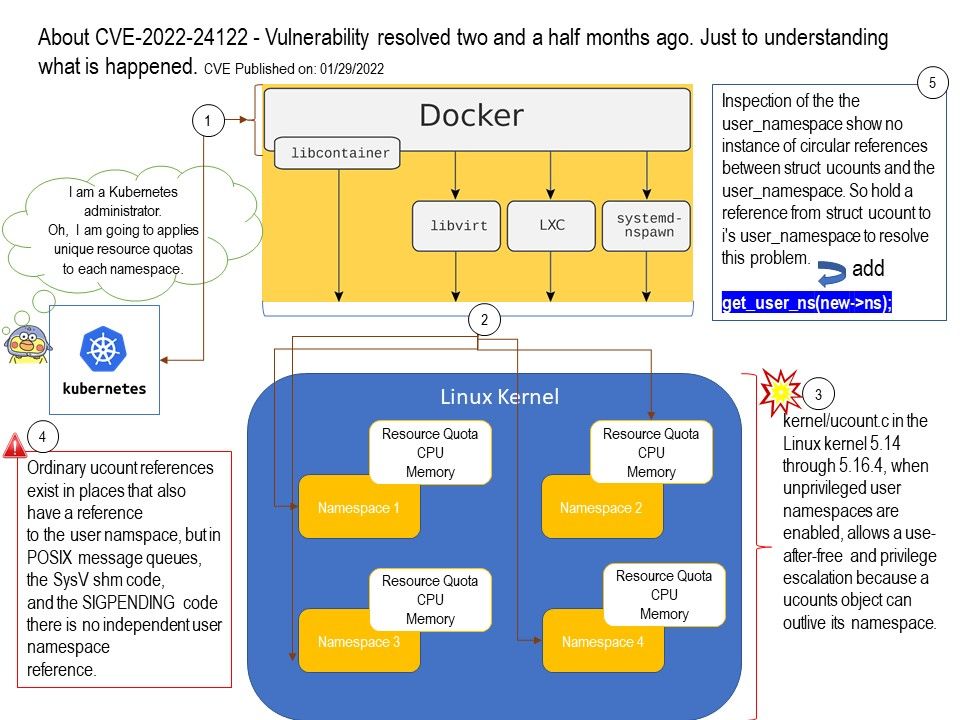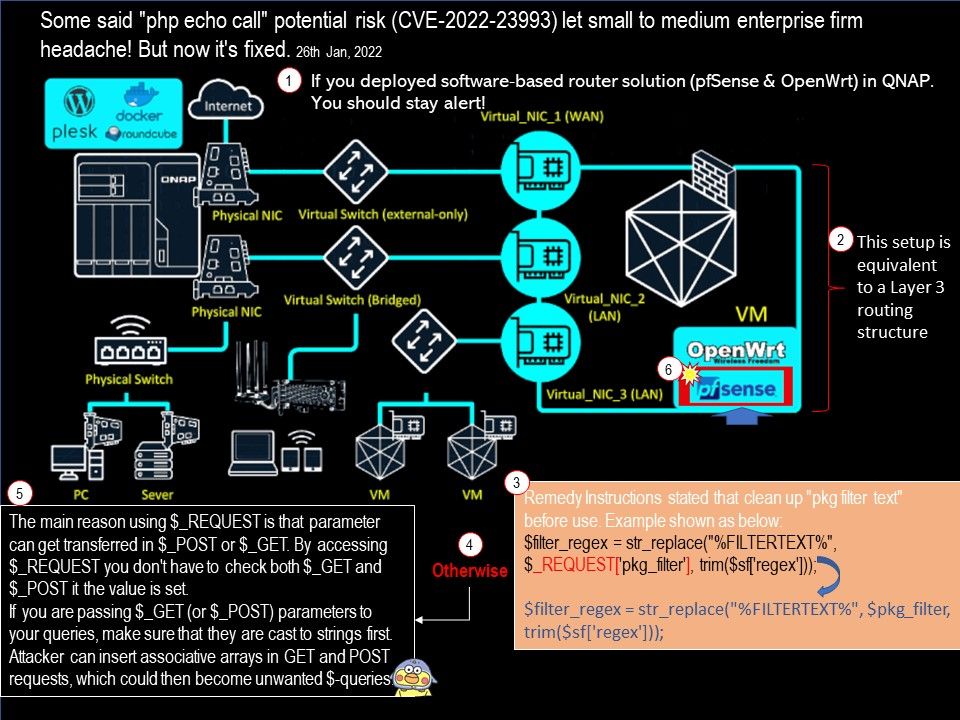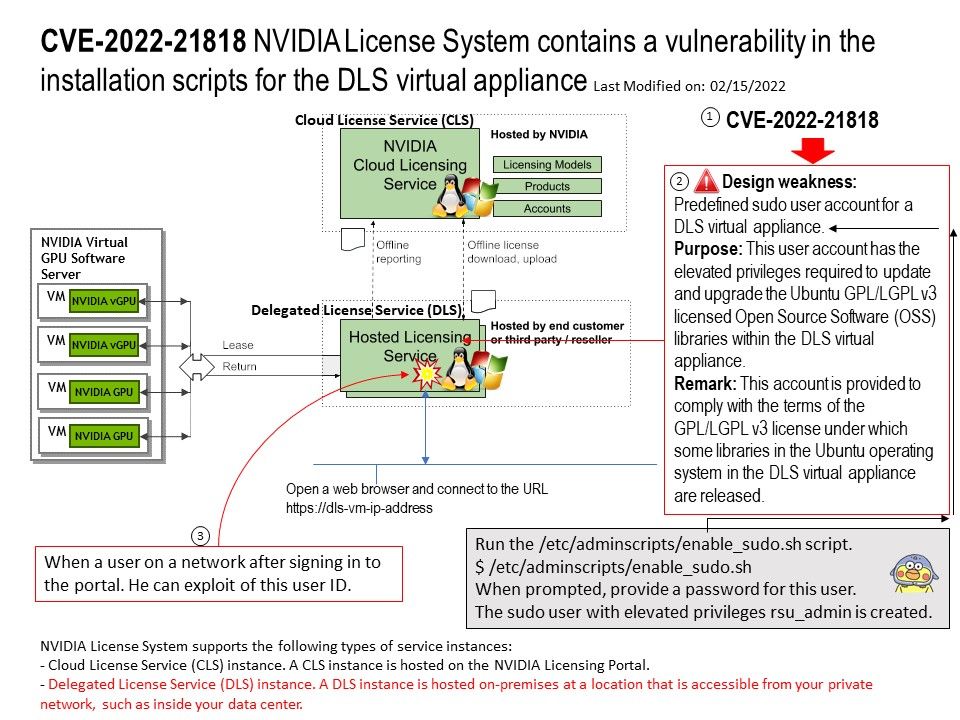
Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: NVIDIA License System supports the following types of service instances:
- Cloud License Service (CLS) instance. A CLS instance is hosted on the NVIDIA Licensing Portal.
- Delegated License Service (DLS) instance. A DLS instance is hosted on-premises at a location that is accessible from your private network, such as inside your data center.
NVIDIA License System is used to serve a pool of floating licenses to NVIDIA licensed products. The NVIDIA License System is configured with licenses obtained from the NVIDIA Licensing Portal. The license server is designed to be installed at a location that is accessible from a customer’s network, and be configured with licenses obtained from the NVIDIA Licensing Portal.
