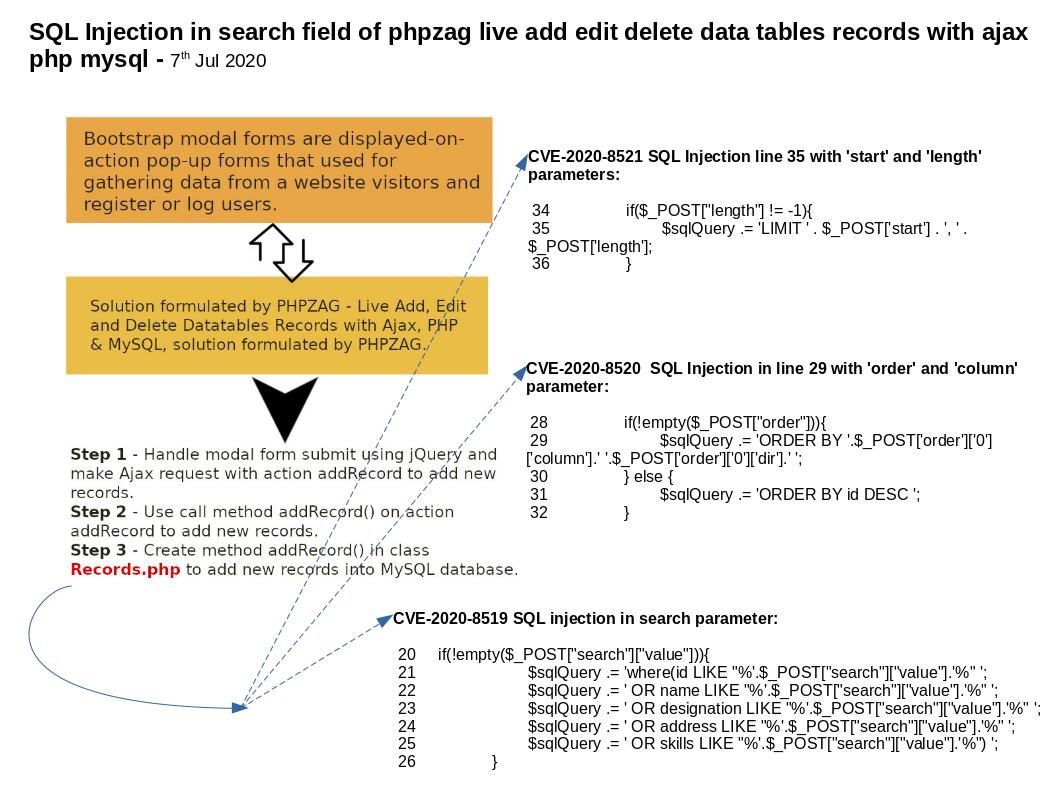
Preface: Bootstrap modal forms are displayed-on-action pop-up forms that are used for gathering data from website visitors and to register or log users.
Background: PHPZAG[.]COM is a programming blog that publishes practical and useful tutorials for programmers and web developers.
Solution formulated by PHPZAG – Live Add, Edit and Delete Datatables Records with Ajax, PHP & MySQL, solution formulated by PHPZAG.
Step 1 – Handle modal form submit using jQuery and make Ajax request with action addRecord to add new records.
Step 2 – Use call method addRecord() on action addRecord to add new records.
