Preface: ARM’s Mali GPUs can be found in smartphones from different brands, including Samsung, Xiaomi, and Oppo. Mali GPUs can be seen on MediaTek, HiSilicon Kirin, and Exynos SOCs
Background: When memory is freed, all pointers into it become invalid, and its contents might either be returned to the operating system, making the freed space inaccessible, or remain intact and accessible.
Vulnerability details: A local non-privileged user can make GPU processing operations that expose sensitive data from previously freed memory.
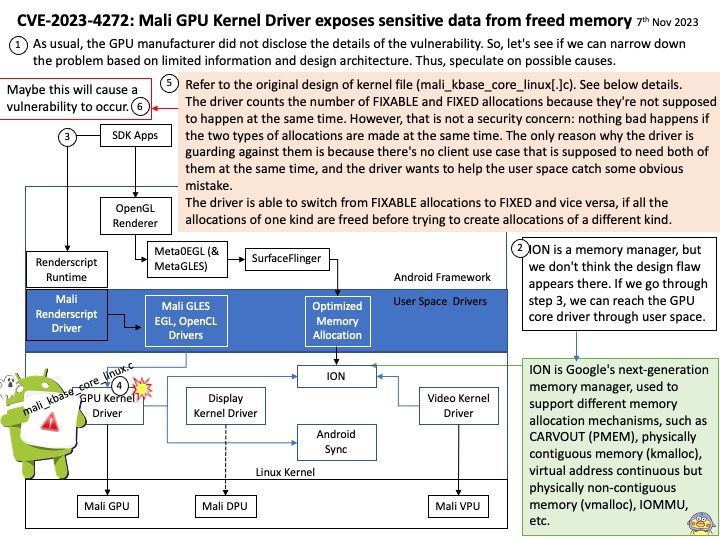
As usual, the GPU manufacturer did not disclose the details of the vulnerability. So, let’s see if we can narrow down the problem based on limited information and design architecture. Thus, speculate on possible causes.
My observations: Refer to the original design of kernel file (mali_kbase_core_linux[.]c). See below details.
The driver counts the number of FIXABLE and FIXED allocations because they’re not supposed to happen at the same time. However, that is not a security concern: nothing bad happens if the two types of allocations are made at the same time. The only reason why the driver is guarding against them is because there’s no client use case that is supposed to need both of them at the same time, and the driver wants to help the user space catch some obvious mistake.
The driver is able to switch from FIXABLE allocations to FIXED and vice versa, if all the allocations of one kind are freed before trying to create allocations of a different kind.
Consequence: Maybe this will cause a vulnerability to occur.
Official announcement: Please refer to the link for details –
https://developer.arm.com/Arm%20Security%20Center/Mali%20GPU%20Driver%20Vulnerabilities