Original posted 06/06/2024
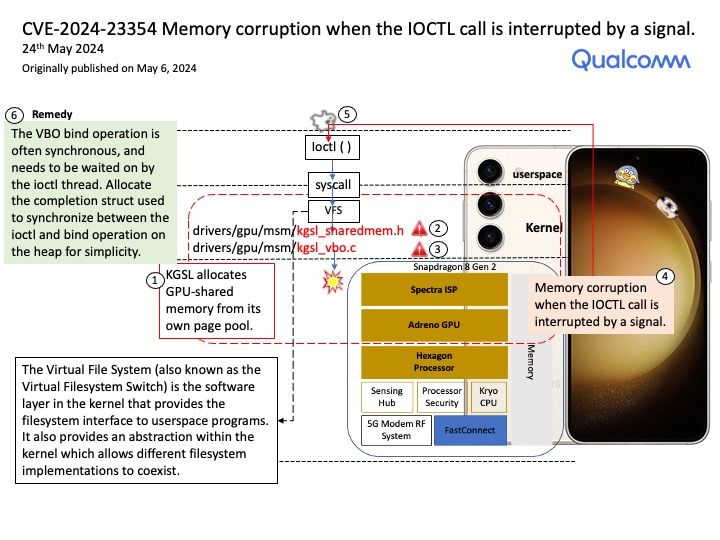
Preface: Oracle and Citrix have large customer bases and use Xen as their primary hypervisor. Red Hat, SUSE, and Canonical support KVM as a virtualization option in their Linux versions. When it comes to cloud computing, administrators face a similar decision: Citrix and Oracle offer Xen-based offerings rather than Google’s KVM.
Background: In a hypervisor command shell, such as the Citrix Hypervisor dom0 shell or the VMware ESXi host shell. You can do the following command to verify your NVIDIA virtual GPU software version.
[root@vgpu ~]# nvidia-smi
|NVIDIA-SMI 550[.]90[.]05 Driver Version: 550[.]90[.]05
NVIDIA vGPU software can be used in a variety of ways. The method we mentioned here is related to this vulnerability. In GPU pass-through mode, an entire physical GPU is directly assigned to one VM, bypassing the NVIDIA Virtual GPU Manager. In this mode of operation, the GPU is accessed exclusively by the NVIDIA driver running in the VM to which it is assigned. The GPU is not shared among VMs.
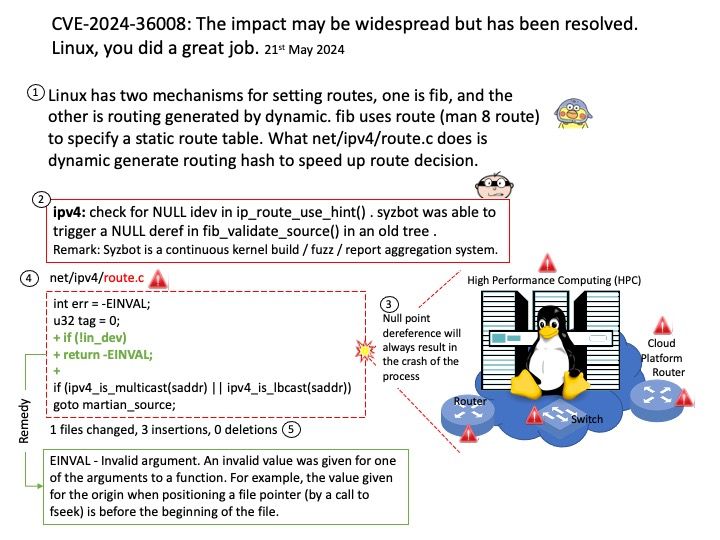
Exploiting a buffer overflow vulnerability often involves manipulating pointers to redirect program execution or inject malicious code. By overwriting the return address of a function, an attacker can divert the control flow to a different section of the program where their code is placed.
Vulnerability details:
CVE‑2024‑0099 NVIDIA vGPU software for Linux contains a vulnerability in the Virtual GPU Manager, where the guest OS could cause buffer overrun in the host. A successful exploit of this vulnerability might lead to information disclosure, data tampering, escalation of privileges, and denial of service.
CVE‑2024‑0089 NVIDIA vGPU software for Linux contains a vulnerability in the Virtual GPU Manager, where the guest OS could execute privileged operations. A successful exploit of this vulnerability might lead to information disclosure, data tampering, escalation of privileges, and denial of service.
Official announcement: For detail, please refer to link – https://nvidia.custhelp.com/app/answers/detail/a_id/5551