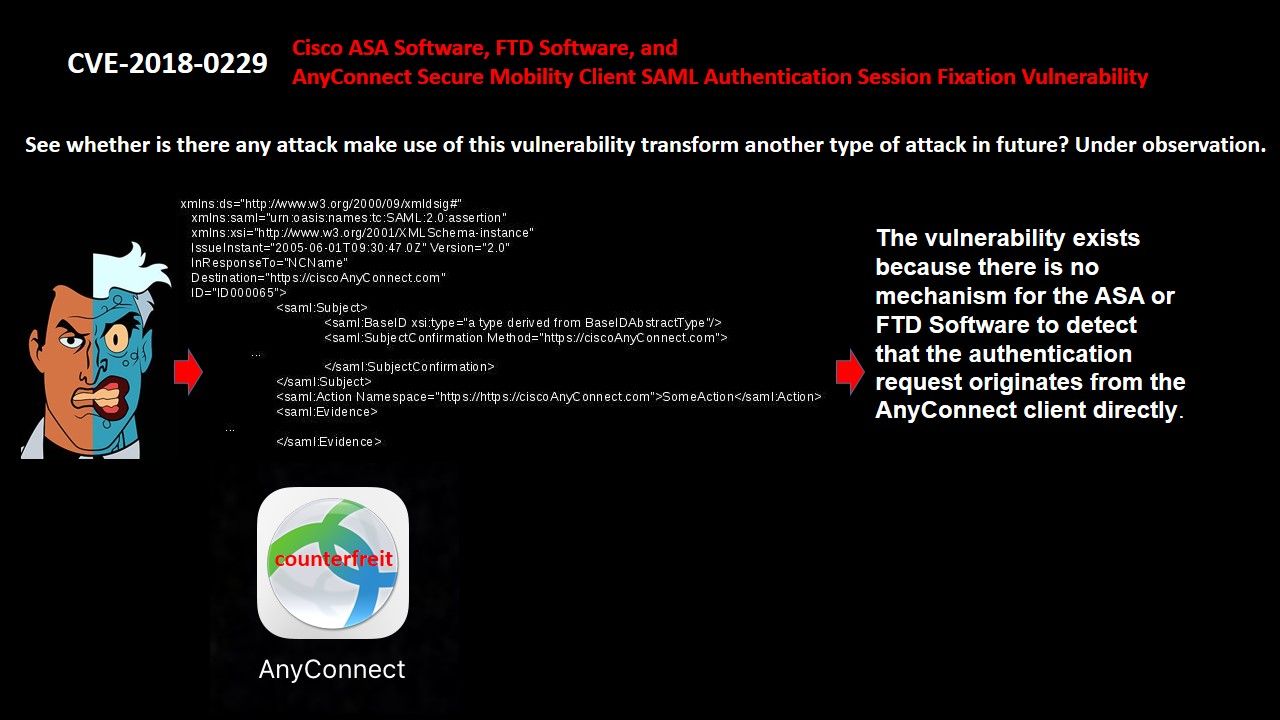
Seems firewall administrator do not take the single sign-on authentication method in firewall. Perhaps it can’t fulfill audit requirement. Cisco found SAML Authentication Session Fixation Vulnerability. The vulnerability exists because there is no mechanism for the ASA or FTD Software to detect that the authentication request originates from the AnyConnect client directly. An attacker could exploit this vulnerability by persuading a user to click a crafted link and authenticating using the company’s Identity Provider (IdP). My concerns is that see whether is there any attack make use of this vulnerability transform another type of attack in future?
Cisco Official announcement is shown as below: