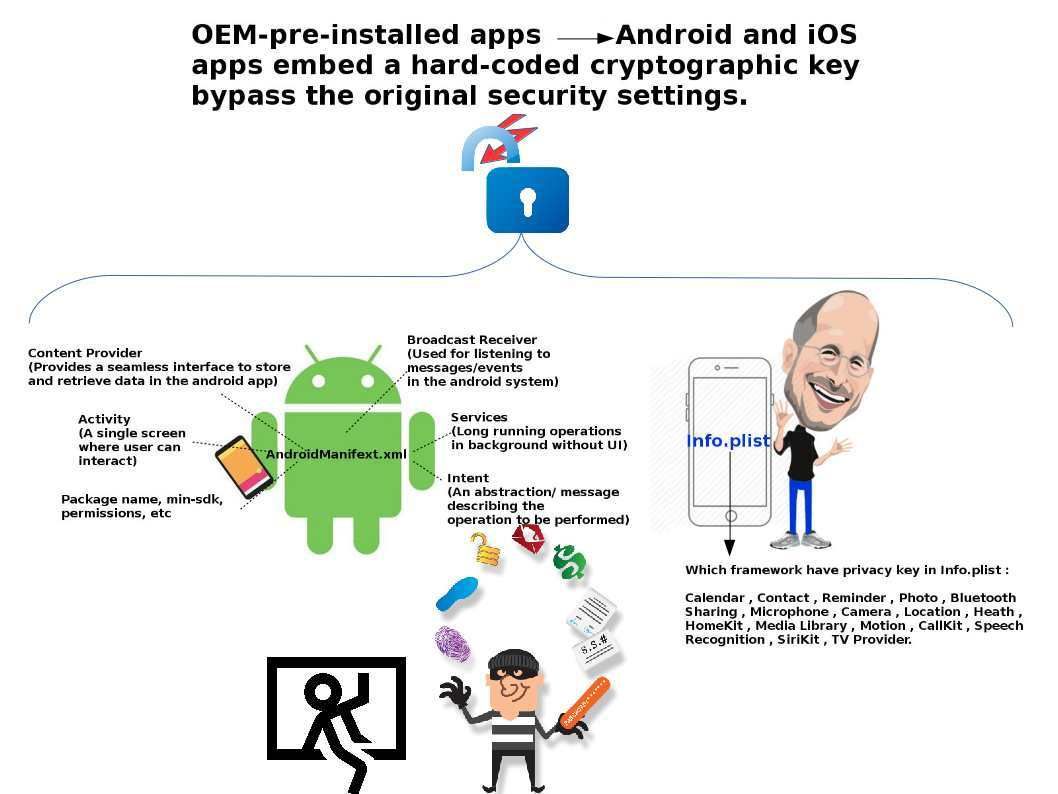
Android and iOS apps contain multiple vulnerabilities:
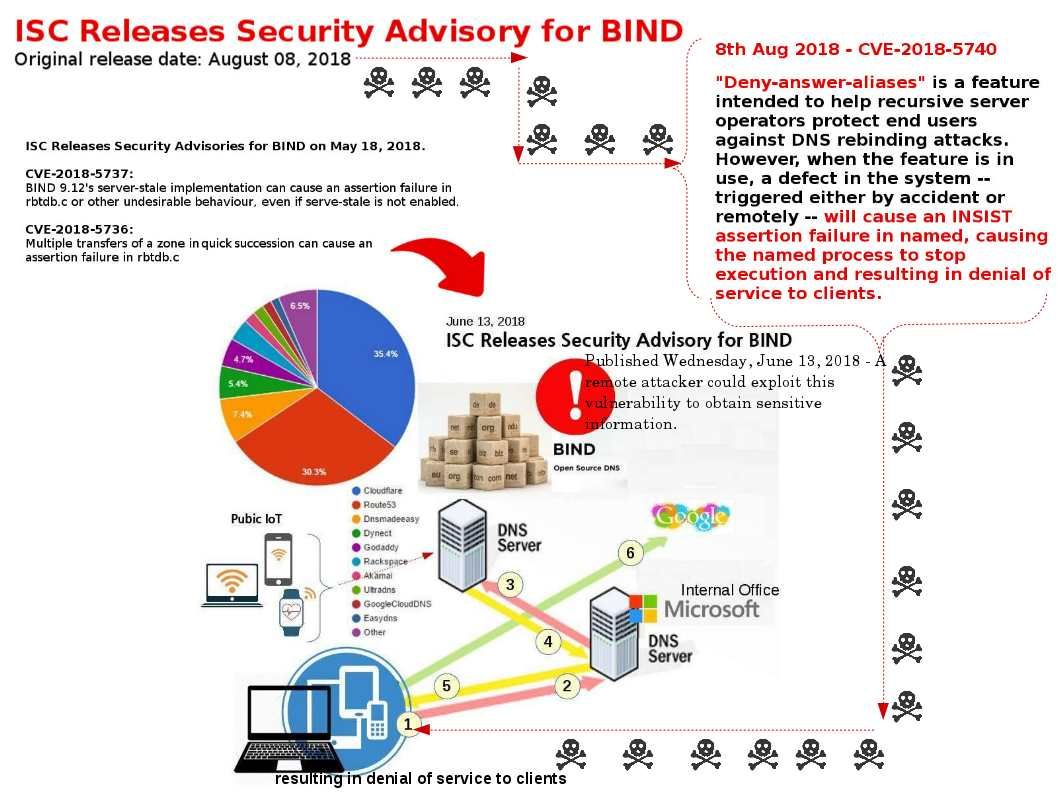
Original Release date: 14 Aug 2018 | Last revised: 15 Aug 2018
Google apps store and App Store (iphone) enforce security policies last year get rid the suspected malicious apps in their store. From customer point of view, it looks better because this is the soure download location. It will avoid the malware infection. A efficency way to avoid cyber security accident and data breach in mobile devices world. However there is another way to evade your phone security setting. What is the way? The OEM vendor pre installed apps like a backdoor. Let’s the Android and iOS apps embed a hard-coded cryptographic key bypass the original security settings.
US-CERT security alert – please refer below url: