Preface: Before you start reading. Perhaps below two different url will lure your interest of this article. Please read 1 first, then 2
1:vCenter Server Appliance Web Console (VAMI) is removed from vCenter Server 6.0 – https://kb.vmware.com/s/article/2120477
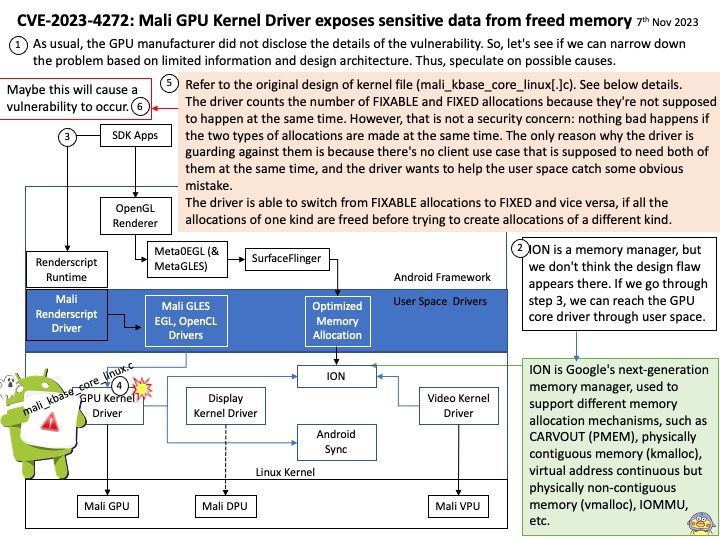
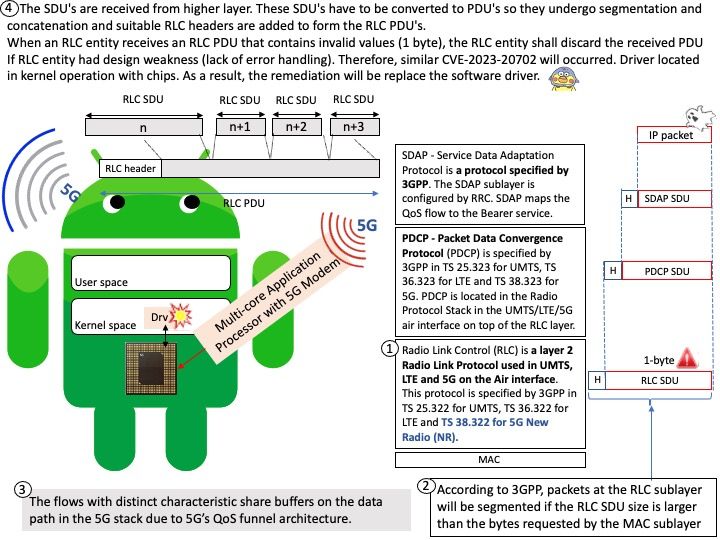
2:Change VCSA 6.7 SSH port – https://communities.vmware.com/t5/VMware-vCenter-Discussions/Change-VCSA-6-7-SSH-port/td-p/1861744
Ref: The vCenter Server appliance is a preconfigured virtual machine that is optimized for running vCenter Server and the associated services. The vCenter Server appliance package contains the following software: Photon OS® 3.0. The vSphere authentication services. PostgreSQL.
