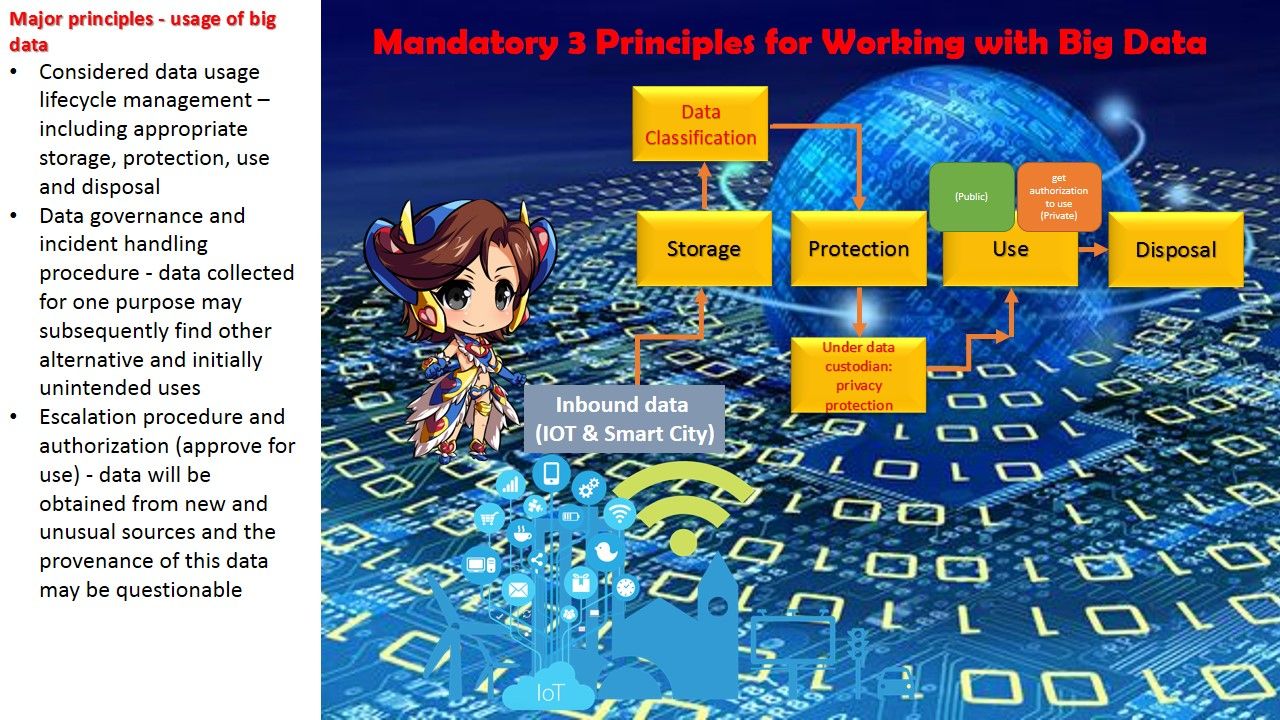
We frequently heard smartcity project and usage of big data. Such key terms for the 1st impression to people is that it is a advanced technique and techology trend in future. In fact it was not possible to say we are keen to enjoy the benefits of smart city and big data analytic but we just ignore the peripherals. How does a city approiate to do such setup on start from strach situation. For example HKSAR issued the smart City blue print mid of last year. But it got whole bunch of unkown answer waiting for queries(public or quires with industries)? Perhaps the objectives of smart city goal to ehance public safty and governance of the city. The career oppuntunities is the side products which carry by this project. If the key items of city not been resolve yet. For instance: population, immigation policy and land use. Even though you enforce this project it may far away from their original design objectives.
Below url is the smart city blueprint for HKSAR for your reference.