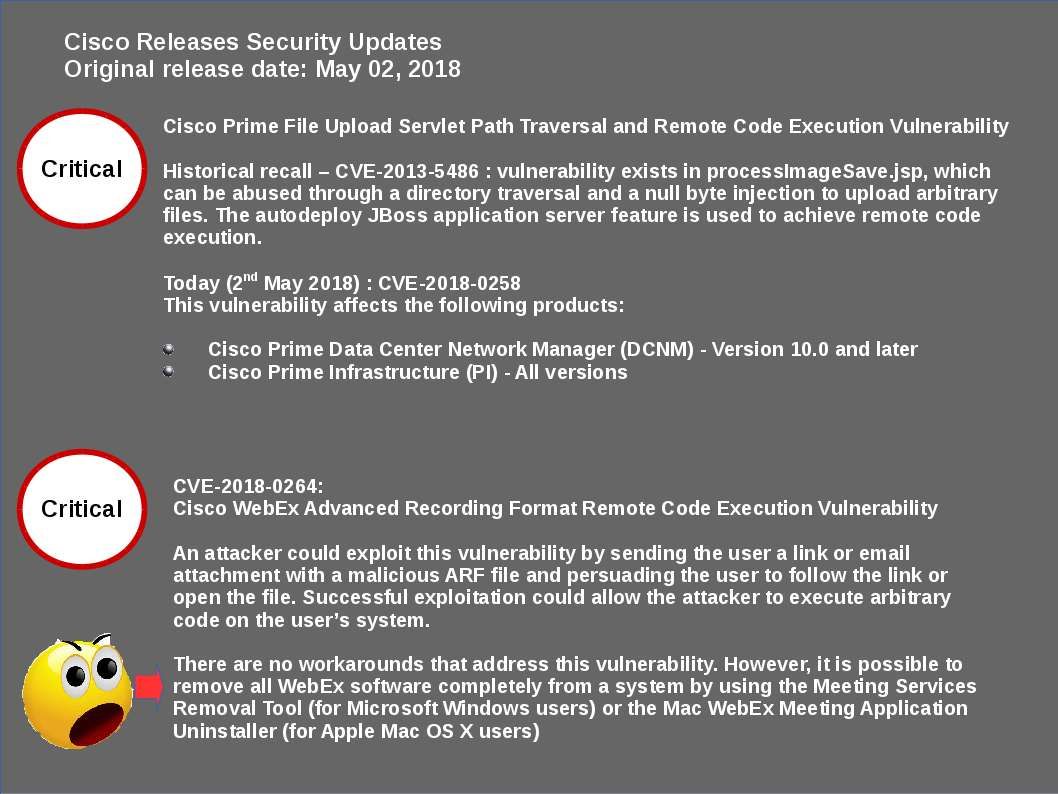
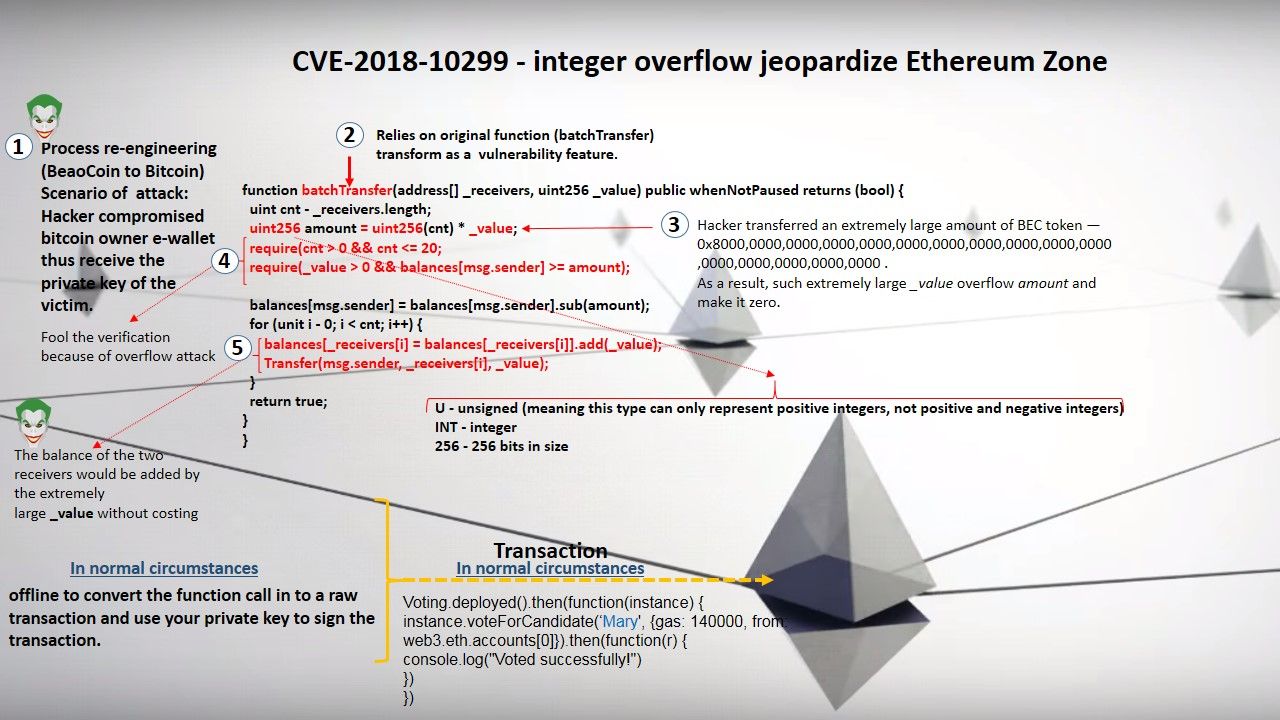
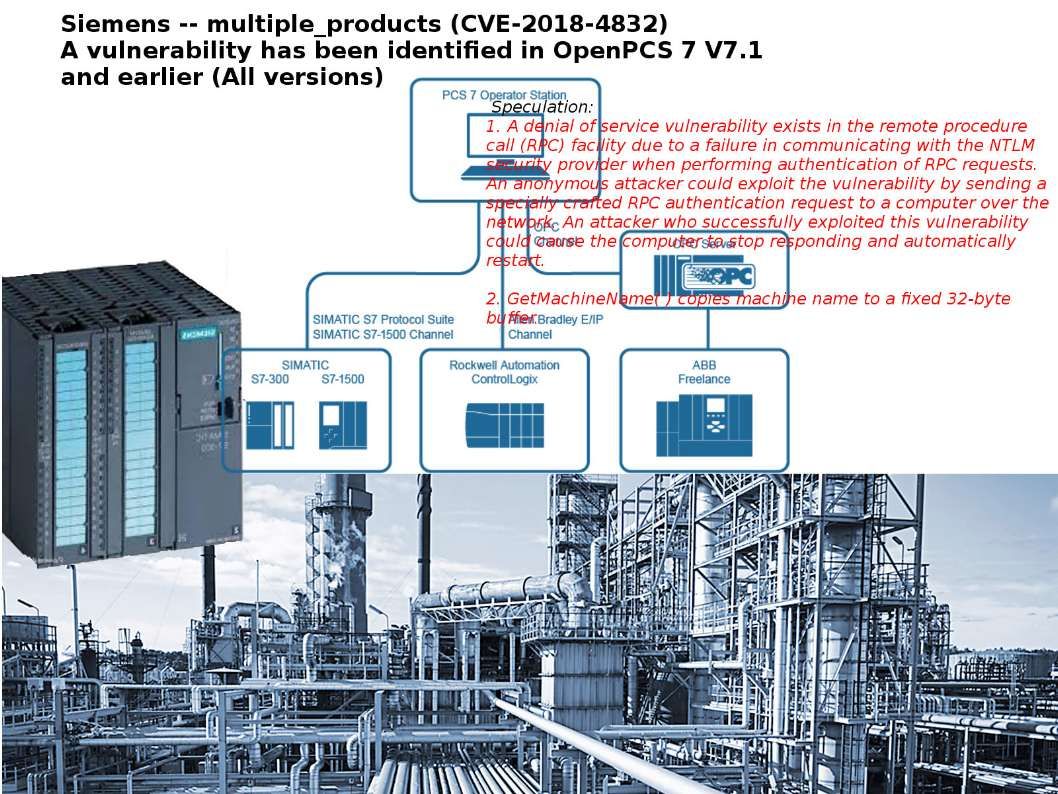
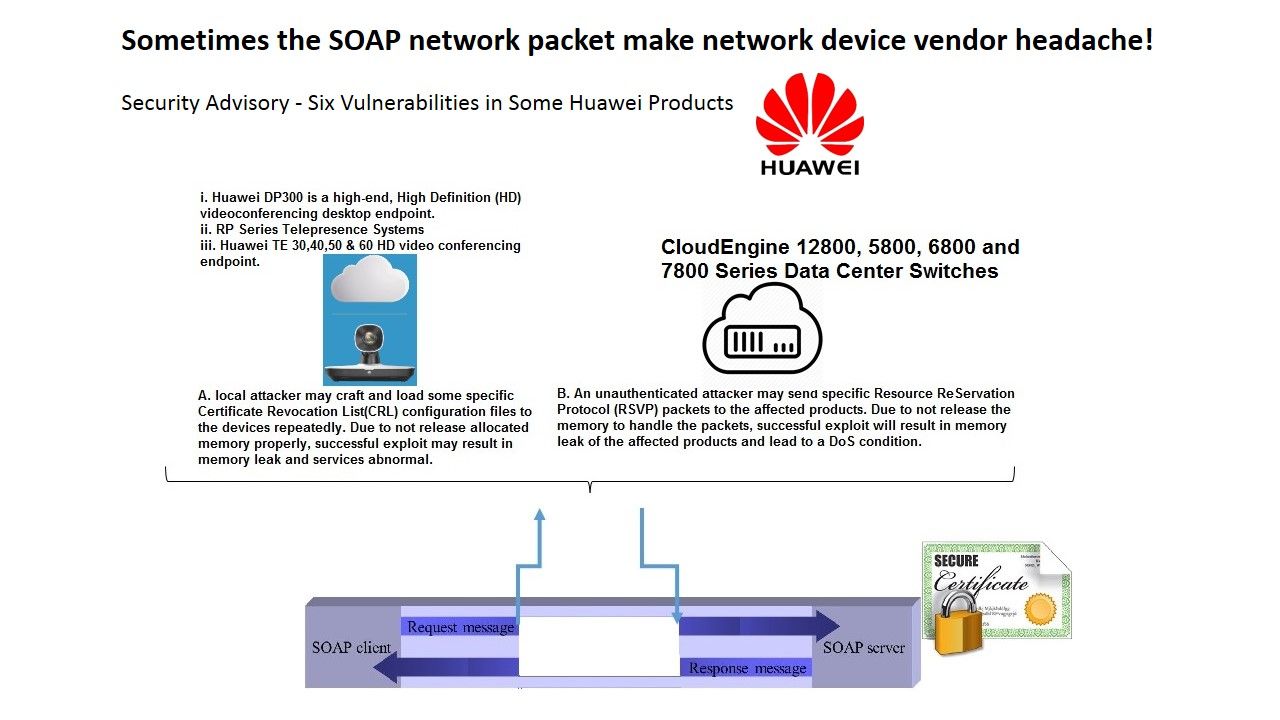
A low level container management API in Hyper-V called the Host Compute Service (HCS). HCS compatible written in Go (and used by Docker), and the other is written in C#.
On 2nd of May, Microsoft official announcement urge end user who deployed Host Computer Service (HCS) requires to do the security update. Microsoft has patched their own infrastructure hosting offerings, as have Microsoft partners with Google among them.
Technical details:
(CVE-2018-8115) – Duplicate the original CVE technical details.
A remote code execution vulnerability exists when the Windows Host Compute Service Shim (hcsshim) library fails to properly validate input while importing a container image. To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host.
For remediation of design limitation, new version of hcsshim v0.6.10 enhance sanitize function. So called sanitize function did not use below command.
Example:
p := xxxxx.UGCPolicy()
user.Name, user.Address = p.Sanitize(user.Name),p.Sanitize(user.Address)But do you have any idea in regards to below command syntax?
}
func makeError(err error, title, rest string) error {
// Pass through DLL errors directly since they do not originate from HCS.
if _, ok := err.(*syscall.DLLError); ok {
return err
}
return &HcsError{title, rest, err}
}
The new release of the hcsschim able to addresses security fixes.For more details, please refer below url for reference.
Change to address CVE-2018-8115