Preface: Nginx was written specifically to address the performance limitations of Apache web servers
Background: In March 2019, Nginx Inc was acquired by F5 Networks for US$670 million. According to statistic on 2020. Nginx server deployed by “375 million websites. There are 1,500 paying customers.
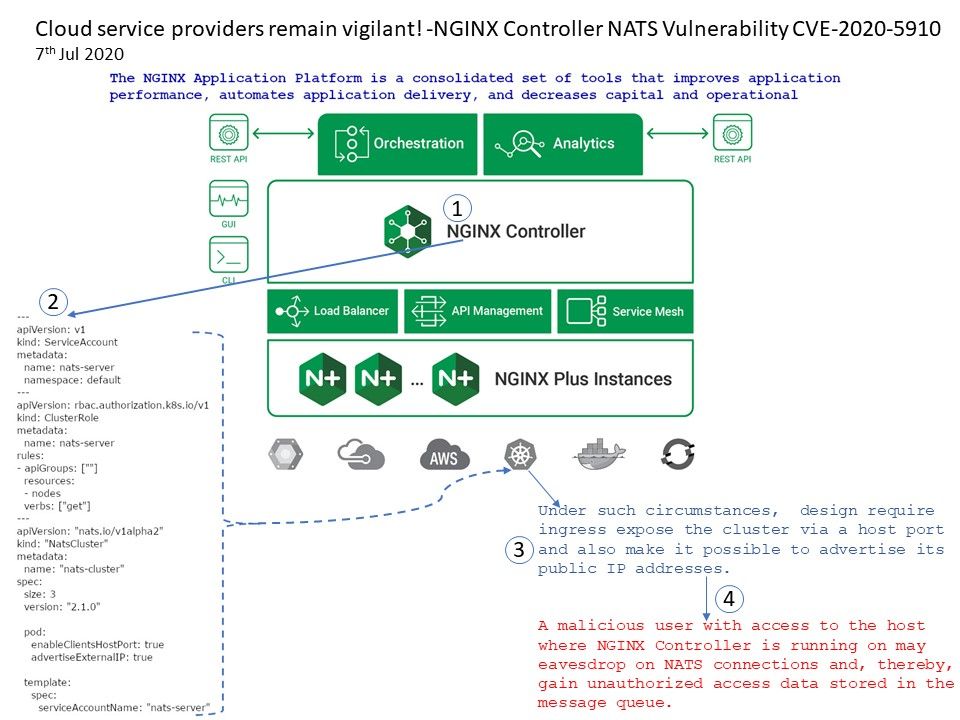
Vulnerability detail : A malicious user with access to the host where NGINX Controller is running on may eavesdrop on NATS connections and, thereby, gain unauthorized access data stored in the message queue. Please refer to the website for details – https://support.f5.com/csp/article/K59209532
Observation: The possible ways to exploit this vulnerability are as follows:
Refer to attached diagram, under such circumstances, design require ingress expose the cluster via a host port and also make it possible to advertise its public ip addresses.
A malicious user with access to the host where NGINX Controller is running on may eavesdrop on NATS connections and, thereby, gain unauthorized access data stored in the message queue.
Remedy: Upgrade to 3.6.0