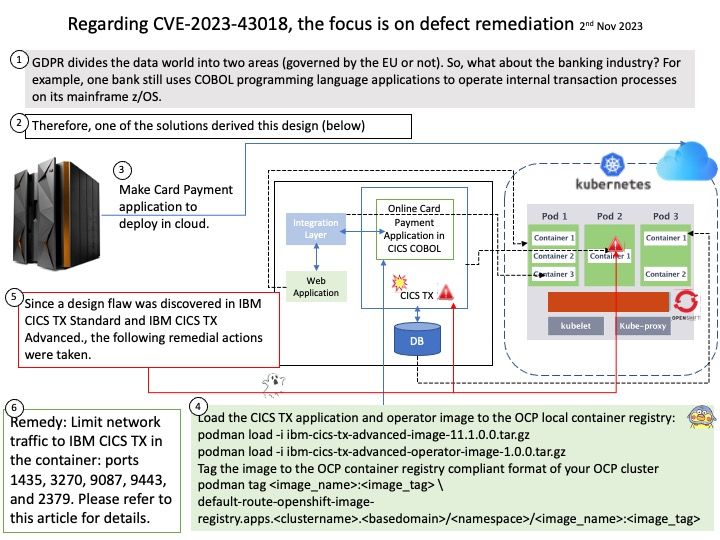
Background: What is the difference between vCenter and vCloud director? A vCenter admin can see virtual data centers, which are logical units for management, a vCloud Director user (tenant) can see only organizational data centers, catalogs, users, and options to manage a virtual organizational data center.
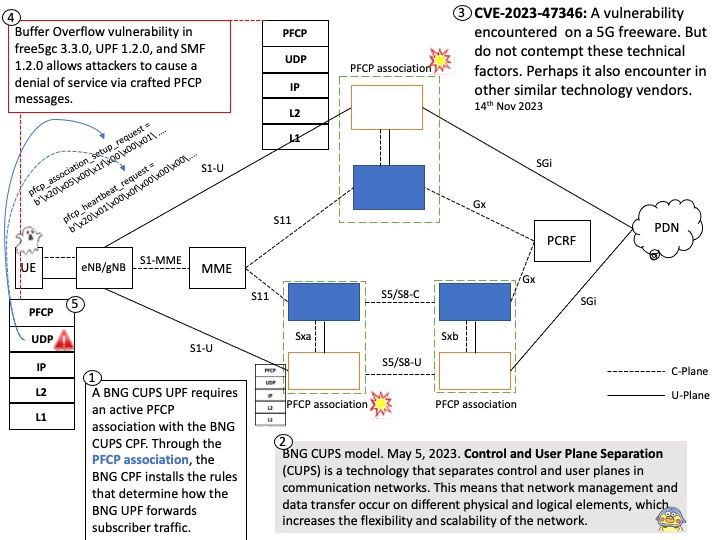
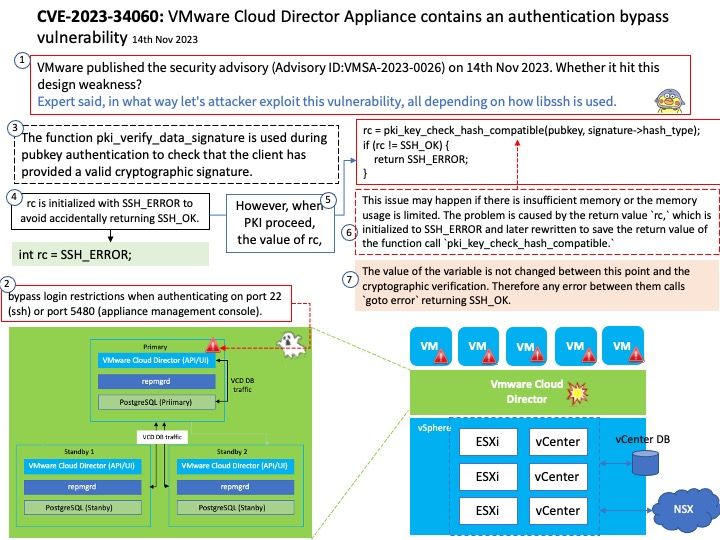
Vulnerability details: VMware Cloud Director Appliance contains an authentication bypass vulnerability in case VMware Cloud Director Appliance was upgraded to 10.5 from an older version. VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9.8.Known Attack Vectors On an upgraded version of VMware Cloud Director Appliance 10.5, a malicious actor with network access to the appliance can bypass login restrictions when authenticating on port 22 (ssh) or port 5480 (appliance management console). This bypass is not present on port 443 (VCD provider and tenant login). On a new installation of VMware Cloud Director Appliance 10.5, the bypass is not present.
Official announcement: Please refer to the link for details –
https://www.vmware.com/security/advisories/VMSA-2023-0026.html