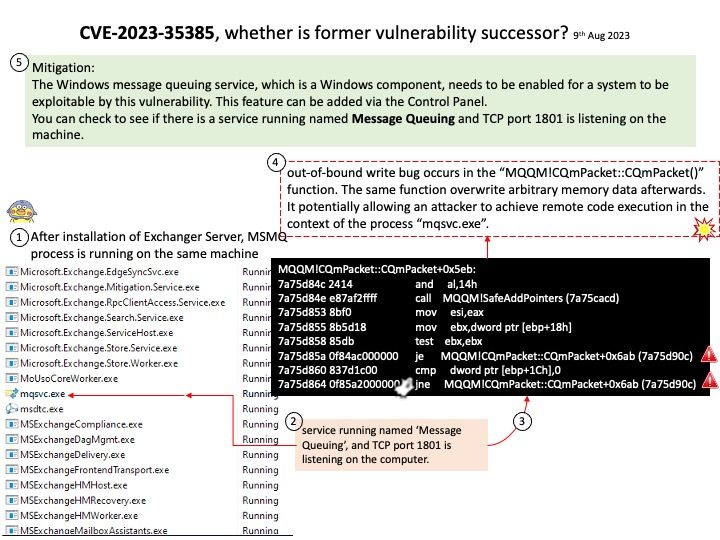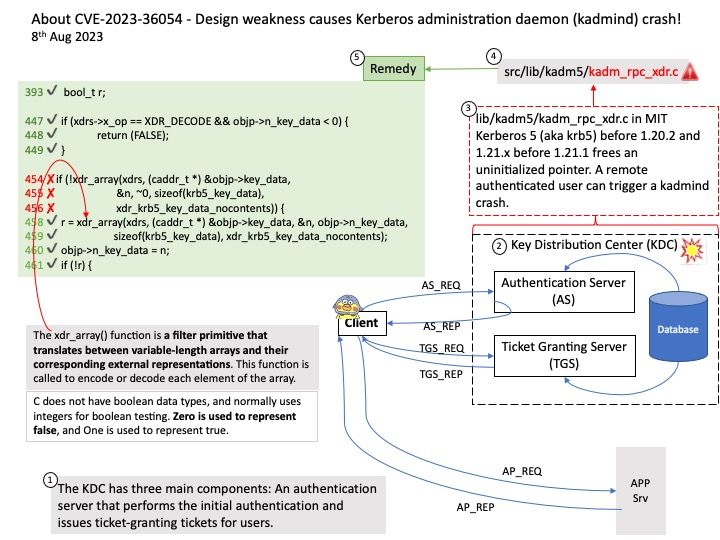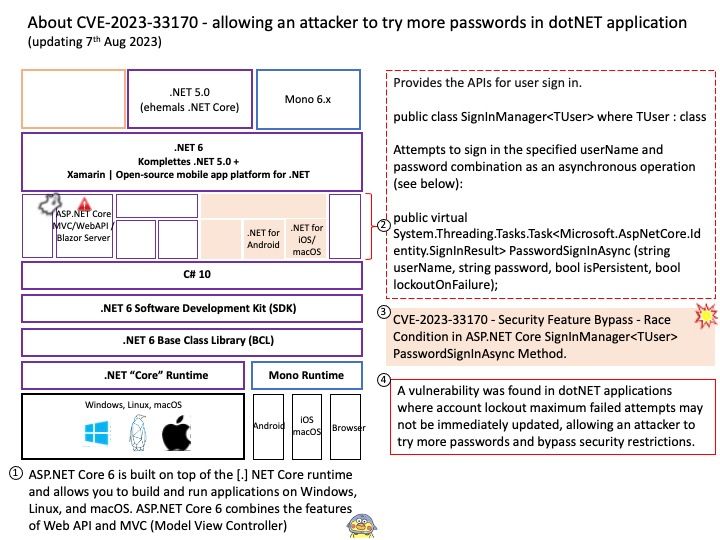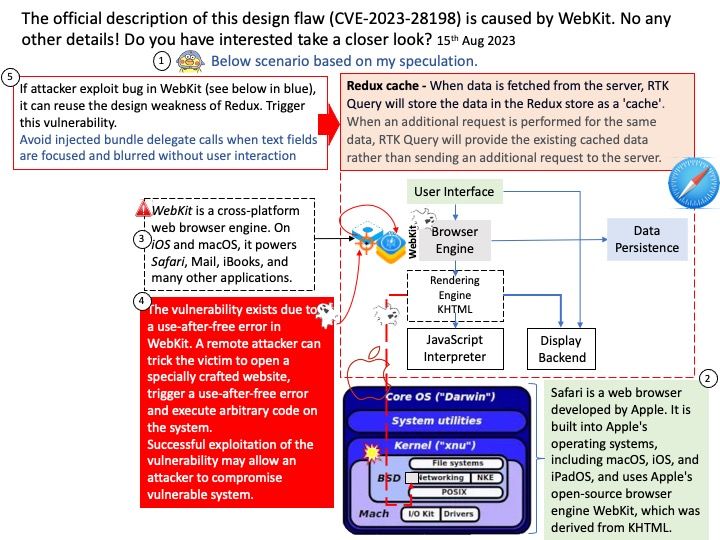
Preface: The official description of this design flaw (CVE-2023-28198) is caused by WebKit. No any other details! Do you have interested take a closer look? But don’t worry, this CVE marked reserved in March 2023. and allow for announcements on August 15, 2023 afterwards. I believe Apple has successfully handled it.
