Preface: When we see new vulnerability information posted on forums or NVD. According to market practice, suppliers have provided patches to customers in advance. Maybe they already received the patch earlier (few weeks ago). But a lot of vulnerability items not intend to disclose the details. Perhaps this is the way. It will reduce the attack ratio. But for the people who have interest to know. For sure it will increase the time to conduct the analytic. We believe Artificial Intelligence is powerful. But if it do not have related information. AI also cannot provide a precise the answer.
Background: Oracle EBS applications are delivered from servers, databases, storage, and applications hosted in your local network, on-premises. Why use Oracle EBS? Oracle EBS enables organizations to manage their procurement process, from purchasing to invoicing and payment. Supply chain management. Oracle EBS provides a complete solution for managing the supply chain, including inventory management, order management, and logistics. Human resources.
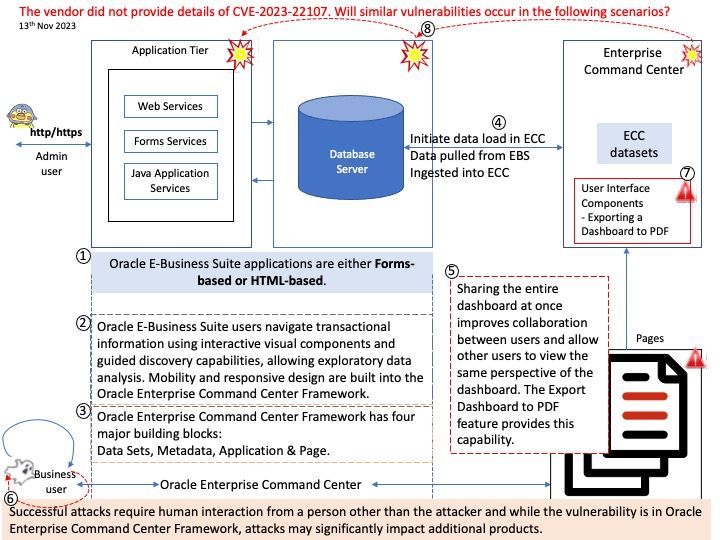
Vulnerability details: Vulnerability in the Oracle Enterprise Command Center Framework product of Oracle E-Business Suite (component: UI Components). Supported versions that are affected are ECC: 8, 9 and 10. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Enterprise Command Center Framework. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Enterprise Command Center Framework, attacks may significantly impact additional products (scope change). Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Enterprise Command Center Framework accessible data as well as unauthorized read access to a subset of Oracle Enterprise Command Center Framework accessible data.
CVSS 3.1 Base Score 6.1 (Confidentiality and Integrity impacts).
CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N).
Remark: The vendor did not provide details of CVE-2023-22107. Will similar vulnerabilities occurs in attached diagram scenarios?
Official announcement: Please refer to the link for details –