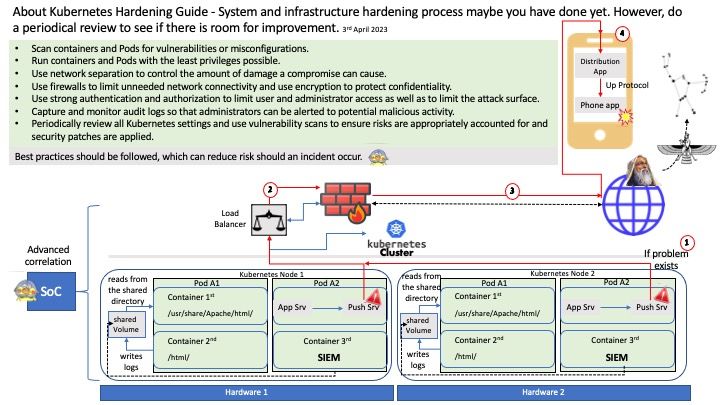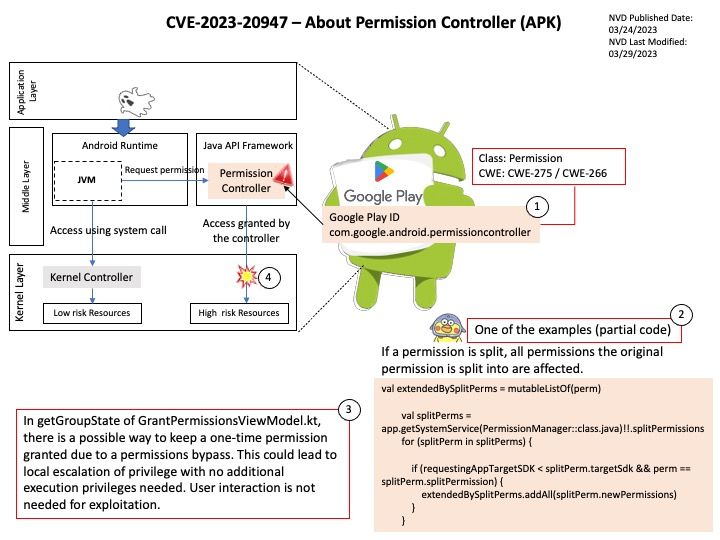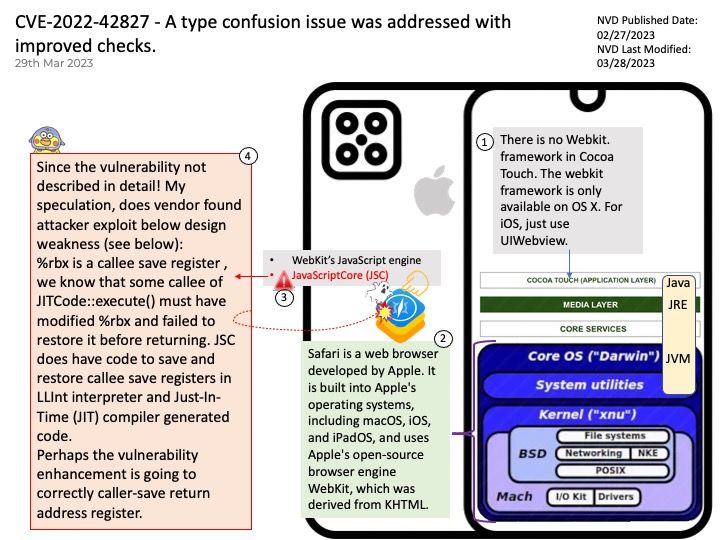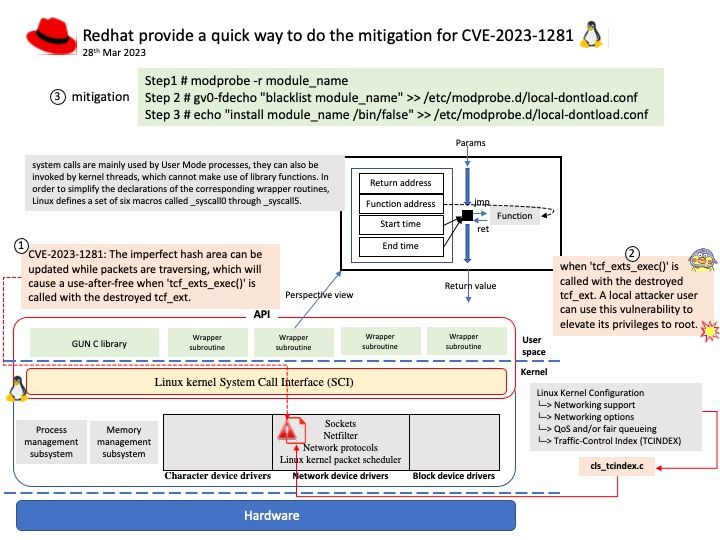
Preface: The easter hoilday in 2nd week of April. So this news may have late. On 03/31/2023 03:00 PM, NVIDIA has released a software update for NVIDIA® Data Center GPU Manager (DCGM). The update addresses security issues that may lead to denial of service and data tampering.
Be my guest, see wether you will be interested?
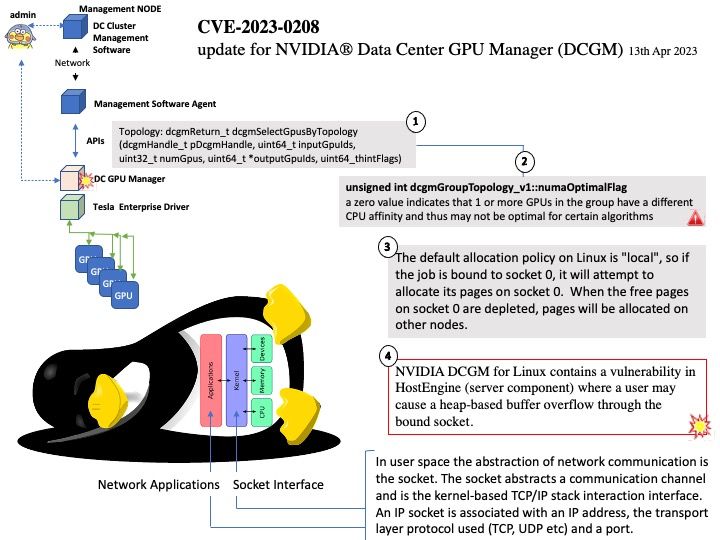
Background: NVIDIA Data Center GPU Manager (DCGM) is a suite of tools for managing and monitoring NVIDIA datacenter GPUs in cluster environments. It includes active health monitoring, comprehensive diagnostics, system alerts and governance policies including power and clock management.
DCGM provides several mechanisms for understanding GPU topology both at a verbose device-level view and non-verbose group-level view. These views are designed to give a user information about connectivity to other GPUs in the system as well as NUMA/ affinity information.
Ref: Non-uniform memory access is a computer memory design used in multiprocessing, where the memory access time depends on the memory location relative to the processor. Under NUMA, a processor can access its own local memory faster than non-local memory.
Vulnerability details: NVIDIA DCGM for Linux contains a vulnerability in HostEngine (server component) where a user may cause a heap-based buffer overflow through the bound socket. A successful exploit of this vulnerability may lead to denial of service and data tampering.
Official announcement: For details, please refer to the official announcement – https://nvidia.custhelp.com/app/answers/detail/a_id/5453