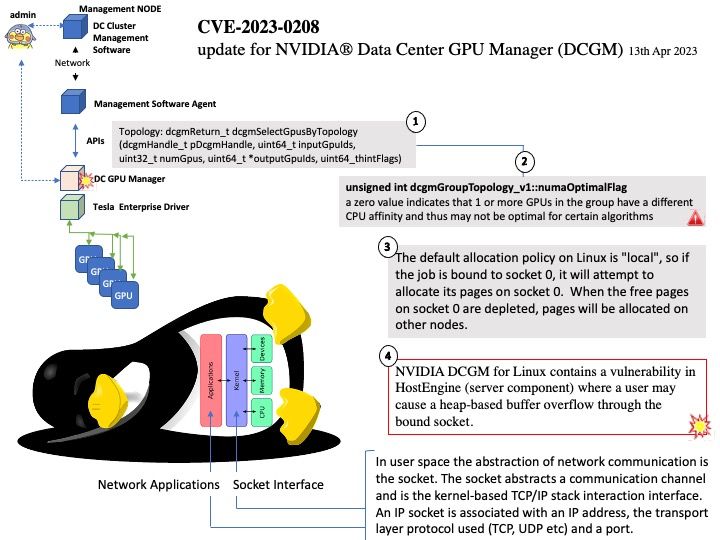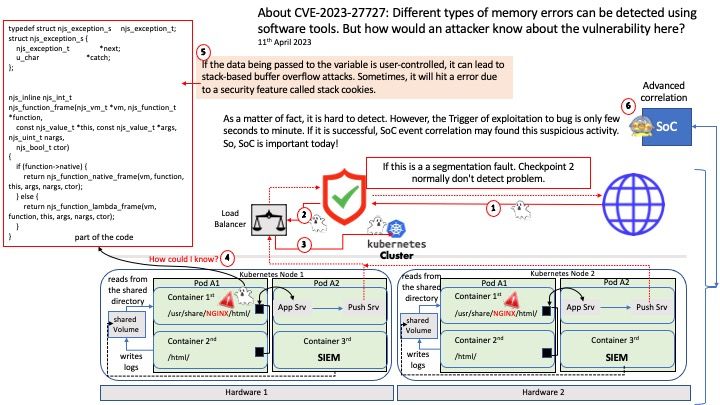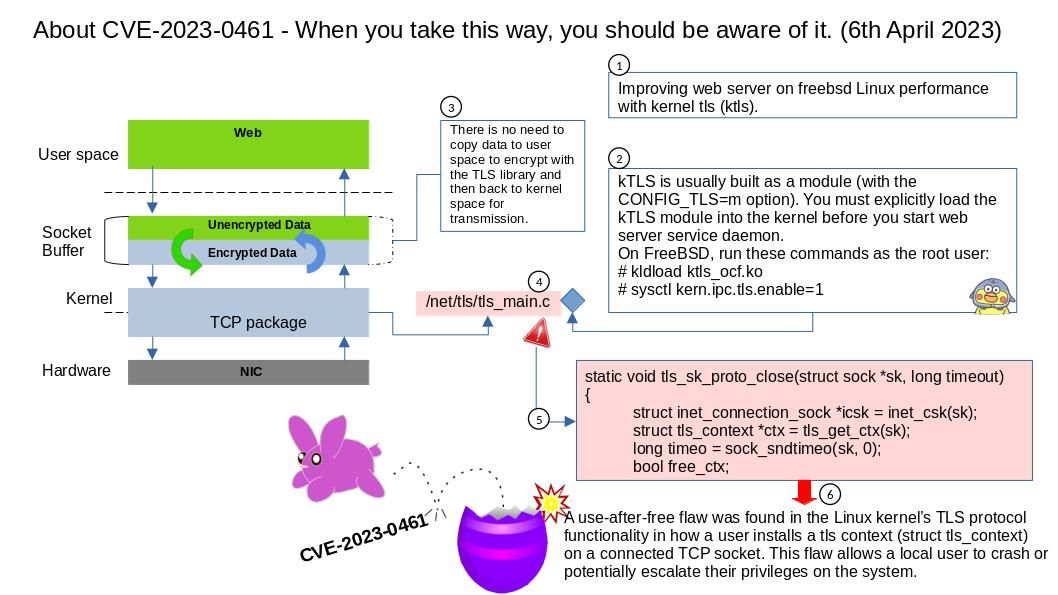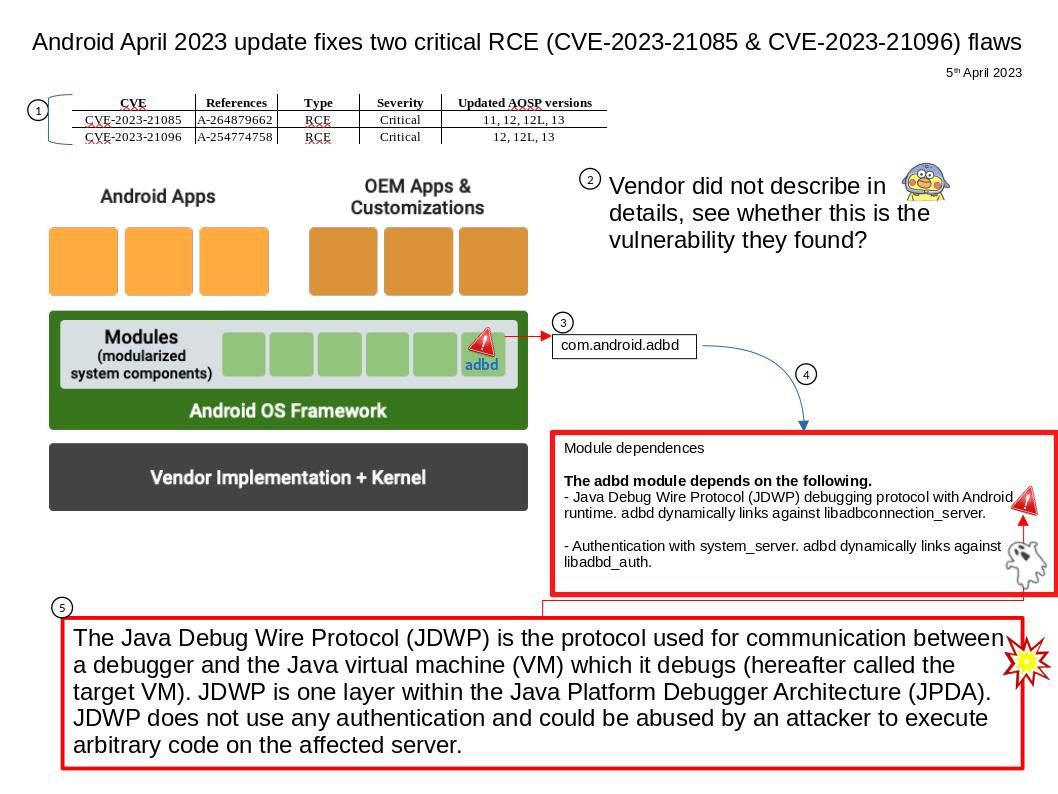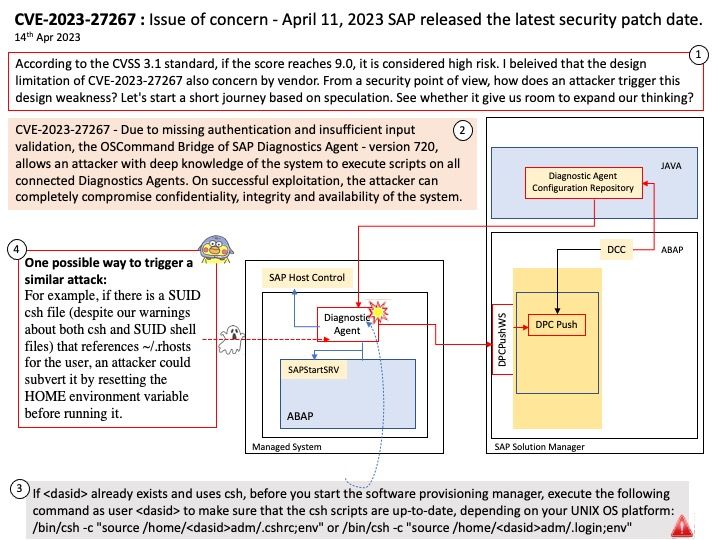
Preface: According to the CVSS 3.1 standard, if the score reaches 9.0, it is considered high risk. I beleived that the design limitation of CVE-2023-27267 also concern by vendor. From a security point of view, how does an attacker trigger this design weakness? Let’s start a short journey based on speculation. See whether it give us room to expand our thinking?
Background: SAP Solution Manager Diagnostics Agent is the remote component of End-to-End Root Cause Analysis. It allows having a connection between SAP Solution Manager and the Managed System(s), and then to collect information from the Managed Systems for reporting purposes.
Vulnerability details: A vulnerability was found in SAP Diagnostics Agent 720. It has been declared as critical. This vulnerability affects some unknown functionality of the component Command Bridge.
Due to missing authentication and insufficient input validation, the OSCommand Bridge of SAP Diagnostics Agent – version 720, allows an attacker with deep knowledge of the system to execute scripts on all connected Diagnostics Agents. On successful exploitation, the attacker can completely compromise confidentiality, integrity and availability of the system.
Official announcement: Please refer to SAP Patch Day Blog for details – https://www.sap.com/documents/2022/02/fa865ea4-167e-0010-bca6-c68f7e60039b.html