Preface: Programmer just spend 10 minutes write a python script then can listen UDP traffic. Even though we performing Google Search , the function is using Python code.
Information background:
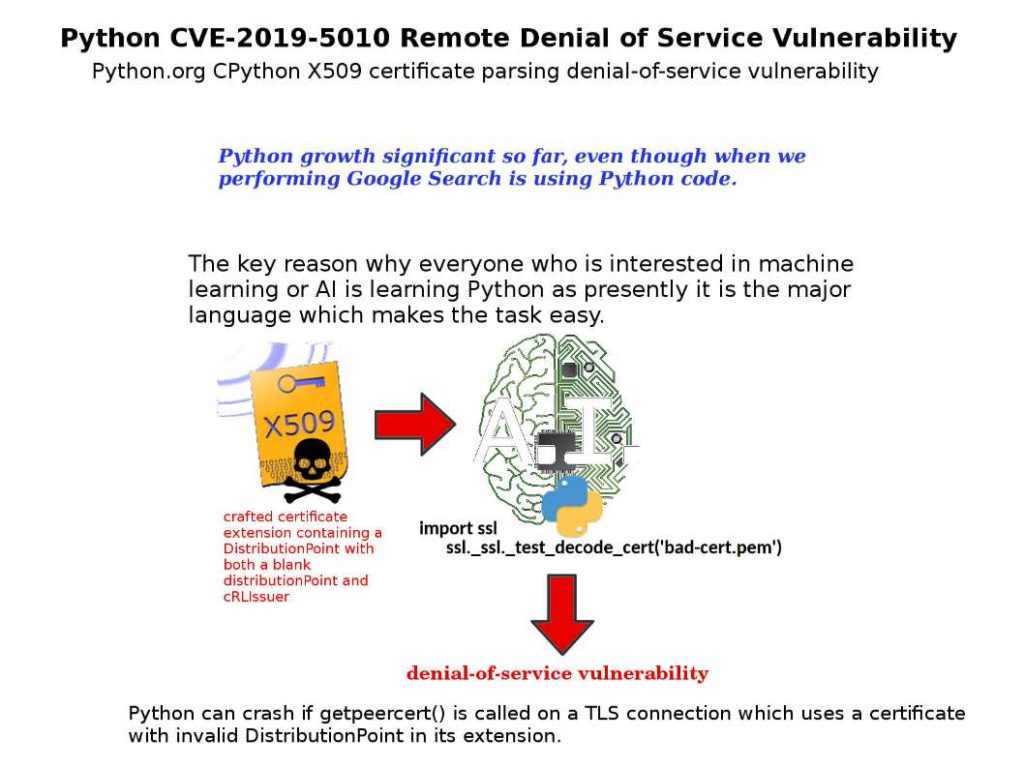
Python has now become the most taught programming languages in Universities and Academica. Machine learning or artificial intelligence is learning Python because it is the primary language that makes tasks easier.
Vulnerability:
The security expert from Cisco Talos found that a vulnerability will be occured when python parser handling x509 certificate. A handshake failures result in skipping the call to getpeercert(). Under above circumstances, attacker can craft a x.509 certificate with both a blank distributionPoint and cRLIssuer causes a NULL pointer dereference. As a result a denial-of-service occur.
Official details: https://bugs.python.org/issue35746