Background: WebKit, the engine, is split into different components that encapsulate its different parts.
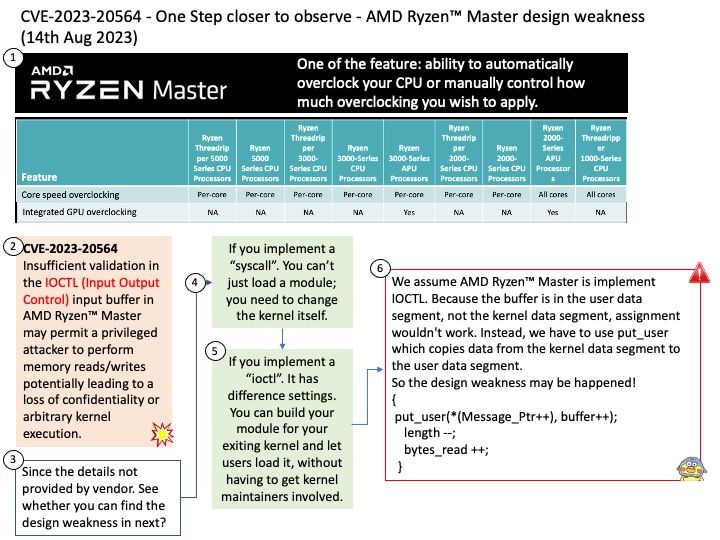
It contains the core features of the engine (rendering, layout, platform access, HTML and DOM support, the graphics layer, etc). However, some of these ultimately depend heavily on the OS and underlying software platform in order to function. For example: how do we actually do any I/O on different platforms? How do we render onscreen? What’s the underlying multimedia platform and how does it decode media and play it?
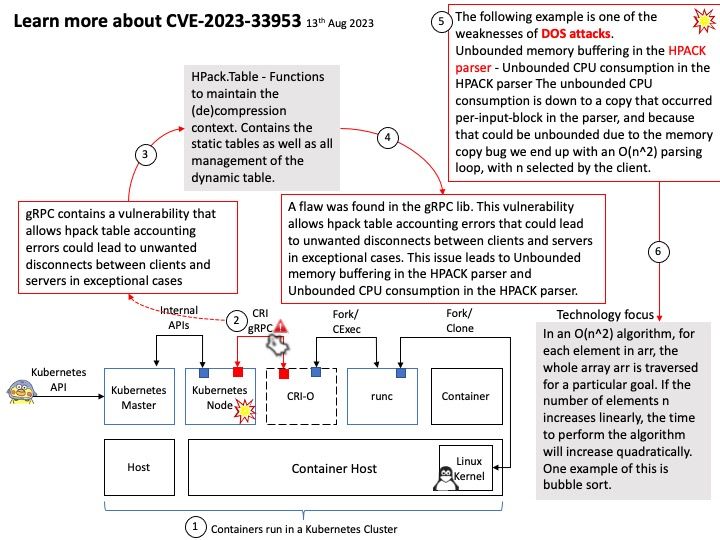
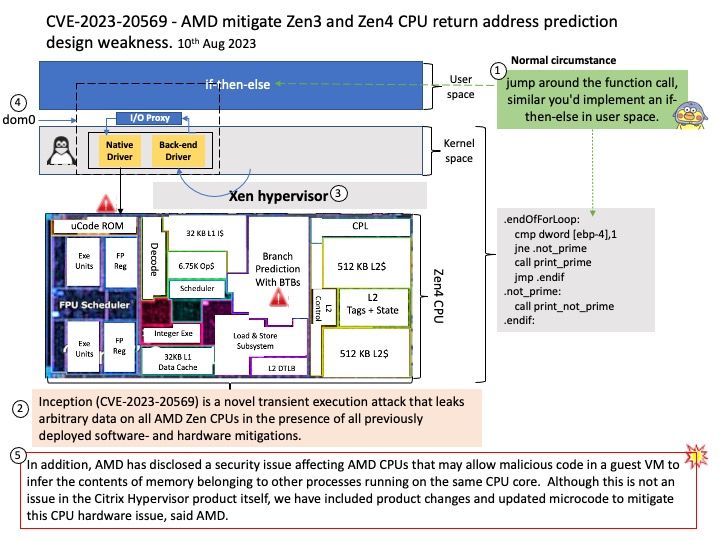
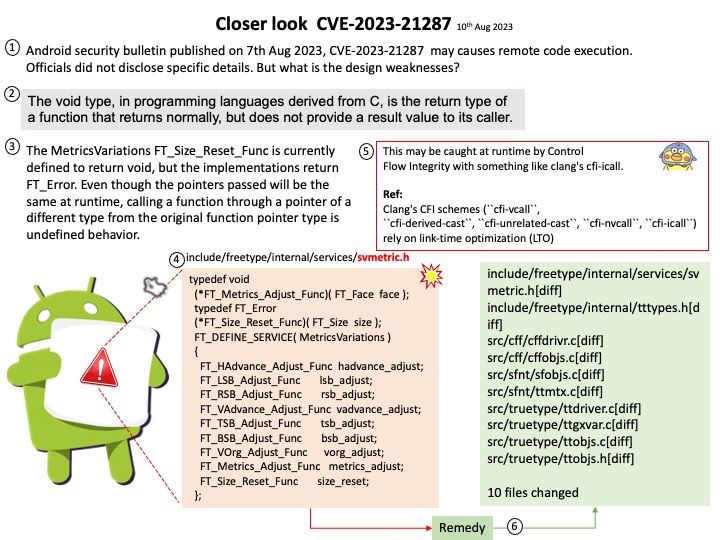
