Preface: Mojo is a collection of runtime libraries providing a platform-agnostic abstraction of common IPC primitives, a message IDL format
, and a bindings library with code generation for multiple target language to facilitate convenient message passing across arbitrary inter – and intra-process boundaries.
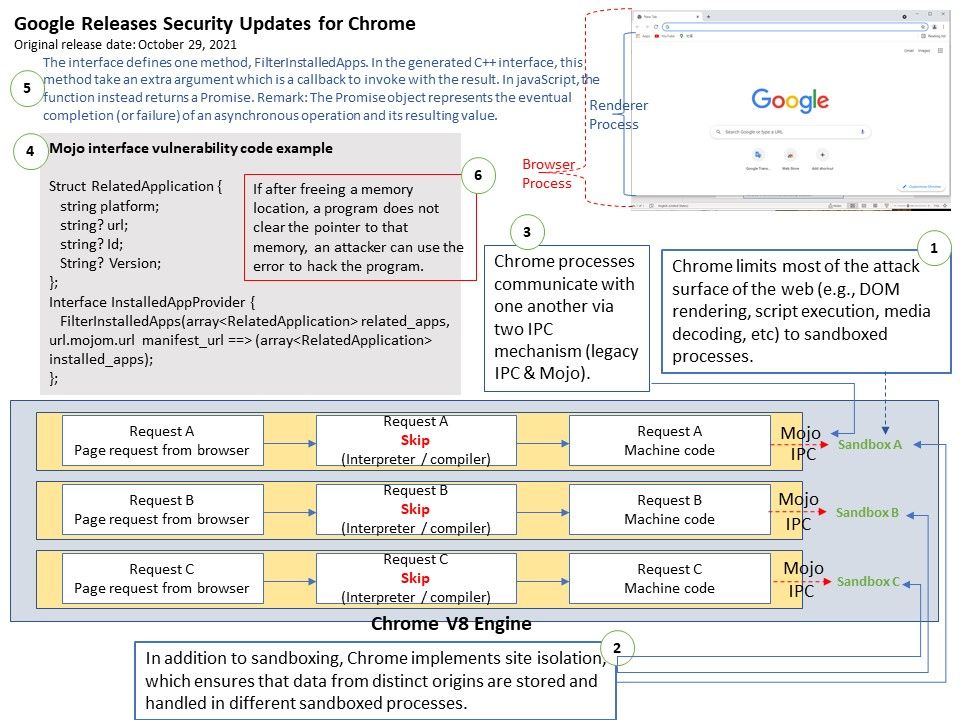
Background:Chrome limits most of the attack surface of the web (e.g., DOM rendering, script execution, media decoding, etc) to sandboxed processes.
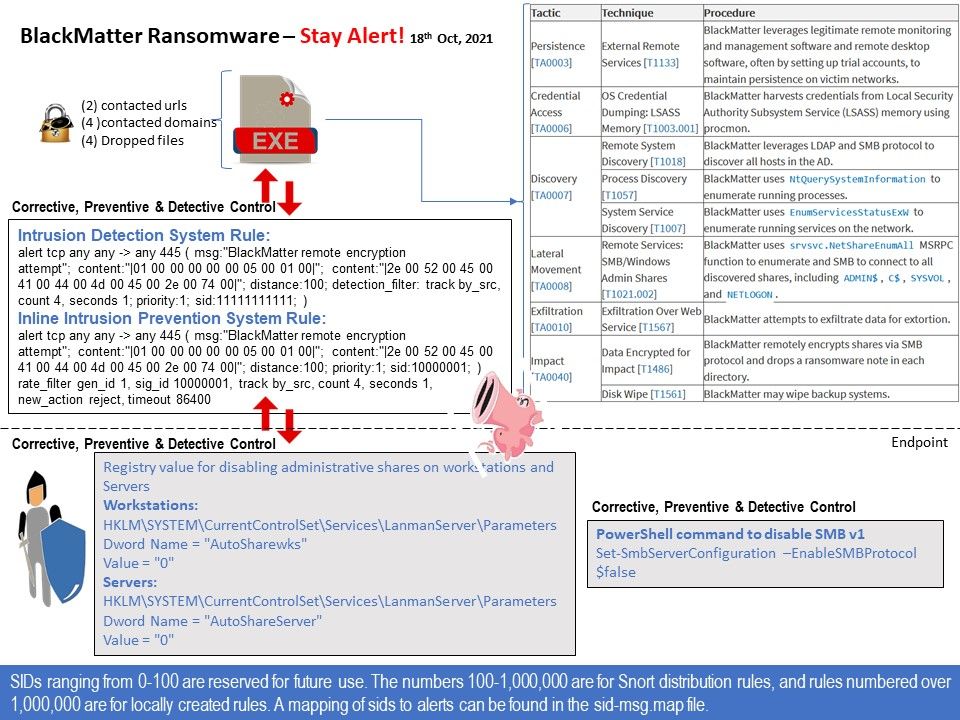
Vulnerability details: Multiple vulnerabilities have been discovered in Google Chrome. Remote attackers can use these vulnerabilities to trigger remote execution of arbitrary code on the target system.
Possibilities: Refer to attached diagram (point 4). The interface defines one method, FilterInstalledApps. In the generated C++ interface, this method take an extra argument which is a callback to invoke with the result. In javaScript, the function instead returns a Promise.
Remark: The Promise object represents the eventual completion (or failure) of an asynchronous operation and its resulting value.
If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program.
Solution: Install the patch provided by the software vendor – https://chromereleases.googleblog.com/2021/10/stable-channel-update-for-desktop_28.html
.jpg)