Vulnerability details: NVIDIA License System contains a vulnerability in the installation scripts for the DLS virtual appliance, where a user on a network after signing in to the portal can access other users’ credentials, allowing them to gain escalated privileges.
One of the possibilities: Traditional technology make use of service account concept.
Design weakness: Predefined sudo user account for a DLS virtual appliance.
Purpose: This user account has the elevated privileges required to update and upgrade the Ubuntu GPL/LGPL v3 licensed Open Source Software (OSS) libraries within the DLS virtual appliance.
Remark: This account is provided to comply with the terms of the GPL/LGPL v3 license under which some libraries in the Ubuntu operating system in the DLS virtual appliance are released.
Official announcement: Please refer to the link for details – https://nvidia.custhelp.com/app/answers/detail/a_id/5319
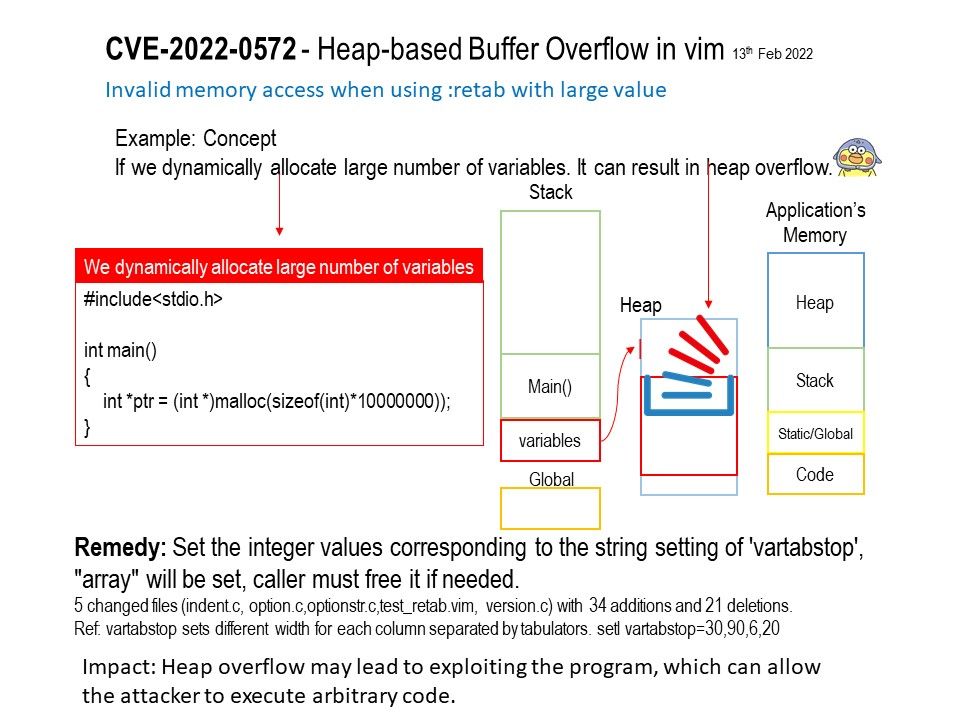
.jpg?width=1920&height=1080&fit=bounds)

.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)