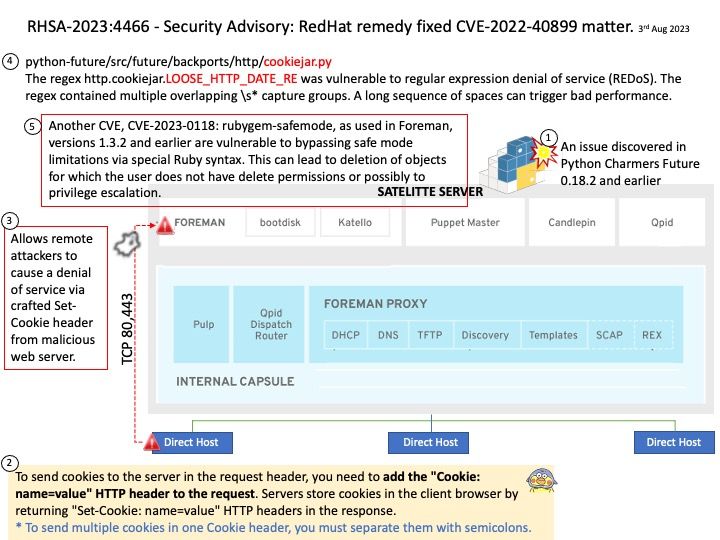
Vulnerability details: The vulnerability allows a remote attacker to compromise vulnerable system. The vulnerability exists due to a use-after-free error in WebKit. A remote attacker can trick the victim to open a specially crafted website, trigger a use-after-free error and execute arbitrary code on the system. Successful exploitation of the vulnerability may allow an attacker to compromise vulnerable system.
Available for: macOS Ventura
Impact: Processing web content may lead to arbitrary code execution
Official announcement: For details, please refer to the link – https://support.apple.com/en-us/HT213670