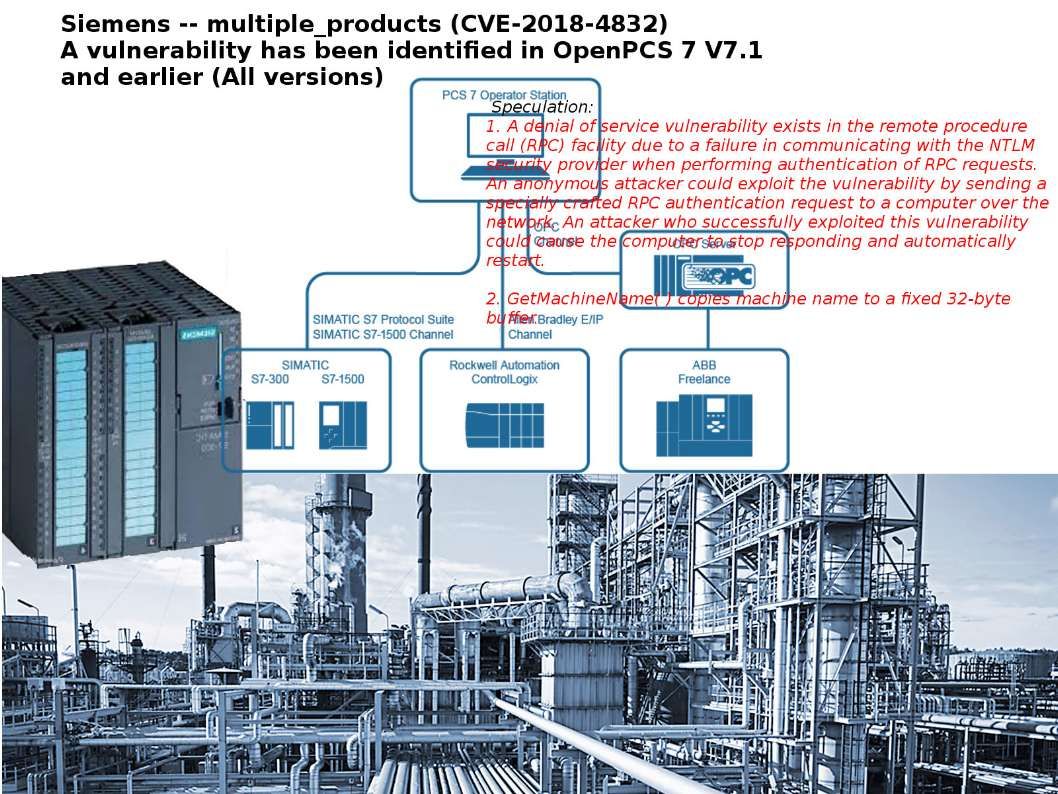
The Gas and Petroleum industries requires automation to enhance their overall operation in last decade. And therefore the automation system setup requires Supervisory control and data acquisition (SCADA). We noticed that hackers targeted SCADA system installed in nuclear power facilities. We are living in digital age and therefore electricity power supply similar air and water. So system automation hardware vendor has responsibility to hardening their system design. Siemens found vulnerability in their Automation Technology Process control systems (PCS 7) on April last month. For more details, please refer below url for reference.
Vulnerability details
https://cert-portal.siemens.com/productcert/pdf/ssa-348629.pdf
My Speculation:
1. A denial of service vulnerability exists in the remote procedure call (RPC) facility due to a failure in communicating with the NTLM security provider when performing authentication of RPC requests. An anonymous attacker could exploit the vulnerability by sending a specially crafted RPC authentication request to a computer over the network. An attacker who successfully exploited this vulnerability could cause the computer to stop responding and automatically restart.
2. GetMachineName ( ) copies machine name to a fixed 32 byte buffer causes problem occurs.