Step 3 – Create method addRecord() in class Records.php to add new records into MySQL database.
The vulnerability found on 19th May 2020, but NVD published on 7th July , 2020 finally. The source file can be download in the following url – https://www.phpzag.com/live-add-edit-delete-datatables-records-with-ajax-php-mysql/
Vulnerability details:
CVE-2020-8519 SQL injection in search parameter
CVE-2020-8520 SQL Injection in line 29 with ‘order’ and ‘column’ parameter
CVE-2020-8521 SQL Injection line 35 with ‘start’ and ‘length’ parameters
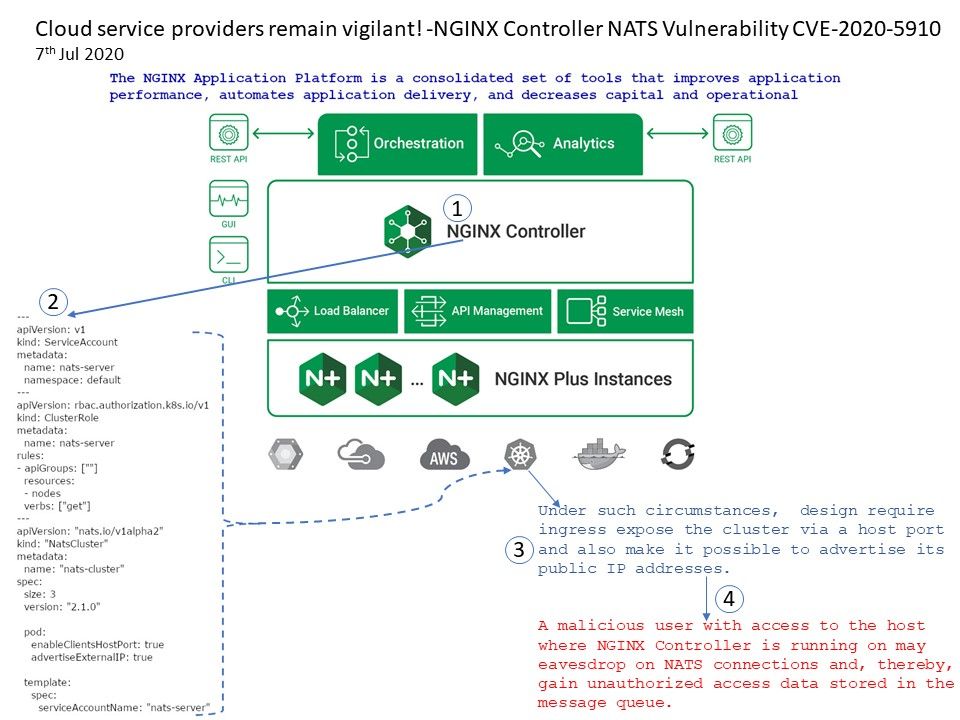
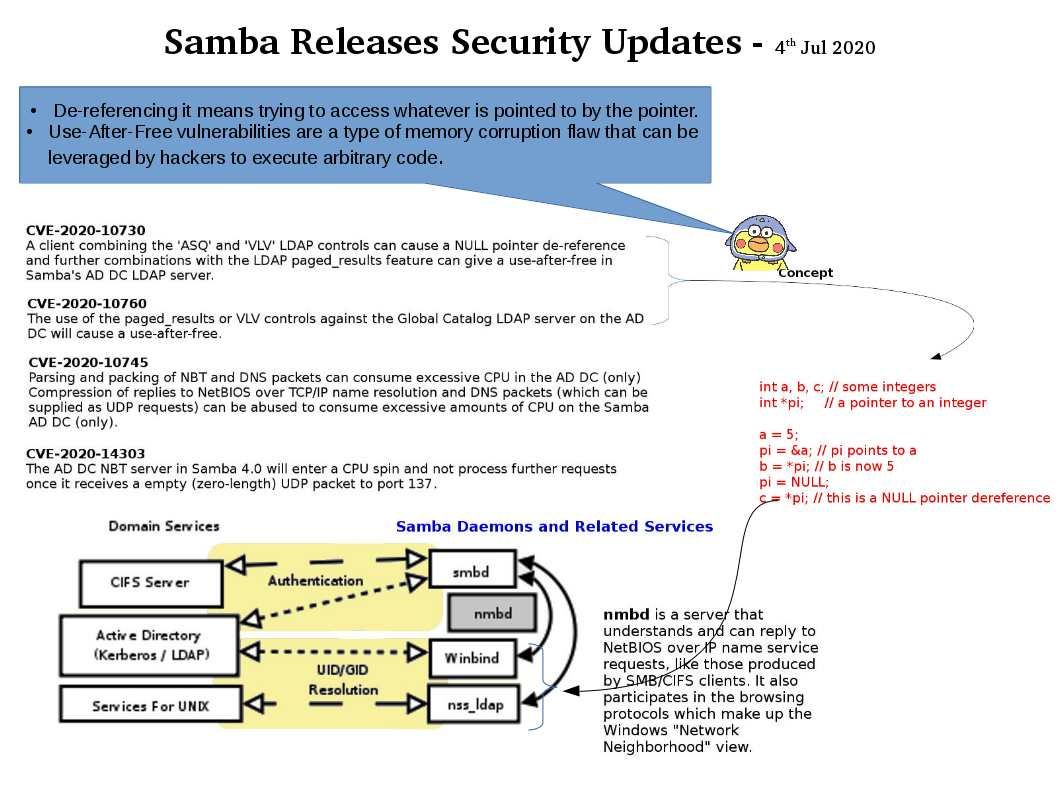

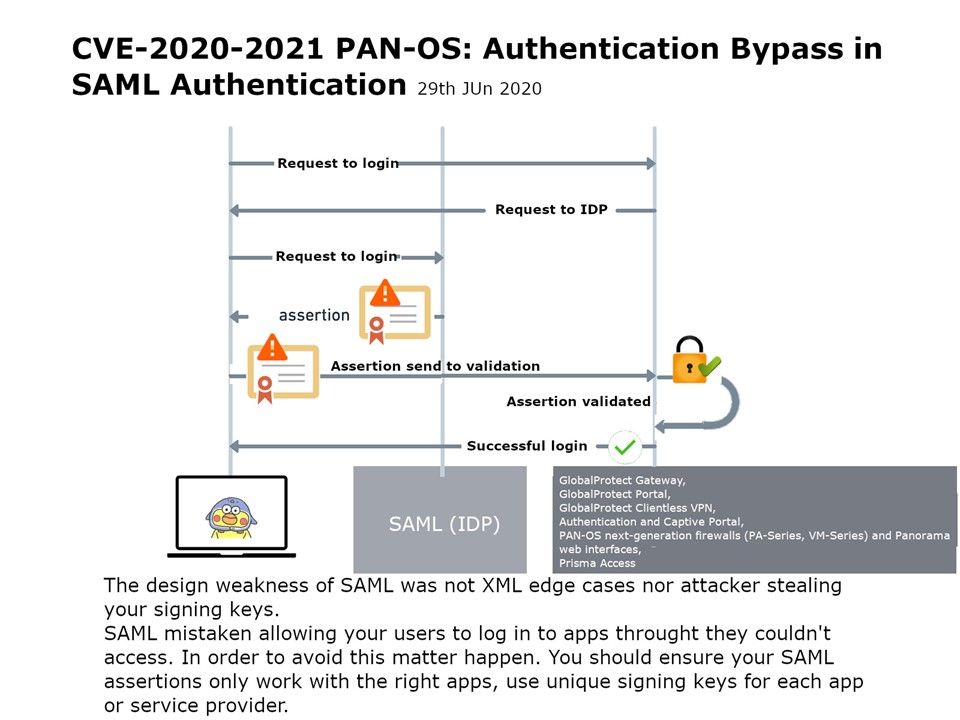
.jpg?width=1920&height=1080&fit=bounds)


.jpg)