Preface: While ActiveMQ is a traditional message broker, Apache Kafka is a distributed streaming platform designed to handle high-velocity, high-volume, and fault-tolerant data streams. It was originally developed at LinkedIn and later donated to the Apache Software Foundation.
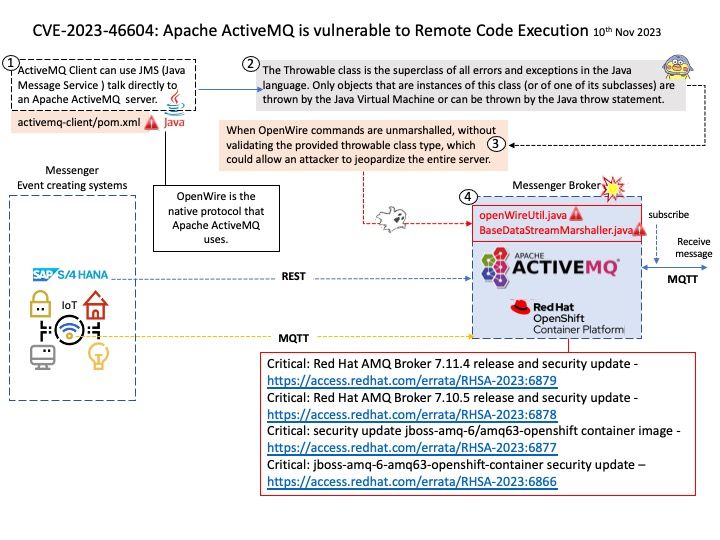
Background: ActiveMQ is open source, message-oriented middleware (MoM). It was written in Java with a full JMS (Java Message Service) client. OpenWire is the native protocol that Apache ActiveMQ uses. Message brokers, like ActiveMQ, can filter and process individual events.
Vulnerability details: Apache ActiveMQ is vulnerable to Remote Code Execution.The vulnerability may allow a remote attacker with network access to a broker to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath.
Remedy: Users are recommended to upgrade to version 5.15.16, 5.16.7, 5.17.6, or 5.18.3, which fixes this issue.
Official announcement: Please refer to the link for details –
https://nvd.nist.gov/vuln/detail/CVE-2023-46604
Critical: Red Hat AMQ Broker 7.11.4 release and security update – https://access.redhat.com/errata/RHSA-2023:6879
Critical: Red Hat AMQ Broker 7.10.5 release and security update – https://access.redhat.com/errata/RHSA-2023:6878
Critical: security update jboss-amq-6/amq63-openshift container image – https://access.redhat.com/errata/RHSA-2023:6877
Critical: jboss-amq-6-amq63-openshift-container security update – https://access.redhat.com/errata/RHSA-2023:6866