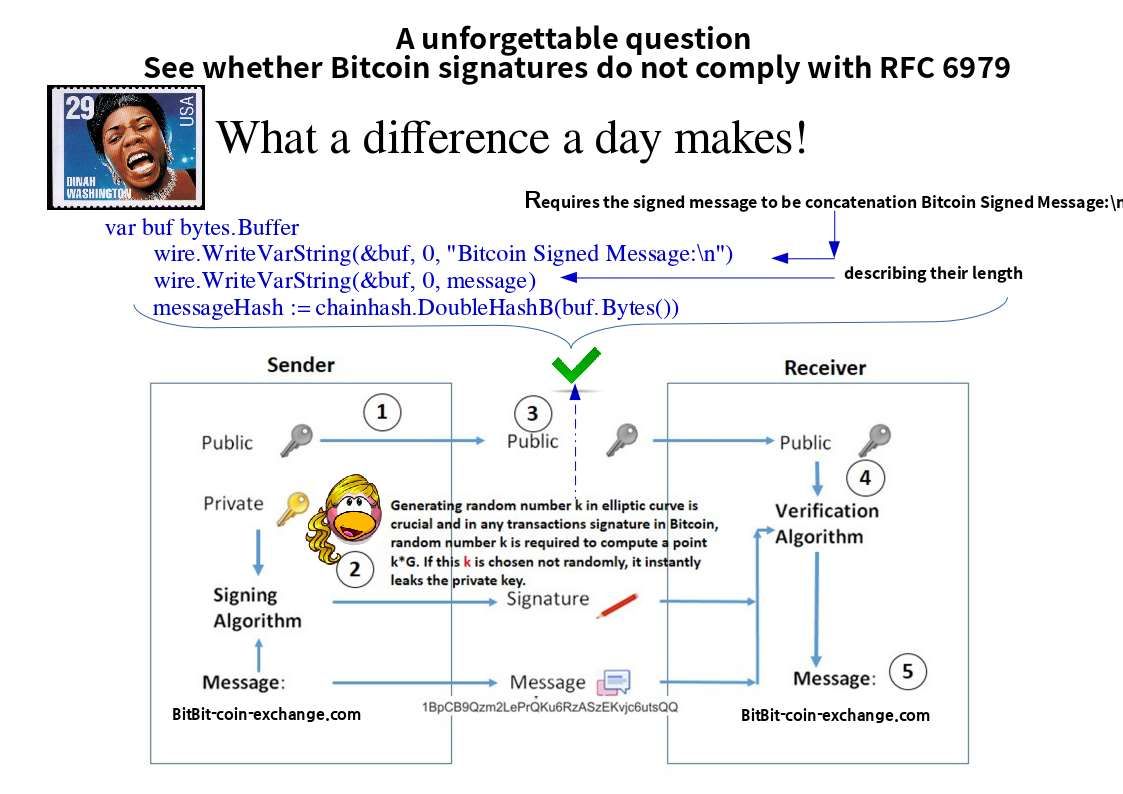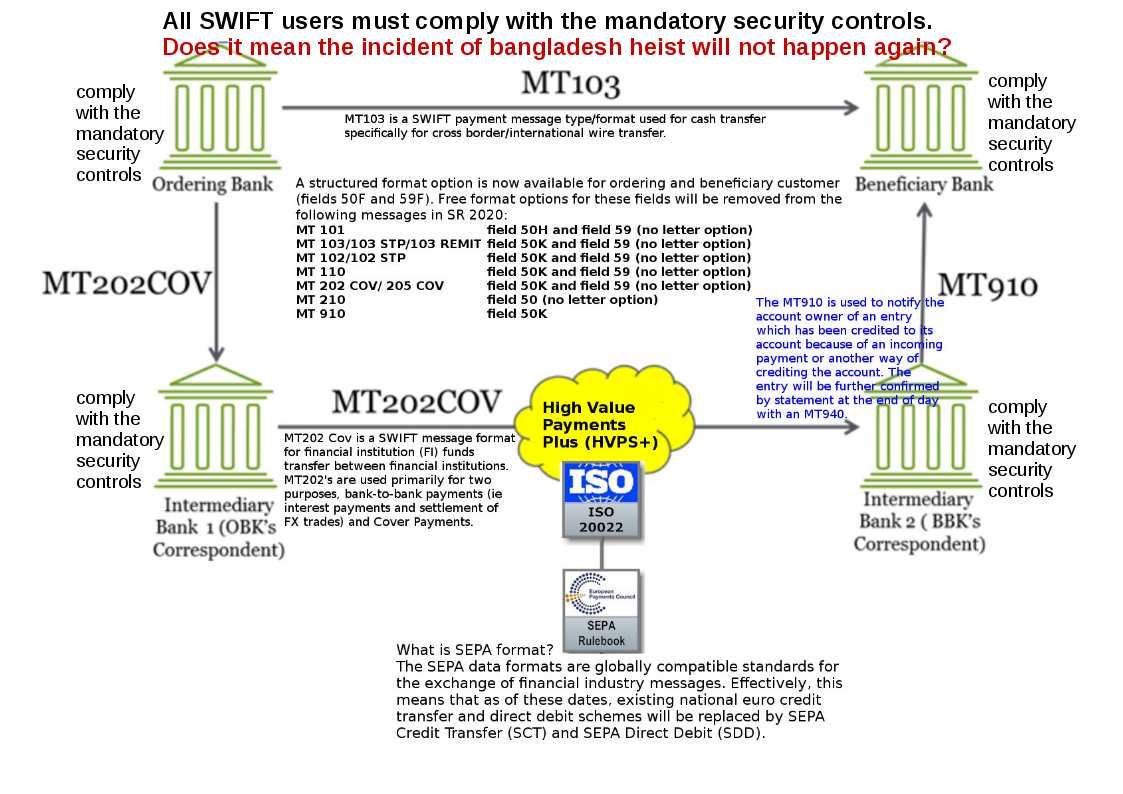
Preface:
All SWIFT users must comply with the mandatory security controls by the end of 2018.
Objective:
Introduction of new controls or guidelines will take account of strong cybersecurity practices that address the currently known new and arising threats in order to pragmatically raise the security bar.
Technical details:
Mandatory Security Controls
1. Restrict Internet Access and Protect Critical Systems from General IT Environment
2. Reduce Attack Surface and Vulnerabilities
3. Physically Secure the Environment
4. Prevent Compromise of Credentials
5. Manage Identities and Segregate Privileges
6. Detect Anomalous Activity to Systems or Transaction Records
7. Plan for Incident Response and Information Sharing
Observation:
Swift system is on the way do the enhancement continuously. But do you think such continuous program will be effectively avoided cyber security attack? For instance Bangladesh heist.
It is hard to tell what is the next cyber attack challenge in the moment. Let’s keep our eye open. Stay tuned!
Reference: