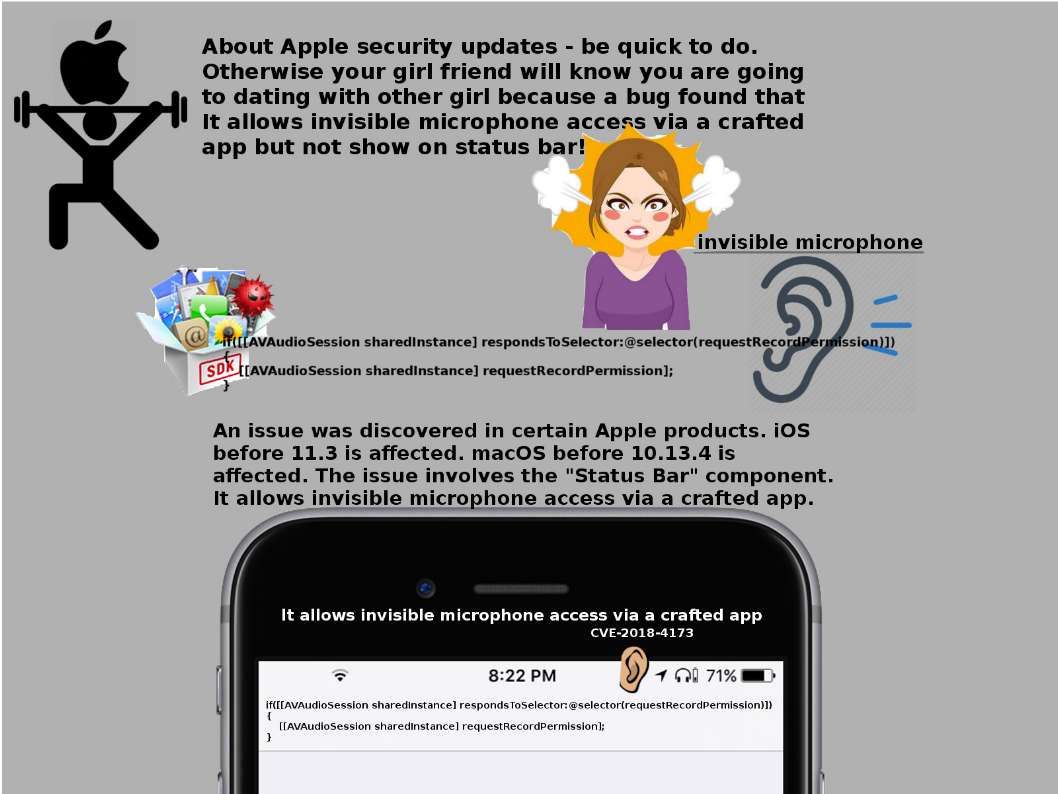
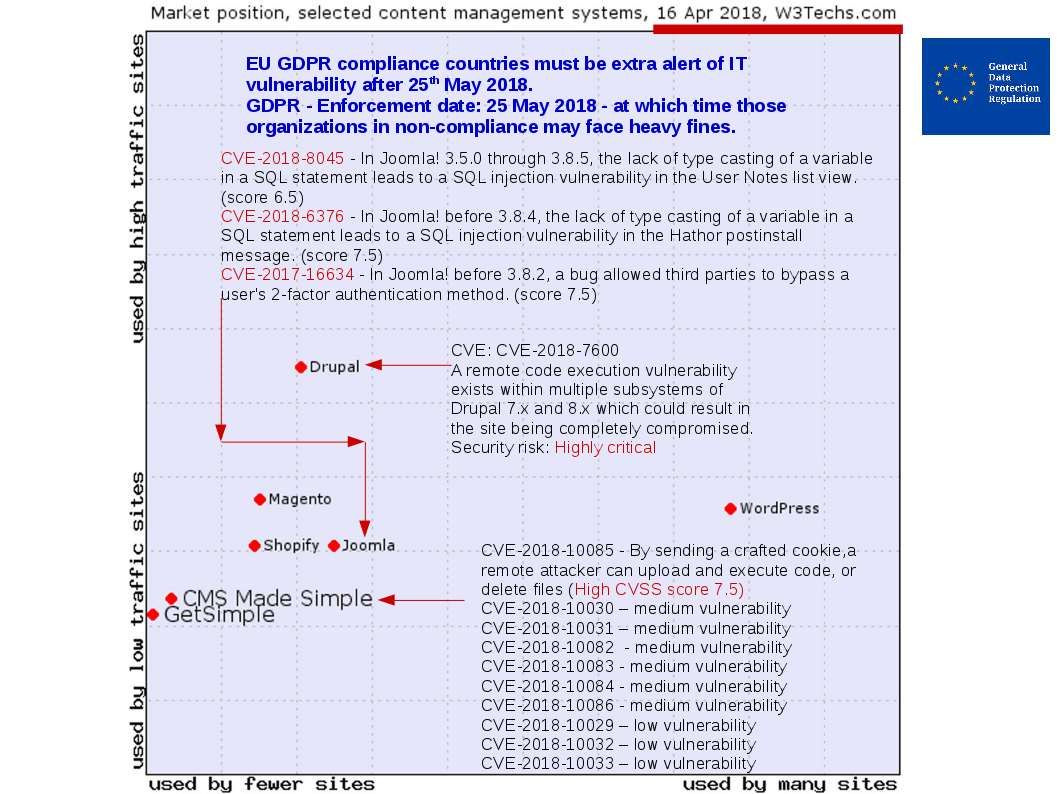
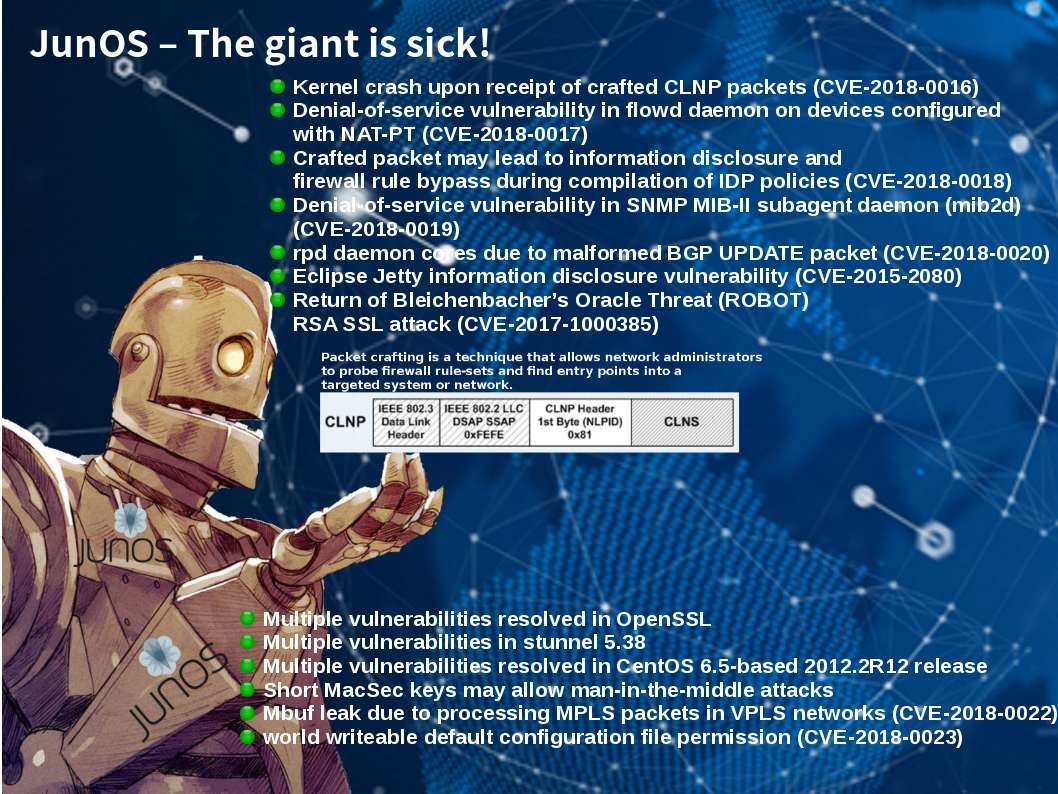
Be extra alert because alliance bombarded Syria chemical facilities with justice. So the cyber attacks will be increased. I encourages users and administrators to review the following Cisco Security Advisories and apply the necessary updates. For more details, please see below:
Cisco WebEx Clients Remote Code Execution Vulnerability cisco-sa-20180418-wbs (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-wbs
Cisco UCS Director Virtual Machine Information Disclosure Vulnerability for End User Portal cisco-sa-20180418-uscd (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-uscd
Cisco StarOS Interface Forwarding Denial of Service Vulnerability cisco-sa-20180418-staros (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-staros
Cisco IOS XR Software UDP Broadcast Forwarding Denial of Service Vulnerability cisco-sa-20180418-iosxr (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-iosxr
Cisco Firepower Detection Engine Secure Sockets Layer Denial of Service Vulnerability cisco-sa-20180418-fpsnort (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-fpsnort
Cisco Firepower 2100 Series Security Appliances IP Fragmentation Denial of Service Vulnerability cisco-sa-20180418-fp2100 (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-fp2100
Cisco ASA Software, FTD Software, and AnyConnect Secure Mobility Client SAML Authentication Session Fixation Vulnerability cisco-sa-20180418-asaanyconnect (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-asaanyconnect
Cisco Adaptive Security Appliance Application Layer Protocol Inspection Denial of Service Vulnerabilities cisco-sa-20180418-asa_inspect (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-asa_inspect
Cisco Adaptive Security Appliance TLS Denial of Service Vulnerability cisco-sa-20180418-asa3 (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-asa3
Cisco Adaptive Security Appliance Flow Creation Denial of Service Vulnerability cisco-sa-20180418-asa2 (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-asa2
Cisco Adaptive Security Appliance Virtual Private Network SSL Client Certificate Bypass Vulnerability cisco-sa-20180418-asa1 (link is external) – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-asa1