Preface: A set of unsafe default configurations for LDAP channel binding and LDAP signing exist on Active Directory domain controllers that let LDAP clients communicate with them without enforcing LDAP channel binding and LDAP signing. This can open Active Directory domain controllers to an elevation of privilege vulnerability, said Microsoft.
Notice: If you are a Samba user, you should remain vigilant. Fix it immediately.
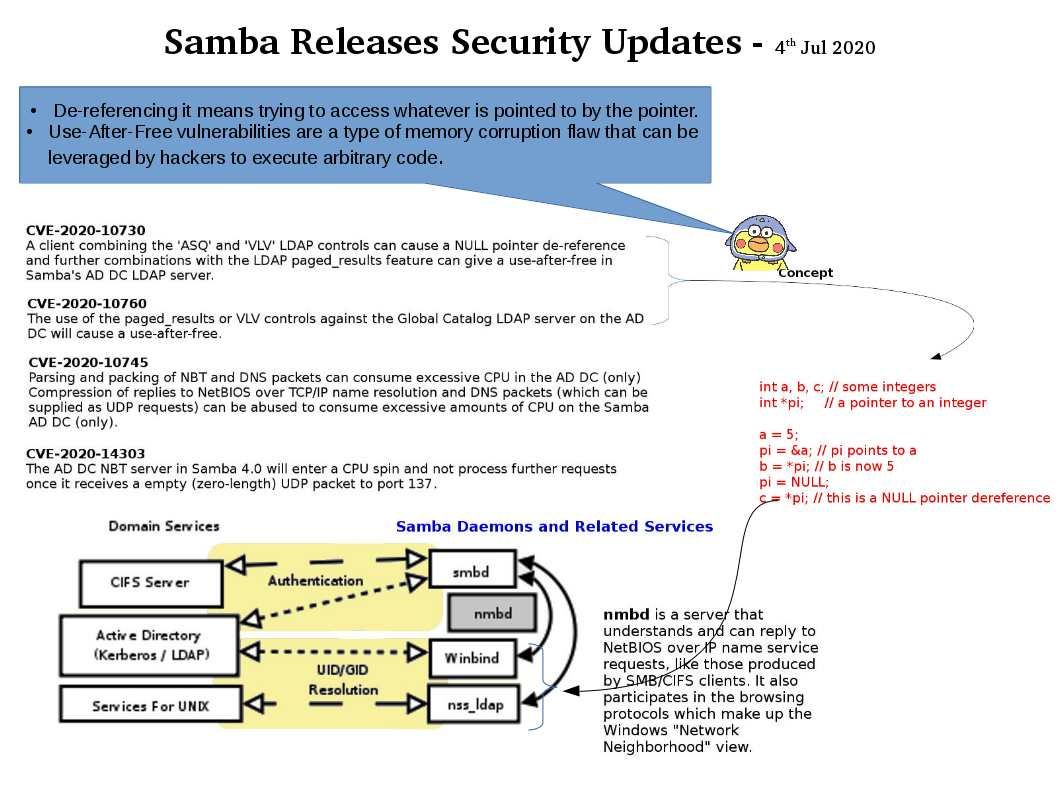
CVE-2020-10730
A client combining the ‘ASQ’ and ‘VLV’ LDAP controls can cause a NULL pointer de-reference and further combinations with the LDAP paged_results feature can give a use-after-free in Samba’s AD DC LDAP server.
https://www.samba.org/samba/security/CVE-2020-10730.html
CVE-2020-10745
Parsing and packing of NBT and DNS packets can consume excessive CPU in the AD DC (only)
Compression of replies to NetBIOS over TCP/IP name resolution and DNS packets (which can be supplied as UDP requests) can be abused to consume excessive amounts of CPU on the Samba AD DC (only).
https://www.samba.org/samba/security/CVE-2020-10745.html
CVE-2020-10760
The use of the paged_results or VLV controls against the Global Catalog LDAP server on the AD DC will cause a use-after-free.
https://www.samba.org/samba/security/CVE-2020-10760.html
CVE-2020-14303
The AD DC NBT server in Samba 4.0 will enter a CPU spin and not process further requests once it receives a empty (zero-length) UDP packet to port 137.
https://www.samba.org/samba/security/CVE-2020-14303.html
Reference:
– De-referencing it means trying to access whatever is pointed to by the pointer.
– Use-After-Free vulnerabilities are a type of memory corruption flaw that can be leveraged by hackers to execute arbitrary code.